Welcome to Day 4 of 30 Days of Azure Security! Over the past few days, we’ve laid a strong foundation for understanding Azure’s robust security ecosystem. Today, we dive into Zero Trust Architecture in Azure, one of the most transformative frameworks shaping modern cloud security.
As traditional network perimeters dissolve and cyber threats grow more advanced, the Zero Trust model has become a cornerstone of secure cloud practices. This approach challenges the conventional “trust but verify” mindset by assuming that no user, device, or system—whether internal or external—can be inherently trusted. Instead, every access request is rigorously authenticated and authorized, ensuring the highest level of security for your Azure environment.
According to the 2023 Verizon Data Breach Report, insider threats and lateral movement within networks are major contributors to security breaches. Zero Trust directly counters these vulnerabilities by prioritizing continuous verification, least privilege access, and the assumption of breach.
In this post, we’ll explore Zero Trust Architecture in Azure, examining its principles, key components, and how Azure’s native tools empower organizations to implement this model effectively. For cloud security engineers, embracing Zero Trust isn’t just a best practice—it’s an essential strategy for navigating today’s threat landscape. Let’s explore how Zero Trust can redefine security in Azure environments!
Table of Contents
What is Zero Trust Architecture in Azure?
The Zero Trust model is a paradigm shift in cybersecurity, emphasizing that organizations should “never trust, always verify”—even when the request originates from within the network. Unlike traditional security models that rely heavily on perimeter-based defenses, Zero Trust assumes that threats can exist both inside and outside the network.
This framework aligns perfectly with the modern hybrid and multi-cloud ecosystems, where users, devices, and workloads are distributed across diverse locations. Azure, with its robust security capabilities, offers a comprehensive toolkit to build and maintain a Zero Trust environment.
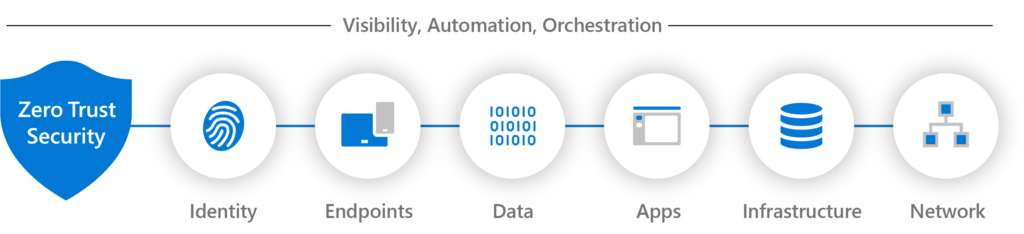
Core Principles of Zero Trust in Azure
Verify Explicitly
Always authenticate and authorize every user, device, and connection based on multiple data points, including identity, location, device health, and anomaly detection.
- Azure Tools: Azure Active Directory (AAD), Conditional Access policies, Multi-Factor Authentication (MFA).
Use Least Privilege Access
Restrict access rights for users, applications, and resources to the bare minimum required for their roles and responsibilities.
- Azure Tools: Role-Based Access Control (RBAC), Just-In-Time (JIT) VM access, Privileged Identity Management (PIM).
Assume Breach
Design your network and security strategies assuming that breaches will occur. Prioritize rapid detection, containment, and recovery.
- Azure Tools: Microsoft Defender for Cloud, Azure Sentinel, Network Security Groups (NSGs), and Application Security Groups (ASGs).
Implementing Zero Trust in Azure: A Step-by-Step Guide
Strengthen Identity Security
Identity is the foundation of Zero Trust. Compromised credentials remain a primary attack vector in modern breaches. Azure Active Directory (AAD) offers comprehensive identity security features:
- Enforce Conditional Access Policies: Define granular access rules based on signals like user location, device compliance, and risk levels.
- Enable Multi-Factor Authentication (MFA): Use MFA to ensure users authenticate using multiple methods, such as passwords and biometrics.
- Leverage Azure AD Identity Protection: Monitor and respond to identity-based threats using machine learning and risk-based policies.
Protect Devices
Securing endpoints is critical to prevent unauthorized access to cloud resources. Azure offers robust tools for endpoint protection and monitoring:
- Integrate Microsoft Defender for Endpoint: Gain insights into device health, vulnerabilities, and threats.
- Use Intune for Device Management: Enforce compliance policies and ensure devices meet security baselines.
