In the fast-paced realm of cybersecurity, the battle between defenders and attackers is ceaseless. Cyber threats grow in sophistication, targeting vulnerabilities with unprecedented precision. To fortify digital fortresses, Security Operations Centers (SOCs) must be equipped with advanced tools that can swiftly detect, analyze, and mitigate threats. This is where Splunk’s components emerge as the ultimate arsenal for next-generation SOC success, transforming the way security professionals safeguard digital assets. To learn more about Splunk, click here.

Table of Contents
1. Unveiling the SOC Evolution
The landscape of cybersecurity has morphed from simple virus detection to an intricate dance with ever-evolving threats. Splunk’s components stand as sentinels in this new era, providing the intelligence needed to counter advanced attacks.
2. Understanding Splunk’s Components
At the heart of SOC triumph is a comprehensive understanding of Splunk’s components. These elements form a cohesive system designed to ingest, process, and analyze massive streams of security data in real-time, arming security experts with the insights they need to stay one step ahead. To learn more about the Splunk component, click here.
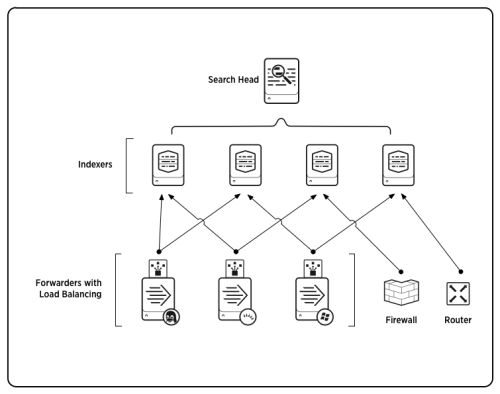
3. The Core of Data Ingestion: Universal Forwarder
The Universal Forwarder, a pivotal component, begins the journey. It efficiently collects data from a multitude of sources, ensuring no piece of information goes unnoticed. This data is the raw material for threat detection and analysis.
Imagine you’re a detective investigating a big case, and you need to gather evidence from various places to solve it. But instead of running around collecting evidence yourself, you have a team of helpers who go to different locations, gather clues, and bring them back to you. These helpers are like the Universal Forwarders in the world of technology.
In this scenario, you are the security analyst trying to keep your school safe from cyber threats. Your school’s computers, like classrooms, have important information that needs to be protected. But you can’t be in every classroom all the time to check for any suspicious activities.
This is where the Universal Forwarder comes into play. Just like your helpers in the detective story, the Universal Forwarder is a small program that quietly sits on each computer in the school. It’s like a watchful eye that keeps an eye out for any unusual behavior, like someone trying to break in or steal something.
Whenever something strange happens on a computer, the Universal Forwarder takes note and sends a message back to you, just like your helpers would bring the evidence to you in a detective case. This message tells you what happened and helps you figure out if there’s a real problem or just a false alarm.
So, the Universal Forwarder is like your team of trusted helpers who watch over the computers and make sure everything is safe. They send you messages when they see something unusual, allowing you to step in and take action if needed, just like a detective solving a case, to keep the school safe from any potential threats.

4. Heavy Forwarder: Transforming Data
Enter the Heavy Forwarder, a master of data transformation. It enriches data, adding context and detail before passing it on. This preparatory step sets the stage for more accurate and effective analysis.
Think of a translator who turns a foreign story into a language you understand. Heavy Forwarder is like that translator, taking complex computer data and making it simpler and clearer. This helps experts understand if there’s anything wrong or unusual happening in the computer world, just like how the translator helps you understand a story from another country.
5. Indexers: The Data Vaults
Indexers take the transformed data and organize it into easily retrievable segments. This data warehousing allows for swift querying and analysis, a crucial facet when responding to threats in real-time.
Imagine a big library where books are organized on shelves. Each shelf has a label that tells you what topics the books cover. Indexers are like those labels, helping you quickly find the right book when you need it. They organize computer data so that experts can easily search and find information when they’re trying to solve problems or understand what’s happening, just like how labels help you find the perfect book in a library.
6. Search Head: Unleashing Insights
The Search Head emerges as the gateway to actionable insights. Security analysts interact with this component to run searches, create reports, and visualize trends, all critical elements for proactive threat hunting.
7. Data Enrichment with Knowledge Objects
Knowledge Objects serve as interpreters, translating raw data into human-readable information. Whether it’s detecting patterns or identifying anomalies, these objects aid in extracting meaning from the data deluge.
8. Dashboards and Visualizations: Painting a Clear Picture
Threats are often complex and multifaceted. Dashboards and Visualizations take abstract data and convert it into visual narratives. Security professionals gain a bird’s-eye view, enabling them to quickly grasp the threat landscape.
9. Proactive Defense: Realizing Next-Gen SOC Success
In a threat landscape where the only constant is change, Splunk’s components provide the agility and versatility required for next-gen SOC success. By enabling real-time analysis, rapid threat detection, and informed decision-making, these components allow security professionals to pivot from reactive to proactive defense.
10. The Road Ahead: Embracing Innovation
As cyber threats continue to evolve, the journey doesn’t end. Embracing innovation remains key. Splunk’s components stand ready to evolve alongside the threats, bolstering SOC capabilities and ensuring that defenders are always a step ahead.
In Conclusion: Fortifying Digital Frontlines
In the perpetual battle for digital supremacy, SOCs armed with Splunk’s components possess a distinct advantage. These components, meticulously designed and seamlessly integrated, empower security professionals to outsmart, outmaneuver, and ultimately defeat adversaries. As the digital realm evolves, the synergy between technology and expertise will continue to form an impregnable fortress, safeguarding our digital future.
