Table of Contents
Public Key Infrastructure (PKI) Introduction
Public Key Infrastructure (PKI) is a system of digital security that uses cryptography to create a secure environment for communication and data exchange. PKI is based on the use of public and private key pairs. The process of decrypting data uses private keys, whereas data encryption uses public keys.
PKI finds application across a diverse range of uses, including:
Communication protocols known for their security, like HTTPS and TLS
Digital signatures
Certificate authorities
Secure email
Secure file transfer
Secure remote access
Why Public Key Infrastructure (PKI) is widely adopted by enterprise businesses
Public Key Infrastructure (PKI) is widely adopted by enterprise businesses for several key reasons:
Security:
Data Encryption: PKI enables secure communication by using public and private key pairs for encrypting and decrypting data. This ensures the confidentiality and integrity of sensitive information.
Digital Signatures: PKI allows the use of digital signatures, providing a way to verify the authenticity and origin of digital documents or messages. This is crucial for ensuring that information has not been tampered with during transit.
Authentication:
Identity Verification: PKI helps in verifying the identity of users, devices, or services in a network. This is achieved through the use of digital certificates, which are issued by trusted Certificate Authorities (CAs). This ensures that entities are who they claim to be.
Secure Access Control: PKI plays a vital role in enabling secure access control mechanisms. By using digital certificates for user authentication, organizations can control access to sensitive resources and data.
Data Integrity:
Hash Functions: PKI often involves the use of hash functions to ensure data integrity. Hash values generated for data are included in digital signatures, allowing the recipient to verify that the data has not been altered.
Regulatory Compliance:
Legal and Regulatory Requirements: Many industries and regions have specific legal and regulatory requirements regarding the protection and privacy of digital information. PKI provides a framework for meeting these compliance standards by offering a secure and verifiable way to handle sensitive data.
Secure Communication:
SSL/TLS for Web Security: PKI is widely used in web security protocols like SSL/TLS, which ensures secure communication between web browsers and servers. This is essential for safeguarding online transactions, login credentials, and other sensitive data exchanged over the internet.
Email Security:
Email Encryption and Signing: PKI is used for encrypting and digitally signing emails, adding an extra layer of security to electronic communication. This is particularly important for protecting sensitive information sent via email.
Key Management:
Secure Key Storage: PKI provides a secure framework for managing and storing cryptographic keys. Proper key management is essential for maintaining the security of encrypted data and digital signatures.
Interoperability:
Standardization: PKI is based on established standards, which promote interoperability among different systems and vendors. This ensures that PKI components from different providers can work together seamlessly.
How Public Key Infrastructure (PKI) Works
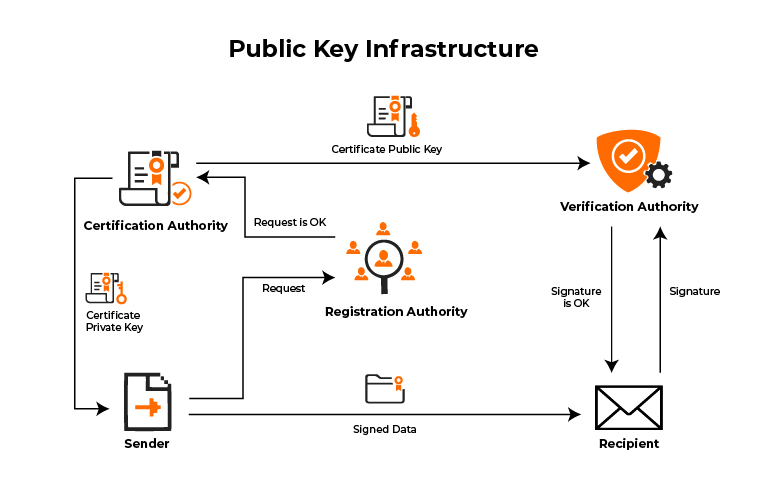
PKI works by using a combination of digital certificates, certificate authorities, and public and private key pairs.
Digital certificates are electronic records that associate a public key with an identity. Certificate authorities (CAs) are tasked with issuing these digital certificates.
Certificate authorities are trusted third parties that verify the identities of entities before issuing them digital certificates.
Encryption and decryption of data rely on pairs of public and private keys. Public keys encrypt data, while private keys decrypt it.
When two parties want to communicate securely using PKI, they exchange their digital certificates. The certificates are used to verify the identities of the parties and to obtain their public keys. The parties then use the public keys to encrypt their communication.
Architecture of Public Key Infrastructure (PKI)
PKI is typically implemented as a three-tier architecture:
Root CA: The root CA is the highest level of the PKI hierarchy. It is responsible for issuing digital certificates to subordinate CAs.
Subordinate CAs: Subordinate CAs are responsible for issuing digital certificates to end entities.
End entities: End entities are the users, devices, and applications that use PKI to communicate securely.
Public Key Infrastructure (PKI) Policies
PKI policies are used to define the rules and procedures for managing and using a PKI. PKI policies should address the following areas:
Certificate issuance and renewal
Certificate revocation
Key management
Access control
Auditing
Public Key Infrastructure (PKI) Standards
There are a number of PKI standards that have been developed to ensure interoperability between different PKI implementations. Some of the most common PKI standards include:
X.509: This is a vital standard defining the format of digital certificates. It establishes rules for consistent and interoperable certificates, playing a crucial role in securing online transactions and communications. Serving as a blueprint, X.509 guides the creation, issuance, and management of digital certificates, forming the foundation of Public Key Infrastructure (PKI) for secure internet communication.
PKCS#12: This standard defines the format of personal information exchange (PFX) files.
S/MIME: This standard defines how to use digital signatures and encryption to protect email messages.
Public Key Infrastructure (PKI) Strategies
When designing and implementing a PKI, it is important to consider the following strategies:
Start small and scale up: It is better to start with a small PKI and scale it up as needed. This will help to reduce the complexity of the implementation and to identify any potential problems early on.
Use a trusted CA: It is important to use a trusted CA to issue digital certificates. This will help to ensure that the certificates are valid and that the identities of the parties involved are verified.
Implement a certificate revocation policy: It is important to have a plan in place for revoking certificates in the event that they are compromised or no longer needed.
Implement a key management policy: It is important to have a plan in place for managing public and private keys. This includes generating, storing, and backing up keys.
Educate users: It is important to educate users about how to use PKI securely. This includes teaching users how to generate and store keys, how to request and renew certificates, and how to verify the identities of other parties.
How to Automate Public Key Infrastructure (PKI)
There are a number of ways to automate PKI tasks. Some common PKI automation tools include:
Certificate lifecycle management (CLM) tools: CLM tools can automate tasks such as certificate issuance, renewal, and revocation.
Key management tools: Key management tools can automate tasks such as key generation, storage, and backup.
PKI integration tools: PKI integration tools can be used to integrate PKI with other systems and applications.
Governance of Public Key Infrastructure (PKI)
PKI governance is the process of managing and overseeing a PKI. PKI governance should address the following areas:
Risk management: PKI governance should identify and mitigate the risks associated with using PKI.
Compliance: PKI governance should ensure that the PKI is compliant with all applicable regulations and standards.
Continuous improvement: PKI governance should include a process for continuous improvement of the PKI.
Conclusion
PKI is a complex but powerful security technology. By understanding the basics of PKI and following the strategies and best practices described above, organizations can implement and use PKI.
You can follow us on LinkedIn and Twitter for IT updates.
Also read..
Investigating Active Directory Security Breaches: A Comprehensive Guide