In today’s world, where everything is becoming digital and the internet is everywhere, it’s super important to keep our online stuff safe. You know, like our accounts, emails, and personal information. But guess what? Bad people out there are always trying to steal this stuff! That’s where multi-factor authentication (MFA) comes into the picture.
Table of Contents
Introduction to Multi-Factor Authentication (MFA)
Multi-Factor Authentication, often abbreviated as MFA or known as Two-Factor Authentication (2FA), is a multifaceted security mechanism that mandates users to authenticate their identity through two or more distinct means before gaining access to an online account or system. This added layer of security is instrumental in thwarting the nefarious designs of cybercriminals seeking unauthorized entry.
Types of Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) is a versatile security approach that incorporates multiple forms of verification to confirm a user’s identity. These verification factors fall into three primary categories, and different types of MFA can combine factors from these categories to enhance security. Here are the most common types of MFA:
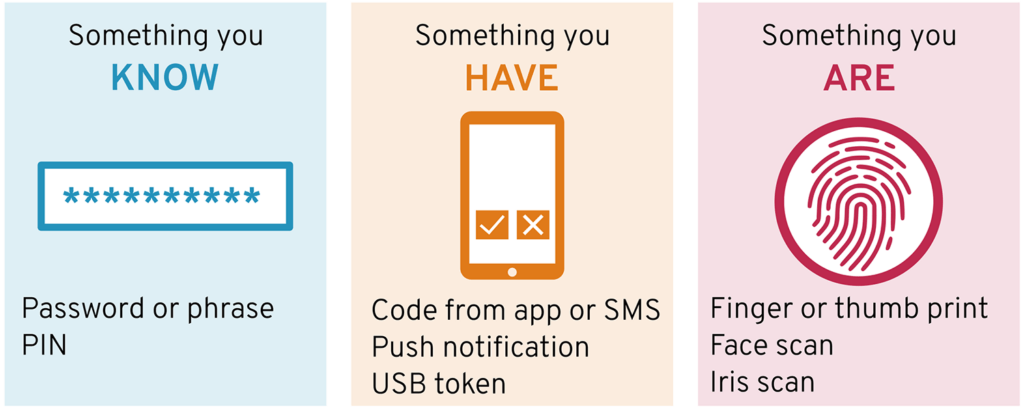
1. Something You Know:
Password: The most common type of authentication requires users to enter a secret password known only to them.
Personal Identification Number (PIN): Similar to a password but typically shorter, often used with smart cards or mobile devices.
Security Questions: Users answer predefined security questions that only they should know, such as their mother’s maiden name or the name of their first pet.
Pattern Unlock: Typically used on touchscreens, users draw a specific pattern to unlock their device.
2. Something You Have:
Mobile App Authentication: Users receive a one-time code or push notification on their mobile device via an authenticator app. They must approve or enter the code to gain access.
Security Token: A physical device that generates a time-sensitive code that the user enters along with their password. Tokens can be hardware-based or software-based.
Smart Card: A physical card with an embedded chip that contains authentication data. Users insert the card into a card reader to authenticate.
Email or SMS Codes: Users receive a one-time code through email or SMS, which they must enter to access their account.
Biometric Authentication: Users rely on unique biological traits, such as fingerprints, facial recognition, or retina scans, to gain access.
3. Something You Are (Biometric):
Fingerprint Recognition: scanning and verifying the user’s fingerprint to grant access
Facial Recognition: Analyzing and matching the user’s facial features to a stored template
Retina Scans: Examining the unique patterns in the user’s retina for authentication
Voice Recognition: Analyzing the user’s voice characteristics and patterns
Iris Recognition: scanning and comparing the unique patterns in the user’s iris
Behavioral Biometrics: Analyzing user behavior, such as typing speed or mouse movements, to verify identity.
4. Somewhere You Are:
Geolocation: Confirming the user’s location through their device’s GPS or IP address. Access may be granted or denied based on predefined geographic boundaries.
Network Location: Authenticating based on the user’s connection to a specific network or domain, such as a corporate network or VPN.
Physical Access Control: Using physical access methods like key cards or access badges to gain entry to a secure location
5. Something You Do:
Keystroke Dynamics: Analyzing typing patterns and speed to verify the user’s identity
Gesture Recognition: Confirming identity through specific gestures or movements, often used in combination with touchscreens or motion-sensing devices.
Behavioral Authentication: Assessing user behavior, such as patterns of activity, to detect anomalies and identify potential threats.
6. Time-Based Authentication: Time-Based One-Time Password (TOTP): Users receive a time-sensitive code, often valid for 30 seconds, generated by an authenticator app or token
The Myriad Benefits of MFA
The advantages of adopting Multi-Factor Authentication are multifarious and extend to various aspects of security and digital access:
1. Elevated Security: MFAsignificantly augments security by reducing the vulnerability to unauthorized access. Even if malevolent actors manage to lay their hands on your password, they would still need to surmount the hurdle posed by the second authentication factor, a task that is considerably more challenging.
2. Phishing Resilience: Phishing attacks often employ cunning strategies to deceive users into disclosing their passwords. MFA serves as a robust countermeasure, as attackers would still require the secondary authentication factor, which is typically not susceptible to phishing attacks.
