Table of Contents
Introduction
In today’s fast-paced digital world, protecting data and systems from cyber threats is a top priority. Microsoft Sentinel, a cloud-native Security Information and Event Management (SIEM) and Security Orchestration Automated Response (SOAR) solution, is designed to meet the evolving demands of cybersecurity. With its advanced features and integration capabilities, Sentinel empowers organizations to identify, investigate, and respond to security incidents in real-time.
What is Security Information and Event Management (SIEM)?
Security Information and Event Management (SIEM) is a system that collects, analyzes, and stores security data from various sources to provide centralized visibility and actionable insights. SIEM tools are essential for:
- Detecting and responding to security threats.
- Meeting compliance requirements.
- Gaining insights into network activity and vulnerabilities.
What is Microsoft Sentinel?
Microsoft Sentinel is a cloud-based SIEM and SOAR solution hosted on Azure. It provides comprehensive tools for:
- Threat Detection: Leveraging AI to identify potential risks.
- Incident Response: Automating and managing security operations.
- Data Insights: Centralizing and visualizing security data.
Key components include:
- Data Connectors for seamless integration.
- Workbooks for custom dashboards.
- Playbooks for automating responses.
Microsoft Sentinel helps you enable end-to-end security operations including collection, detection, investigation, and response:
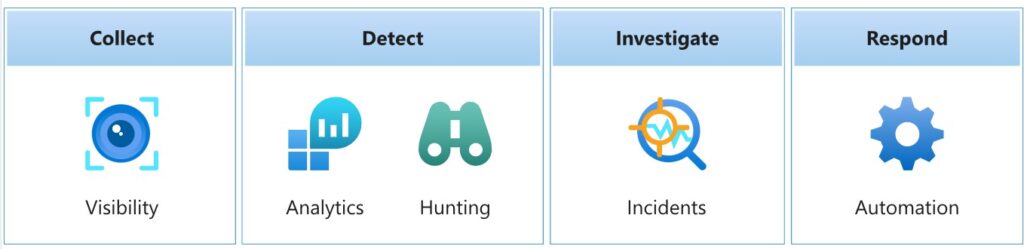
How Microsoft Sentinel Works
- Data Ingestion and Analysis
Sentinel collects security data from various sources, including Azure services, on-premises systems, and third-party applications. It uses AI to analyze this data and identify threats. - Incident Management
Alerts are generated for potential risks, prioritized, and managed through an intuitive interface. - Response Automation
Automation playbooks streamline responses, reducing the time to mitigate threats.
Key Features of Microsoft Sentinel
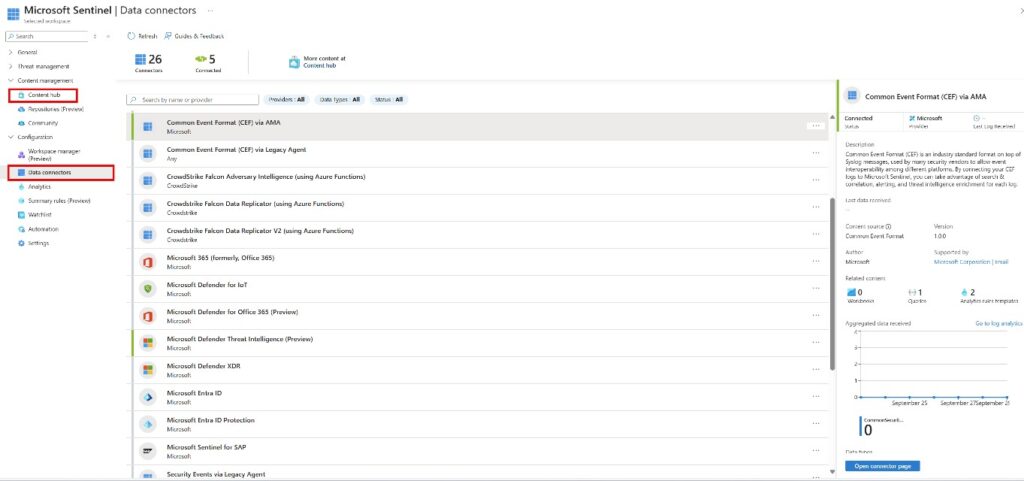
Data Connectors
Getting your data imported into Microsoft Sentinel should be your initial step. This is made possible by data connections. Installing Content Hub solutions is the initial step in connecting Data Connectors. After installation, you only need to click a button to add certain services, such Azure activity logs. Others need additional setup, like syslog. All scenarios and sources are covered by data connectors, which include but are not restricted to:
- Syslog
- CEF, or Common Event Format
- Azure Activity
- Microsoft Defender services
- The Trusted Automated eXchange of Indicator Information (TAXII) (for threat intelligence)
- Google Cloud Platform (GCP)
- Amazon Web Services (AWS)
In simple term Data connector is use to connect to multiple data sources, including Microsoft Defender, AWS, Office 365, and third-party solutions, ensuring comprehensive visibility.
