Table of Contents
Introduction to Microsoft Entra ID
Microsoft Entra ID, formerly known as Azure Active Directory, is a cloud-based identity and access management service that enables organizations to manage user identities and control access to applications and resources. It plays a critical role in securing enterprise environments by providing robust authentication, authorization, and access management capabilities. With the rise of cloud adoption and the increasing number of applications in use, managing access efficiently and securely has become more important than ever. Microsoft Entra ID offers a comprehensive solution for this challenge, allowing IT administrators to manage access to enterprise applications with ease. One of its key features includes managing enterprise applications with OAuth permission grants, enabling secure and seamless authorization for applications that need access to organizational resources.
Understanding OAuth Permission Grants
What are OAuth Permission Grants?
OAuth permission grants are a core component of the OAuth 2.0 protocol, which is widely used for authorization. In the context of Microsoft Entra ID, OAuth permission grants allow applications to request access to resources on behalf of users or other applications. These permissions can be delegated (acting on behalf of a user) or application-specific (acting independently of a user).
Purpose and Function
The primary purpose of OAuth permission grants is to enable secure and efficient access to resources. By using OAuth, applications can obtain limited access to user resources without exposing user credentials. This is particularly important in modern enterprise environments where security and compliance are paramount. OAuth permission grants function by issuing tokens that authorize specific actions, ensuring that access is controlled and monitored.
Configuring and Managing Access
- Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
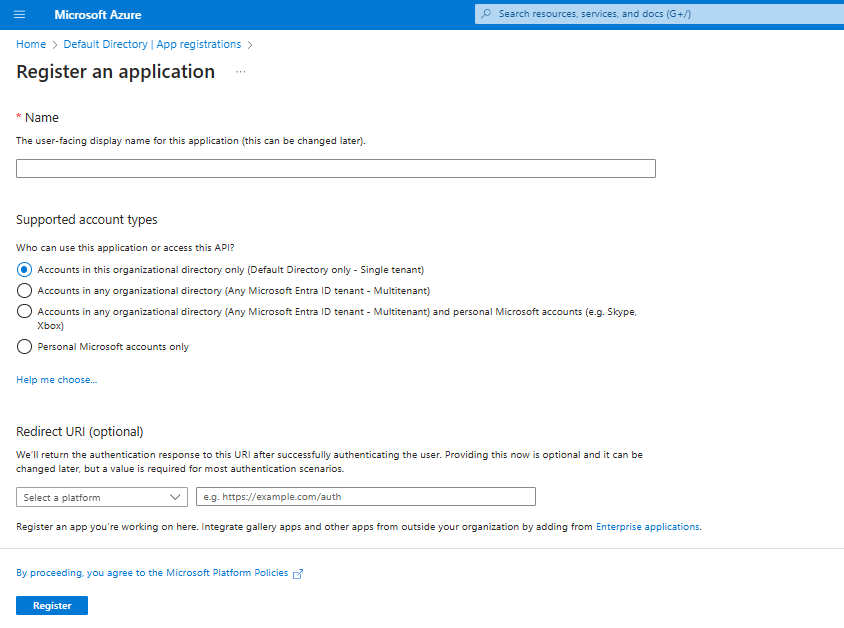
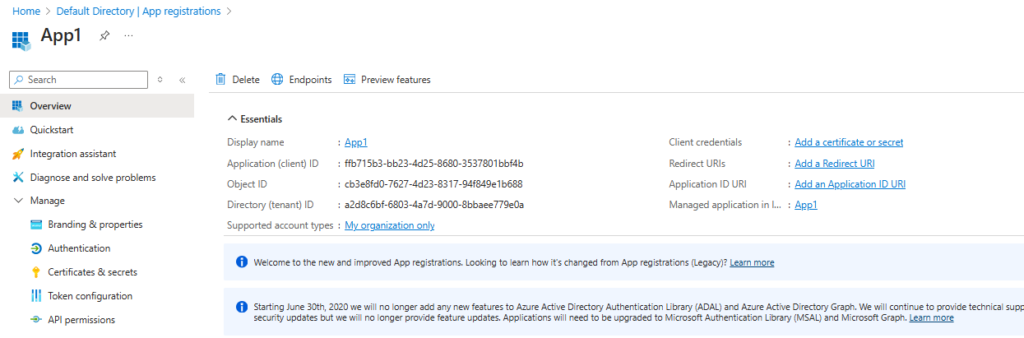
- Browse to Identity > Applications > App registrations then select New registration.
