Welcome to Day 5 of our 30 Days of Azure Security blog series! Today, we’ll explore Conditional Access in Entra ID (formerly Azure Active Directory), a cornerstone of securing modern cloud environments. Designed to help enforce security policies dynamically, Conditional Access ensures that the right people have the right access under the right conditions—without compromising usability.
In this post, we will:
- Define Conditional Access and its core concepts.
- Explore use cases and benefits.
- Walk through creating and testing a Conditional Access policy.
- Provide best practices for optimal implementation.
Let’s get started!
Table of Contents
What is Conditional Access in Entra ID?
Conditional Access (CA) is a policy-driven approach to managing user access in Entra ID. It enables organizations to enforce security policies based on contextual signals like user identity, device health, location, and application sensitivity. Think of Conditional Access as the gatekeeper for your organization’s resources, only granting access when all specified conditions are met.
Why is Conditional Access Critical?
In today’s digital landscape, a static username and password are no longer sufficient for safeguarding resources. With the rise of hybrid work and cloud adoption, organizations face evolving security challenges such as:
- Increased phishing and credential-based attacks.
- Users accessing resources from unmanaged devices or untrusted networks.
- Compliance requirements mandating advanced access controls.
Conditional Access provides dynamic and adaptive security by leveraging identity signals, ensuring only legitimate users can access sensitive data under pre-approved conditions.
Key Components of Conditional Access
To understand Conditional Access, let’s break it down into its core components:
Signals
Signals are the inputs evaluated to determine whether access should be granted. Key signals include:
- User or Group Membership: Policies can target specific users or groups (e.g., Finance Team, External Contractors).
- IP Location: Restrict access based on trusted IP ranges or geographic regions.
- Device Compliance: Ensure the device accessing resources meets compliance standards via Intune.
- Risk Levels: Integrate with Microsoft’s Identity Protection to detect risky sign-ins or compromised accounts.
- Application Sensitivity: Apply policies to specific SaaS or on-premises apps.
Conditions
Conditions define the rules under which the policy applies. Examples include:
- Sign-in Risk: Require additional verification for risky logins.
- Device Platform: Apply restrictions based on OS (Windows, iOS, Android).
- Location: Grant or block access depending on the user’s location.
- Client Apps: Differentiate between browser access and desktop/mobile app access.
Controls
Controls define what actions are required to satisfy the policy. These include:
- Grant Access Controls:
- Require MFA.
- Require compliant or hybrid Azure AD-joined devices.
- Require app protection policies.
- Session Controls:
- Enforce restrictions using Conditional Access App Control or session timeout policies.
Use Cases for Conditional Access
Conditional Access is versatile, addressing a wide range of security scenarios. Here are a few practical use cases:
Securing Remote Access
Ensure that remote employees can only access corporate resources from trusted devices and locations. For instance:
- Block access from untrusted regions.
- Require MFA for logins outside corporate IP ranges.
Protecting Sensitive Applications
Add additional security for applications like Microsoft Teams, SharePoint, or Salesforce by requiring MFA or restricting access to managed devices.
Addressing Risky Sign-ins
Leverage Identity Protection to trigger Conditional Access policies for sign-ins flagged as risky, such as:
- Password spray attacks.
- Impossible travel scenarios (e.g., a sign-in from New York immediately followed by one from Singapore).
Complying with Regulatory Standards
Meet compliance requirements by enforcing stricter access controls for highly regulated industries (e.g., healthcare, finance).
Creating a Conditional Access Policy
Let’s walk through a step-by-step guide to creating a basic Conditional Access policy that requires MFA for all users accessing Exchange Online from outside trusted locations
Step 1: Type “entra.microsoft.com” and enter username and password -> Navigate to left pane and click on “Conditional Access“.
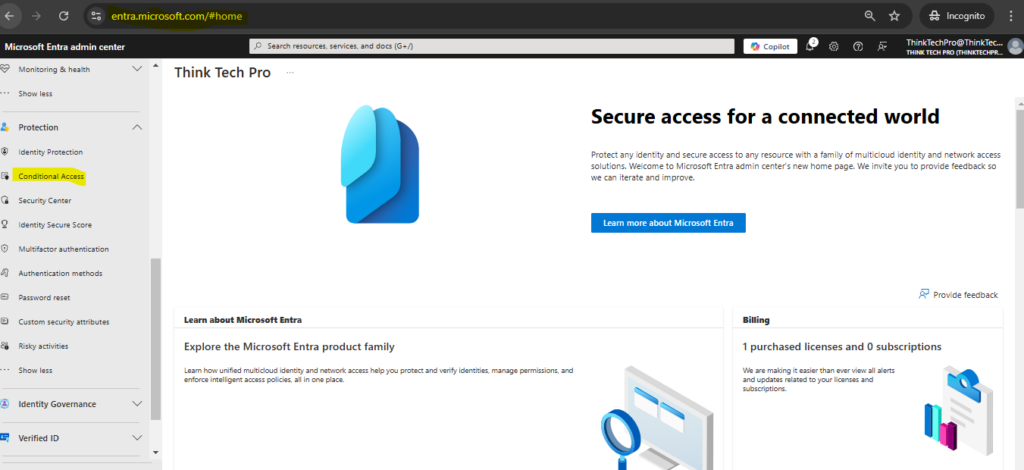
Step 2: Click on “Create new policy” , new wizard will open as show below screen.
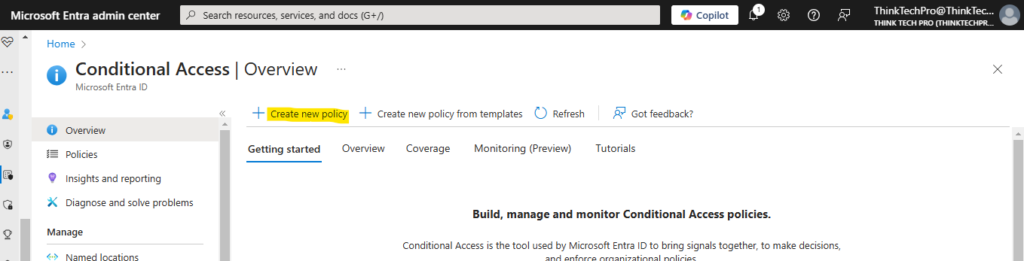
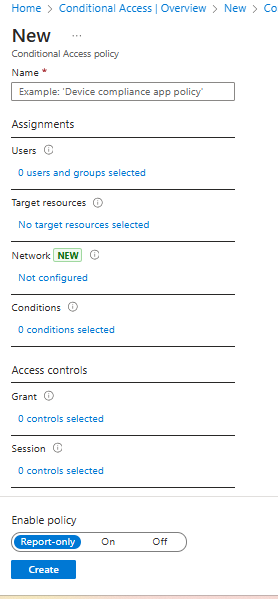
Step 3: Give the name of Policy here we are using “MFA for external access” and go to Assignments add all users