Log Retention
Data is saved in the Log Analytics workspace following its ingestion into Microsoft Sentinel. One advantage of utilizing Log Analytics is that you may query your data using the Kusto Query Language (KQL). KQL is a powerful query language that allows you to explore and learn from our data.
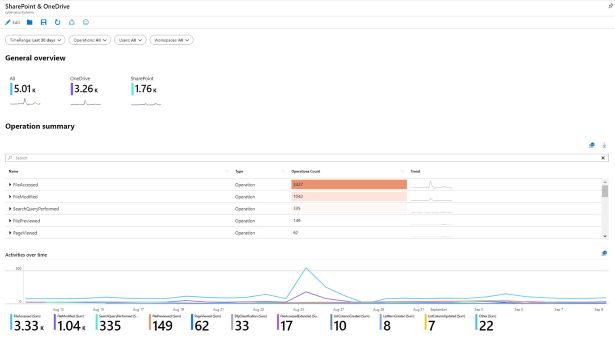
Workbooks
Workbooks are a way to see your data in Microsoft Sentinel. Consider workbooks to be dashboards. Every dashboard element is constructed using an underlying KQL query of your data. You may either make your own workbooks from start or modify the pre-built worksheets in Microsoft Sentinel to suit your needs. Since Sentinel is the implementation of Monitor workbooks, you are likely familiar with this functionality if you have used Azure Monitor workbooks.
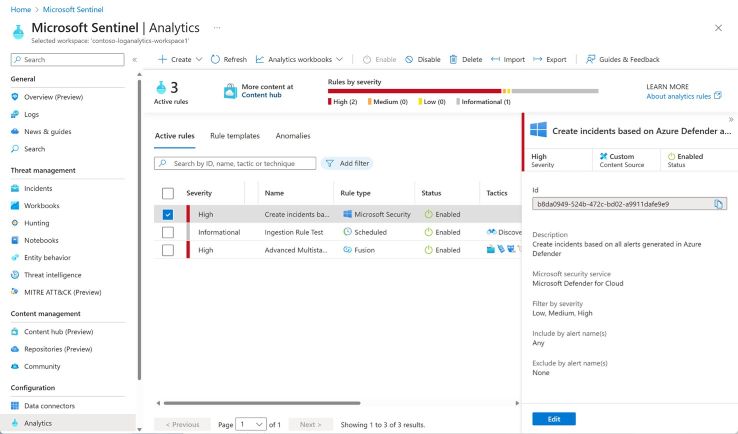
Analytics Alerts
Your logs and some data visualization are all you have so far. Now that you have some proactive analytics across your data, it would be fantastic to be alerted when something questionable happens. You can activate analytics notifications that are already integrated into your Sentinel workplace. Alerts come in a variety of forms, some of which you may customize to your preferences. Microsoft-proprietary machine-learning models are used to build other warnings. Additionally, you have the option to directly generate personalized, timed notifications.
