In today’s digital landscape, where threats to cybersecurity are constantly evolving, traditional security models are no longer sufficient to protect sensitive data and systems. As organizations embrace cloud computing, remote work, and an increasingly interconnected environment, the attack surface grows wider, making it crucial to adopt a more robust security strategy. This is where Zero Trust comes into play—a modern security paradigm designed to mitigate risks by eliminating the concept of inherent trust.
In this post, we’ll explore the basics of Zero Trust, its core principles, and best practice frameworks that can help organizations build stronger, more resilient security postures.
Table of Contents
What is Zero Trust?
Zero Trust is a security model that operates under the assumption that no entity, whether inside or outside the network, can be trusted by default. Every request, whether coming from a user, device, or application, must be authenticated, authorized, and continuously validated before access is granted to critical resources. The motto of Zero Trust is “never trust, always verify.”
This approach significantly reduces the risk of data breaches and lateral movement within networks by minimizing the reliance on perimeter defenses and focusing on enforcing strict access controls.
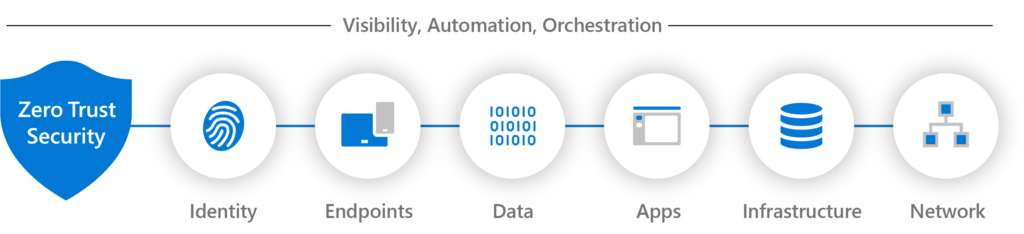
Core Principles of Zero Trust
The Zero Trust model is built upon several key principles:
1. Verify Explicitly: Every request must be authenticated and authorized based on all available data points, such as user identity, device health, and location, regardless of its origin. Identity-based access controls are fundamental in this step.
2. Use Least Privilege Access: Limit users and systems to only the minimum levels of access required to perform their tasks. This principle minimizes the potential damage caused by compromised accounts or systems.
3. Assume Breach: Continuously monitor and analyze all activities, assuming that breaches will happen. Implement systems for threat detection, response, and recovery to mitigate the impact of a successful attack.
4. Segmentation: Divide the network into smaller, isolated zones. This helps prevent unauthorized lateral movement within the environment by limiting attackers’ ability to access other parts of the network.
5. End-to-End Encryption: Ensure that data is encrypted both at rest and in transit, which helps protect sensitive information even if attackers manage to intercept it.
6. Continuous Monitoring and Analytics: Use real-time monitoring, threat intelligence, and behavior analysis to detect anomalies and suspicious activities quickly.
Best Practice Frameworks for Zero Trust
While Zero Trust is a broad and flexible concept, several frameworks and guidelines have emerged to help organizations implement it effectively. These frameworks provide practical steps and industry-standard practices for adopting a Zero Trust model. Some key frameworks include:
1. NIST Zero Trust Architecture (SP 800-207)
The National Institute of Standards and Technology (NIST) published the SP 800-207. Zero Trust Architecture as a detailed guideline for implementing Zero Trust in an organization. It outlines how to apply Zero Trust principles to enterprise systems and provides a conceptual architecture that includes policy enforcement, data flows, and continuous monitoring.
Key Components of NIST Zero Trust:
– Policy Engine: Decides whether to grant or deny access.
– Policy Administrator: Enforces the decisions made by the policy engine.
– Policy Enforcement Points (PEP): Controls access to resources based on established policies.
2. Microsoft Zero Trust Framework
Microsoft’s Zero Trust approach focuses on securing identities, endpoints, networks, and applications. It emphasizes three core strategies: explicit verification, least privileged access, and assuming breach. Microsoft also highlights the importance of using AI and automation to detect threats faster and respond more efficiently.
Microsoft’s Zero Trust framework can be broken down into six pillars:
– Identities: Secure access with strong authentication methods like multifactor authentication (MFA) and adaptive policies.
– Devices: Ensure that all devices accessing corporate resources are compliant and monitored.
– Applications: Secure application access by enabling least privileged permissions.
– Data: Classify, encrypt, and enforce data protection policies across the board.
– Infrastructure: Monitor infrastructure security, especially in hybrid cloud environments.
– Network: Segment the network and encrypt data, monitoring for any unusual activities.
3. Google BeyondCorp
Google’s BeyondCorp is one of the earliest and most well-known Zero Trust models. It focuses on enabling secure access to enterprise resources without relying on a traditional network perimeter. BeyondCorp shifts access decisions from network locations to individual user and device identities, ensuring that employees can securely access internal applications from any location without needing a VPN.
Key Practices of BeyondCorp:
– Device-based access control
– Context-aware access based on user identity and device health
– Use of internal certificates for secure communications
4. CISA Zero Trust Maturity Model
The Cybersecurity and Infrastructure Security Agency (CISA) provides a Zero Trust Maturity Model, which is designed to help federal agencies adopt Zero Trust strategies incrementally. This model lays out different stages—Traditional, Initial, Advanced, and Optimal—allowing organizations to evaluate their current state and plan their progression toward full Zero Trust implementation. click here to know more.
Stages of Maturity:
– Traditional: Relies on perimeter security and limited visibility into activities.
– Initial: Starts adopting identity-based access controls and monitoring capabilities.
– Advanced: Applies Zero Trust principles across the organization, including automation.
– Optimal: Fully mature Zero Trust environment, with proactive threat detection and real-time response.
Steps to Implement Zero Trust
Adopting Zero Trust may seem like a daunting task, but organizations can follow these steps to make the transition smoother:
1. Assess Current Security Posture: Start by evaluating your existing security framework and identifying vulnerabilities that Zero Trust can address.
2. Prioritize Critical Assets: Determine which assets, data, and applications are most critical to the organization and apply Zero Trust principles to these first.
3. Implement Identity and Access Management (IAM): Ensure strong authentication mechanisms are in place, such as multifactor authentication (MFA), and adopt least privileged access. To learn more about IAM.
4. Micro-Segmentation: Use network segmentation to isolate different zones and limit lateral movement.
5. Monitor and Respond: Deploy tools that provide continuous monitoring, behavior analysis, and anomaly detection, ensuring that suspicious activities are detected early.
6. Automate Security Policies: Leverage AI and machine learning to automate policy enforcement and respond to threats in real-time.
Conclusion
As the cyber threat landscape evolves, traditional perimeter-based security models can no longer keep up with the increasing complexity of attacks. Zero Trust offers a more flexible and robust solution, ensuring that every access request is scrutinized, and no one is trusted by default.
By adopting Zero Trust frameworks such as NIST SP 800-207, Microsoft’s Zero Trust framework, and Google’s BeyondCorp, organizations can protect their most valuable assets and data in a cloud-first, hybrid work environment. Starting with strong identity management, continuous monitoring, and least privileged access will set the foundation for a more secure, resilient organization.
Ready to start your Zero Trust journey? Implementing a Zero Trust architecture might require a cultural and operational shift, but the benefits—protection against modern threats and enhanced security—are well worth the investment.