Step 4: Select Target resources here we select “Office 365” as shows below

Step 5: Select “Network” , here we include all trusted network and location. Which means that all the request which is coming form trusted network and location can access the application.

Step 6: Go to Access controls and click on “Grant access” and check on “Required multifactor authentication“

Step 7: Review all configuration and click create. Please note as of now we are create this policy as report-only
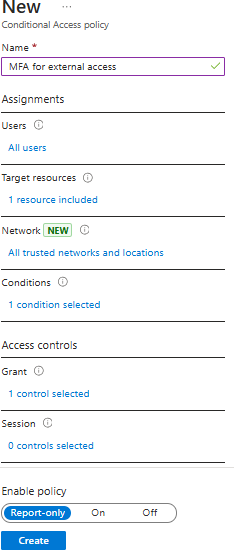
Best Practices for Conditional Access
To maximize the effectiveness of your Conditional Access implementation, follow these best practices:
Start with Audit Mode
Before enforcing a policy, enable it in “Report-only” mode to assess its impact. This helps identify potential disruptions.
Prioritize Break-Glass Accounts
Always exclude break-glass or emergency accounts from Conditional Access policies to avoid being locked out during unforeseen issues.
Layer Policies for Defense-in-Depth
Combine Conditional Access with Microsoft Defender for Cloud Apps to enhance session controls, such as blocking downloads for unmanaged devices.
Leverage Identity Protection
Integrate risk-based Conditional Access policies to automate responses to identity-related threats, such as:
- Forcing a password reset for users flagged as high risk.
- Blocking access for compromised accounts.
Monitor and Refine Policies
Regularly review sign-in logs and Conditional Access reports to:
- Identify bypass scenarios.
- Optimize policies based on user behavior and threat patterns.
Common Challenges and How to Address Them
Challenge 1: Overly Restrictive Policies
- Solution: Use “Exclude” settings and test policies in report-only mode to prevent legitimate users from being locked out.
Challenge 2: Managing Exceptions
- Solution: Establish a clear process for handling exceptions, such as creating dedicated Conditional Access policies for specific user groups.
Challenge 3: Policy Conflicts
Solution: Evaluate all active Conditional Access policies to ensure they work harmoniously and do not override each other unintentionally.
Conclusion
Conditional Access in Entra ID is an indispensable tool for implementing Zero Trust principles, balancing security with usability. By leveraging contextual signals and enforcing dynamic policies, organizations can significantly reduce their attack surface and protect critical resources.
Stay tuned for more insights in our 30 Days of Azure Security series!

