Introduction
Domain password guessing is a type of cyberattack where an attacker attempts to gain access to user accounts in a domain by guessing passwords. This can be done manually or using automated tools. Domain password guessing attacks can be very successful, especially if users choose weak or easily guessable passwords. If an attacker gains access to a user account, they can steal sensitive data, install malware, or disrupt operations.
Table of Contents
How does domain password guess work?
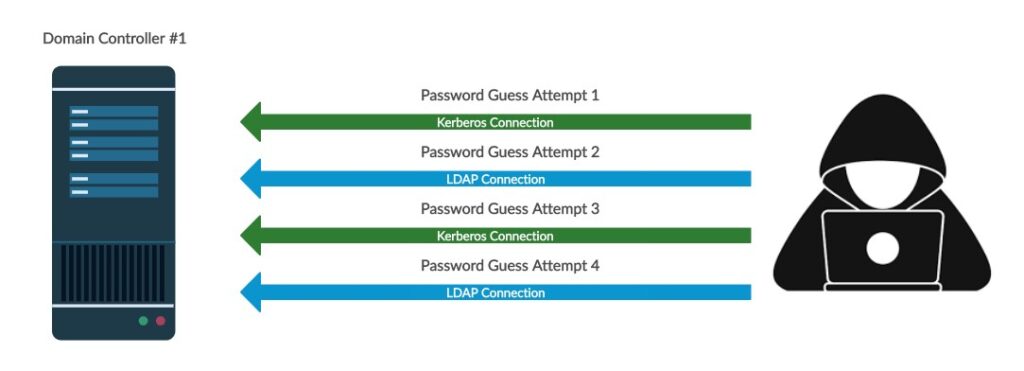
Domain password guessing attacks typically involve the following steps:
1. The attacker gains access to a list of user accounts in the domain. This can be done through a variety of methods, such as social engineering, phishing attacks, or data breaches.
2. The attacker attempts to guess the passwords for the user accounts on the list. This can be done manually or using automated tools.
3. If the attacker is successful in guessing a password, they will gain access to the user account.
What are the risks of domain password guessing?
Domain password-guessing attacks can be very successful, especially if users choose weak or easily guessable passwords. If a malicious actor successfully breaches a user’s account, they have the ability to
• Steal sensitive data, such as customer information, financial data, or intellectual property.
• Install malware, such as ransomware or trojans, on the user’s computer.
• Disrupt operations by disabling or deleting files or systems.
• Escalate privileges and gain access to other systems in the domain.
• Launch attacks against other organizations.
How to protect against domain password guessing
There are a number of things that organizations can do to protect against domain password guessing attacks, including:
- Educate users about password security best practices. Users should be taught to create strong, unique passwords and to change them regularly.
- Implement a password policy. A password policy should require users to create passwords that meet certain criteria, such as minimum length and complexity requirements.
- Enable multi-factor authentication (MFA). MFA adds an extra layer of security to user accounts, making it more difficult for attackers to gain access even if they have the user’s password.
- Use a password manager. A password manager can help users to create and manage strong, unique passwords for all of their accounts.
- Monitor Kerberos ticket requests. Active Directory relies on the Kerberos authentication protocol for its security measures. By monitoring Kerberos ticket requests, you can identify suspicious activity, such as requests for tickets that are not typically used by the user account.
Domain password guessing attack techniques
There are a number of different techniques that attackers can use to carry out domain password guessing attacks, including:
- Brute-force attacks. In a brute-force attack, the attacker tries all possible combinations of characters until they find the correct password. This type of attack can be very slow, but it is effective against weak passwords.
- Dictionary attacks. In a dictionary attack, the attacker tries common words and phrases as passwords. This type of attack is also effective against weak passwords.
- Rainbow table attacks. Rainbow tables are pre-computed tables of hash values for common passwords. Attackers can use rainbow tables to quickly crack passwords that have been hashed using a common algorithm.
- Spray and pray attacks. In a spray and pray attack, the attacker tries the same password against a large number of user accounts. This type of attack is often used to target organizations with weak password policies.
- Pass-the-hash attacks. In a pass-the-hash attack, the attacker steals a user’s password hash and then uses it to authenticate to the user’s account. Pass-the-hash attacks can be successful even if the user’s password is strong.
How to detect domain password guessing attacks
There are a few things that organizations can look for to detect domain password guessing attacks, including:
- Unusual login activity. If an organization notices unusual login activity, such as login attempts from unusual locations or times, it could be a sign of a domain password guessing attack.
- Changes to Kerberos tickets. Organizations can use security monitoring tools to monitor Kerberos tickets for changes. If an attacker creates a new Kerberos ticket, it will show up as a change in the Kerberos ticket database.
- Suspicious activity on the domain controller. Organizations can use security monitoring tools to monitor the domain controller for suspicious activity, such as unauthorized changes to user accounts or permissions.
How to respond to domain password guessing attacks
If an organization detects a domain password guessing attack, it is important to take the following steps:
1. Identify the affected user accounts. Organizations need to identify the user accounts that have been affected by the domain password guessing attack.
2. Change the passwords for the affected user accounts. Organizations need to change the passwords for all of the affected user accounts immediately.
3. Investigate the attack. Organizations need to investigate the attack to determine how the attacker gained access to the list of user accounts and to identify any other systems that may have been affected. This may involve reviewing security logs, interviewing users, and conducting network traffic analysis.
4. Take steps to prevent future attacks. Organizations need to take steps to prevent future domain password guessing attacks, such as:
- Educating users about password security best practices and the importance of using strong, unique passwords
- Implementing a password policy that requires users to create strong, unique passwords and to change them regularly
- Enabling multi-factor authentication (MFA) for all user accounts.
- Using a password manager to help users create and manage strong, unique passwords
- Monitoring Kerberos ticket requests for suspicious activity.
- Implementing security controls to prevent attackers from gaining access to the list of user accounts in the domain
You can follow us on LinkedIn and Twitter for Cloud & Cybersecurity updates.
Also read..
Kerberoasting Attack: A Cybersecurity Threat
Top 10 Active Directory Attacks Methods
Pass-the-Hash Attacks: Strengthening Your Cybersecurity
Golden Ticket Attack: How to Defend Your Castle
Password Spraying: A Comprehensive Guide to Protecting Your Digital World
Pass-the-Ticket Attack: A Persistent Threat to System Integrity