- Name the application, for example “APP1”.
- Select a supported account type, which determines who can use the application.
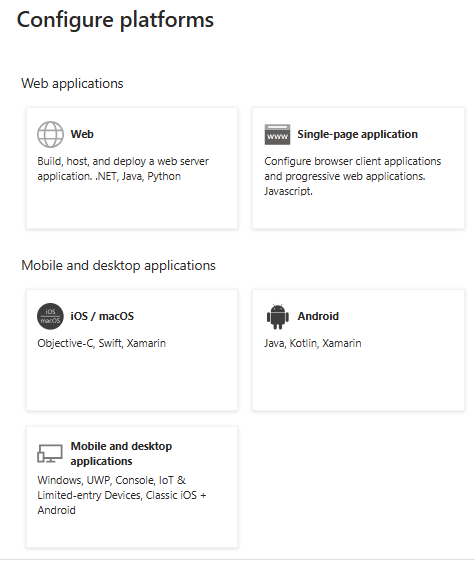
- Under Redirect URI, select Web for the type of application you want to create. Enter the URI where the access token is sent to.
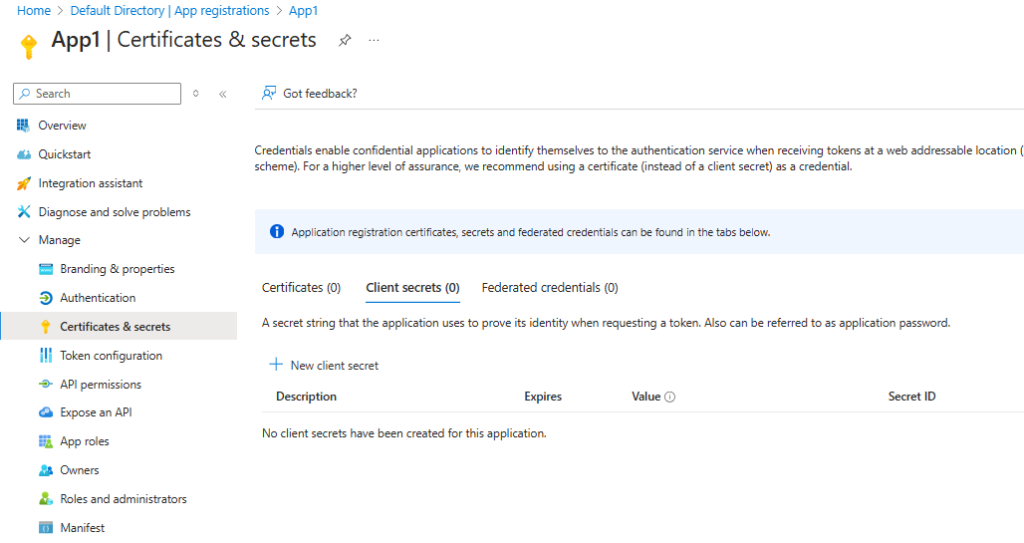
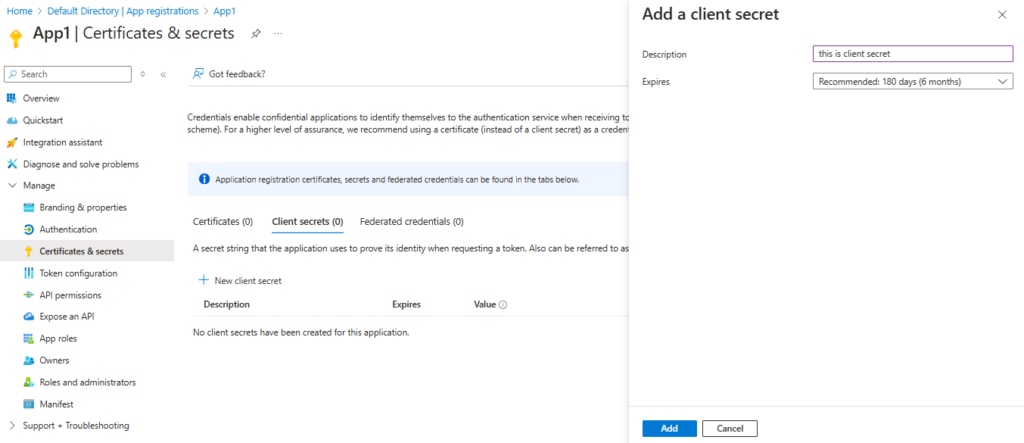
- Select Certificates & Secrets and click on create New client secrets, here we set client secret expire after 180 days
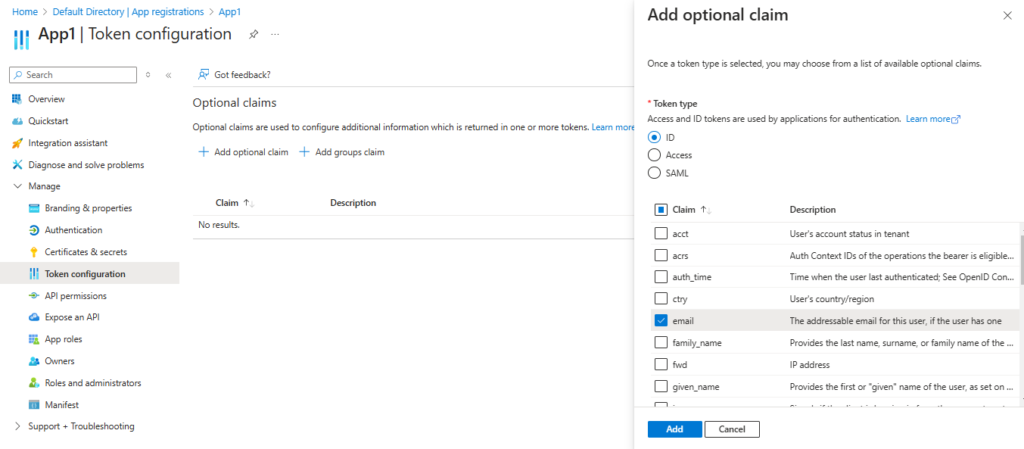
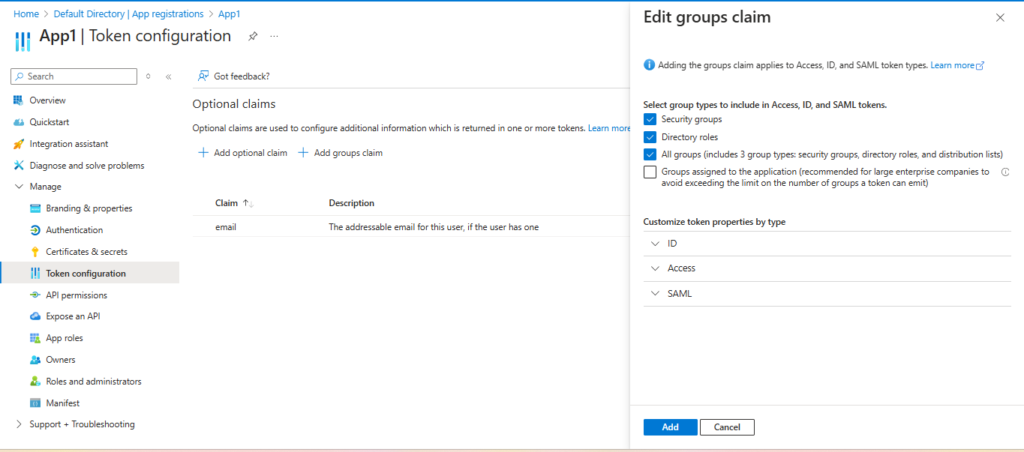
- Configure Token, here are using email id and group
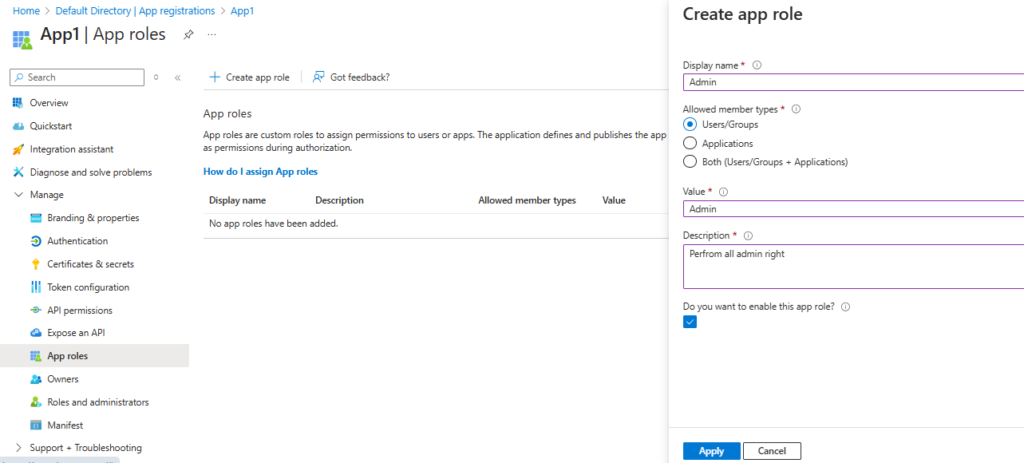
- Define app role as Admin
Best Practices for Security and Compliance
1. Follow the Principle of Least Privilege
Grant only the permissions necessary for your app to function. Avoid over-permissioning, which can lead to security vulnerabilities.
2. Use Managed Identities
Leverage managed identities for applications running on Azure resources. This eliminates the need for hard-coding credentials and improves security.
3. Implement Conditional Access Policies