- Implement Endpoint Detection and Response (EDR): Actively monitor endpoints for malicious activities.
Secure Access to Applications
Azure provides mechanisms to protect both SaaS and custom applications using Zero Trust principles:
- Use Azure AD App Proxy: Enable secure access to on-premises applications without exposing them to the internet.
- Implement Single Sign-On (SSO): Simplify user authentication and reduce password sprawl.
- Adopt Application Gateway and WAF: Protect web applications from common threats like SQL injection and cross-site scripting (XSS).
Safeguard Data
Data protection is a cornerstone of Zero Trust. In Azure, data security involves encryption, monitoring, and access control:
- Encrypt Data at Rest and in Transit: Use Azure Disk Encryption, Transparent Data Encryption (TDE), and Secure Socket Layer (SSL).
- Classify and Label Data: Leverage Azure Information Protection (AIP) to classify and protect sensitive data.
- Monitor Data Access Patterns: Use Azure Monitor and Microsoft Defender for SQL to track anomalies in data usage.
Segment the Network
Network segmentation minimizes the blast radius of an attack and enforces granular access policies:
- Define Micro-Segmentation Policies: Use NSGs and ASGs to control traffic flow between resources.
- Implement Azure Firewall: Establish a robust perimeter for your Azure environment with deep packet inspection and threat intelligence.
- Adopt Virtual Network (VNet) Peering: Secure connections between VNets without exposing traffic to the public internet.
Enable Advanced Threat Detection
Detecting and responding to threats in real-time is crucial to a Zero Trust approach:
- Use Microsoft Defender for Cloud: Gain a unified view of your security posture and recommendations for improvement.
- Deploy Azure Sentinel: Employ SIEM capabilities to analyze logs and detect sophisticated threats.
- Leverage Threat Intelligence: Enrich detection rules with global threat intelligence feeds.
Zero Trust Architecture: Real-World Use Case in Azure
Let’s consider a hypothetical organization, SecureNet Corp, transitioning to Zero Trust in Azure.
- Challenge: Employees often access sensitive workloads from personal devices. Unauthorized applications have also been discovered on corporate devices.
- Solution Implementation:
- SecureNet uses Conditional Access policies to allow access only from compliant and corporate-managed devices.
- Employees authenticate via MFA, and application access is streamlined with SSO.
- All devices are onboarded to Intune for compliance management, and Microsoft Defender for Endpoint ensures real-time protection.
- Outcome: SecureNet achieves a 60% reduction in credential-based attacks and a significant improvement in data governance and visibility.
Benefits of Adopting Zero Trust in Azure
- Enhanced Security Posture: Minimized attack surfaces and proactive threat detection capabilities.
- Regulatory Compliance: Simplified adherence to standards like GDPR, HIPAA, and ISO 27001.
- Operational Efficiency: Centralized policies and automation reduce the burden on IT teams.
- Resilience Against Insider Threats: Comprehensive monitoring and segmentation limit the impact of compromised accounts.
Best Practices for Zero Trust Implementation
- Start Small and Scale Gradually: Focus on critical assets first, then extend Zero Trust principles across the environment.
- Continuously Monitor and Adapt: Leverage Azure Monitor and Sentinel for ongoing assessments and updates.
- Educate Stakeholders: Ensure employees and administrators understand Zero Trust concepts and their role in maintaining security.
- Leverage Automation: Use tools like Azure Policy to automate enforcement of security best practices.
Challenges in Adopting Zero Trust
While the benefits are clear, adopting Zero Trust can be challenging:
- Cultural Resistance: Transitioning from a traditional security model requires significant organizational buy-in.
- Complexity: Integrating tools and policies across a hybrid or multi-cloud environment demands careful planning.
- Cost: Initial setup may require investment in new tools and training.
Azure mitigates these challenges by offering a comprehensive suite of integrated tools that streamline Zero Trust implementation.
Conclusion
Zero Trust Architecture represents the future of cloud security. By leveraging Azure’s extensive security features, organizations can adopt this model to safeguard their hybrid and multi-cloud environments. As a Cloud Security Engineer or Cyber Security Engineer, your role in driving Zero Trust adoption will be pivotal in enabling secure and resilient operations.
In tomorrow’s post, we’ll explore Understanding Conditional Access in Azure AD, where we’ll demonstrate how to configure and enforce policies to secure access to resources effectively.
Stay tuned for more insights in our 30 Days of Azure Security series!

