In the ever-evolving landscape of cybersecurity threats, Pass-the-Hash (PtH) attacks have emerged as a particularly insidious and persistent menace. As digital guardians, it is imperative that we arm ourselves with the knowledge and strategies necessary to combat this threat effectively. In this article, we delve deep into PtH attacks, exploring their intricacies, potential consequences, and most importantly, how to safeguard your digital fortress against them.
Table of Contents
Understanding Pass-the-Hash Attacks
What Exactly is Pass-the-Hash?
Pass-the-Hash attacks are a form of credential theft, where malicious actors aim to compromise user account passwords without ever needing to access the plaintext password. Instead, they target the hashed version of passwords stored on a system. A hash is a mathematical representation of a password, typically a one-way function, making it challenging to reverse-engineer and uncover the original password.
The Anatomy of a PtH Attack
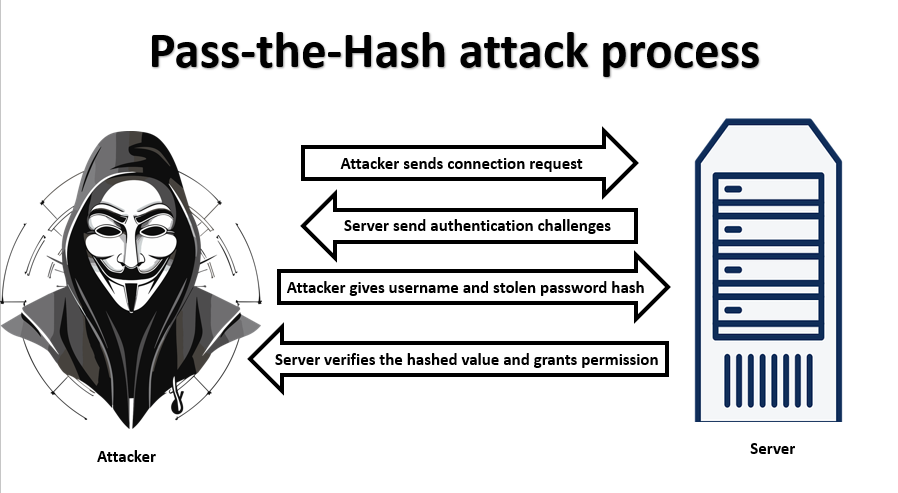
The Pass-the-Hash attack process typically unfolds in the following steps:
1. Obtaining Hashed Passwords: Attackers gain access to the hashed passwords stored on a compromised system or network. This can be achieved through various means, including malware, vulnerabilities, or social engineering.
2. Passing the Hash: Instead of decrypting the hashed password, attackers use it directly to authenticate themselves on a system, service, or network. This allows them to impersonate legitimate users and gain unauthorized access.
3. Privilege Escalation: Once inside, attackers may escalate their privileges, gaining more extensive control over the compromised environment. This can lead to data theft, data manipulation, or further exploitation.
The Threat Landscape
Why are PtH Attacks So Dangerous?
Pass-the-Hash attacks pose a significant threat to organizations and individuals alike due to their stealthy nature and devastating potential. Here’s why they are so dangerous:
1. Stealthy Execution: Pass-the-Hash attacks can go unnoticed for extended periods, as they don’t rely on brute force techniques that trigger alarms. This stealth allows attackers to gather valuable information before detection.
2. Credential Reuse: Attackers can use the obtained hashed passwords across multiple systems or services, magnifying the scope of their compromise. A single successful Pass-the-Hash attack can lead to a widespread breach.
3. Data Theft and Manipulation: Once inside, attackers can exfiltrate sensitive data, manipulate records, or disrupt critical systems. This can result in financial losses, data breaches, and reputational damage.