Define conditional access policies to enforce multi-factor authentication (MFA) and control access based on user location, device compliance, and risk level.
4. Monitor and Audit Activity
Regularly monitor sign-in activity and audit logs for suspicious behavior. Microsoft Entra ID provides comprehensive logging and reporting tools to help you stay vigilant.
5. Automate Processes
Use Microsoft Entra lifecycle workflows to automate routine tasks such as user provisioning and access management. This reduces manual effort and ensures consistency.
Real-World Use Cases
Use Case 1: Multi-Factor Authentication (MFA)
In an enterprise setting, MFA can be enforced for all critical applications using OAuth permission grants. By requiring additional verification, organizations can ensure that only authorized users access sensitive information.
Use Case 2: Conditional Access Policies
Conditional access policies can be used to restrict access to applications based on various conditions such as user location and device compliance. This is particularly useful for organizations with a distributed workforce.
Use Case 3: Delegated Access for Third-Party Applications
Organizations often need to grant third-party applications access to their resources. OAuth permission grants allow this while ensuring that access is limited and controlled.
Common Challenges and Troubleshooting Tips
Challenge 1: Managing Token Lifetimes
Token lifetimes can impact user sessions and app performance. Configure token settings in the Azure portal to balance security and usability.
Challenge 2: Handling Multi-Tenant Applications
For multi-tenant applications, ensure proper isolation and security measures are in place to protect data across different tenants.
Challenge 3: Ensuring Compliance
Stay updated with compliance requirements and ensure your app registrations adhere to regulations such as GDPR, HIPAA, and others relevant to your industry
Conclusion
Managing access to enterprise applications in Microsoft Entra ID, including OAuth permission grants, is a critical task that requires attention to detail and adherence to best practices. By following the guidelines outlined in this post, you can ensure your applications are secure, compliant, and efficient. Whether you are just starting or looking to optimize your existing setup, these insights will help you make the most of Microsoft Entra ID’s capabilities.
Stay tuned for more insights in our 30 Days of Azure Security series!