3. Safeguarding Sensitive Data: Particularly in the realm of businesses and organizations handling sensitive customer data or financial information, MFA serves as a vital bulwark against data breaches. It adds an additional layer of security, ensuring that only authorized individuals can gain access to confidential data.
4. Compliance Conformity: Numerous industries and regulatory bodies mandate the implementation of MFA as an integral component of their cybersecurity protocols. Adhering to these stipulations helps organizations avoid regulatory penalties and mitigate potential damage to their reputation.
Implementing Multi-Factor Authentication
Embarking on the journey to implement Multi-Factor Authentication within your digital ecosystem is a prudent and responsible course of action. Here are the key steps to initiate this process:
1. Selection of Authentication Factors: Determine which authentication factors are most suited to your organization’s specific requirements. Typically, a combination of something you know (e.g., password) and something you have (e.g., smartphone or security token) is recommended.
2. Choose MFA Solutions: Survey the landscape of MFA solutions and tools available in the market to ascertain the ones that align with your organization’s needs and goals. Many popular online services, including Google, Microsoft, and various social media platforms, offer built-in MFA options that can be readily utilized.
3. User Education and Training: Effective user education and training are pivotal to the successful implementation of MFA. It is imperative to communicate to your employees or users the significance of MFA and provide clear, step-by-step instructions on how to set it up. Equipping users with the knowledge and support they need ensures a smooth transition to this enhanced security paradigm.
4. Testing and Continuous Monitoring: After implementing MFA, it is essential to conduct regular testing to verify that the setup functions as intended. Additionally, establish a robust system for continuous monitoring of user activities, promptly responding to security alerts and anomalies.
FAQs
1. What is Multi-Factor Authentication (MFA)?
Multi-Factor Authentication (MFA) represents a security approach that mandates users to furnish two or more types of verification before obtaining entry to an online account or system. It introduces an additional tier of security that extends beyond the use of a password alone.
2. Why is MFA important?
Multi-Factor Authentication (MFA) holds immense importance due to its capacity to substantially elevate security levels. It serves as a formidable safeguard, effectively shielding your accounts against unauthorized access, even in situations where your password may have been compromised.
3. How does MFA work?
MFA typically involves three categories of authentication factors: something you know (like a password), something you have (like a smartphone), and something you are (like a fingerprint). Users must provide at least two of these factors to authenticate.
4. What are the benefits of using MFA?
MFA offers several benefits, including:
Enhanced security against cyber threats.
Protection against phishing attacks.
Safeguarding sensitive data.
Compliance with regulatory requirements.
5. Is MFA difficult to set up?
Setting up MFA is usually straightforward. Many online services and platforms offer MFA options, and the setup process is user-friendly. It may require installing an authenticator app or registering a device.
6. Can I use MFA on my smartphone?
Yes, MFA can be set up on your smartphone. You can receive one-time codes or push notifications through an authenticator app to verify your identity.
7. What if I lose my MFA device, like my smartphone or security token?
Losing your MFA device can be a concern. It’s essential to have backup methods in place, such as backup codes or alternative authentication factors. Contact your service provider to regain access.
8. Is MFA the same as Two-Factor Authentication (2FA)?
MFA and 2FA are similar but not identical. 2FA is a subset of MFA and specifically involves two factors of authentication. MFA can include more than two factors for added security.
9. Are biometrics like fingerprint or facial recognition safe for MFA?
Biometrics, when properly implemented, can be very secure for MFA. They offer unique identifiers that are challenging to replicate. However, it’s essential to use secure and well designed biometric systems.
10. Can I use MFA for all my online accounts?
While not all online services support MFA, many popular ones do. It’s highly recommended to enable MFA wherever possible, especially for accounts containing sensitive information.
11. Can I turn off MFA if I no longer want to use it?
Yes, you can typically disable MFA if you no longer wish to use it. However, it’s advisable to maintain MFA for enhanced security, especially for critical accounts.
12. Is MFA foolproof?
While MFA significantly improves security, it is not entirely foolproof. No security measure is. However, it greatly reduces the risk of unauthorized access and should be an essential part of your cybersecurity strategy. Know more about common attack click here
13. Is MFA only for businesses, or can individuals use it too?
Individuals can and should use MFA as well. It’s not exclusive to businesses. Protecting your personal online accounts with MFA is a wise step to enhance your digital security.
14. Does MFA slow down the login process?
MFA may add a few seconds to the login process as you need to provide additional authentication. However, the added security outweighs the minor inconvenience of a slightly longer login time
15. What should I do if I suspect someone has accessed my account despite MFA?
If you have concerns about unauthorized access, it’s essential to take prompt action. Begin by changing your password without delay, and then get in touch with your service provider. They are equipped to assist you in fortifying your account’s security and initiating an inquiry into any questionable or suspicious activities.
Multi-Factor Authentication is a robust security measure that everyone should consider implementing to protect their digital presence. It’s a powerful tool in the fight against cyber threats and unauthorized access to online accounts and sensitive information.