Mitigating PtH Attacks
Strengthening Your Cybersecurity Arsenal
Protecting against PtH attacks requires a multi-faceted approach that combines robust security practices and cutting-edge technologies:
1. Enhanced Authentication: Incorporate multi-factor authentication (MFA) to introduce an additional layer of security. Even if attackers obtain hashed passwords, they won’t be able to access accounts without the additional authentication factor.
2. Regular Password Updates: Encourage users to change their passwords regularly. This reduces the window of opportunity for attackers to utilize stolen hashed passwords effectively.
3. Privilege Management: Limit user privileges to the minimum required for their roles. This reduces the potential impact of a Pass-the-Hash attack by restricting what attackers can access.
4. Monitoring and Detection: Deploy advanced intrusion detection systems (IDS) and security information and event management (SIEM) solutions to monitor network traffic and detect suspicious activities promptly.
5. Patch Management: Keep systems and software up to date to mitigate vulnerabilities that attackers can exploit.
Pass-the-Hash Attack FAQ
Pass-the-Hash attacks are a complex cybersecurity threat that demands a comprehensive understanding. Below, we provide answers to frequently asked questions about PtH attacks to help you navigate this crucial topic.
What is a Pass-the-Hash Attack?
A Pass-the-Hash attack is a cyberattack method where malicious actors steal hashed passwords from a system and use them to gain unauthorized access to accounts or systems without needing to decipher the plaintext password.
How Does a Pass-the-Hash Attack Work?
In a Pass-the-Hash attack, the attacker first obtains hashed passwords, often by exploiting vulnerabilities or using malware. Instead of cracking the hash to reveal the original password, they directly use the hash to authenticate themselves on a target system, allowing them to impersonate legitimate users.
What Makes PtH Attacks So Dangerous?
Pass-the-Hash attacks are dangerous due to their stealthy nature. They can remain undetected for extended periods, and attackers can use compromised credentials across multiple systems, increasing the potential damage and scope of the breach.
What Are the Consequences of a PtH Attack?
Pass-the-Hash attacks can lead to data theft, data manipulation, privilege escalation, and disruption of critical systems. The consequences can include financial losses, data breaches, and damage to an organization’s reputation.
How Can Organizations Defend Against PtH Attacks?
To defend against Pass-the-Hash attacks, organizations should implement robust security measures, including multi-factor authentication (MFA), regular password updates, privilege management, monitoring and detection systems, and patch management.
Is Pass-the-Hash the Same as Password Cracking?
No, Pass-the-Hash attacks differ from password cracking. In PtH attacks, attackers use the stolen hashed passwords directly for authentication, while password cracking involves attempting to guess or crack the plaintext password.
Can Individuals Protect Themselves from PtH Attacks?
Yes, individuals can enhance their security by using strong, unique passwords for each account, enabling multi-factor authentication where available, and staying vigilant for signs of compromised accounts or unusual activity.
How Can I Detect a PtH Attack?
Detecting PtH attacks requires advanced intrusion detection systems (IDS) and security information and event management (SIEM) solutions. These tools can monitor network traffic and identify suspicious patterns indicative of PtH attacks.
What Should I Do If I Suspect a PtH Attack?
If you suspect a PtH attack, take immediate action by isolating affected systems, changing compromised passwords, and conducting a thorough security audit to identify the extent of the breach. Additionally, report the incident to your organization’s cybersecurity team or authorities.
Is PtH the Only Credential Theft Technique?
No, PtH attacks are one of several credential theft techniques. Others include credential stuffing, keylogging, and phishing. Organizations and individuals must remain vigilant against a range of cyber threats.
Understanding Pass-the-Hash (PtH) attacks is essential in today’s digital landscape. By staying informed and implementing robust security measures, you can protect yourself and your organization from this pervasive cybersecurity threat.
You can follow us on LinkedIn and Twitter for Cloud & Cybersecurity updates.
Also read
Top 10 Active Directory Attacks Methods
Multifactor Authentication: Your Shield Against Cyber Threats


5 thoughts on “Pass-the-Hash Attacks: Strengthening Your Cybersecurity”