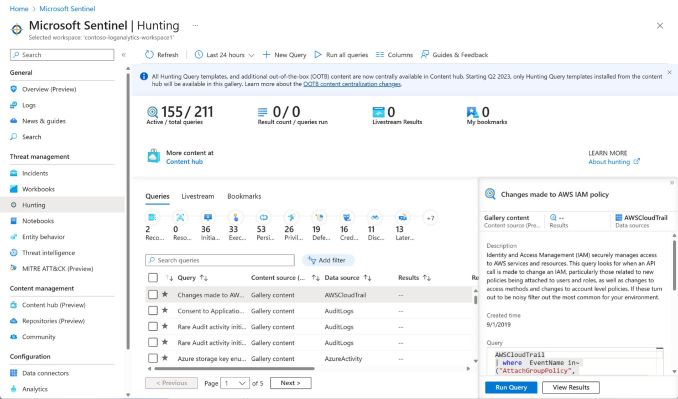
Threat Hunting
This post won’t go into detail about threat hunting, as we plan to dedicate a separate article to that topic. However, for SOC analysts looking to investigate suspicious activities, many Content Hub solutions offer pre-built hunting queries that can be readily used. Analysts also have the flexibility to craft custom queries tailored to their needs. Additionally, Microsoft Sentinel integrates with Azure Notebooks, providing sample notebooks for advanced users who wish to leverage the capabilities of programming languages to perform in-depth data analysis.
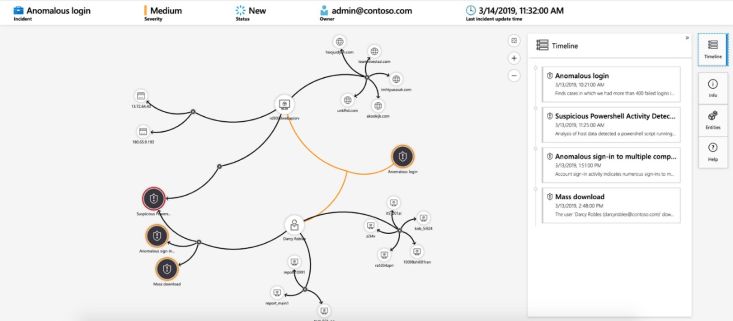
Incidents and Investigations
When alerts are triggered in Microsoft Sentinel, they generate incidents. You can manage these incidents using standard tools, such as updating their status or assigning them to specific team members for investigation. Microsoft Sentinel also includes powerful investigation features, allowing you to visually analyze incidents by mapping related entities across log data on a timeline for a comprehensive understanding
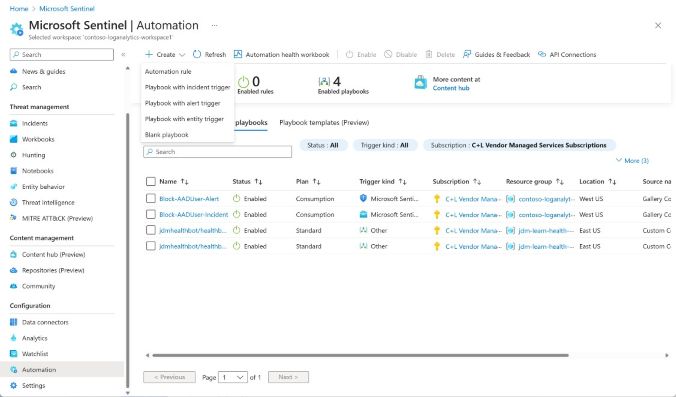
Automation Playbooks
Microsoft Sentinel empowers you to enhance the efficiency of your SOC by enabling automatic responses to incidents. You can design automated workflows, known as playbooks, to handle events effectively. These playbooks can be used for various purposes, including incident management, data enrichment, investigation, or remediation. This functionality is part of what’s commonly referred to as Security Orchestration, Automation, and Response (SOAR), helping streamline your security operations.
When to Use Microsoft Sentinel
Microsoft Sentinel is a solution for performing security operations on your cloud and on-premises environments.
Use Microsoft Sentinel if you want to:
- Collect event data from various sources.
- Perform security operations on that data to identify suspicious activity.
Security operations could include:
- Visualization of log data
- Anomaly detection
- Threat hunting
- Security incident investigation
- Automated response to alerts and incidents
Microsoft Sentinel offers other capabilities that could help you decide whether it’s the right fit for you:
- Cloud-native SIEM: with no servers to provision, scaling is effortless
- Integration with the Azure Logic Apps service and its hundreds of connectors
- Benefits of Microsoft research and machine learning
- Key log sources provided for free
- Support for hybrid cloud and on-premises environments
- SIEM and a data lake all in one
When you began investigating Microsoft Sentinel, your organization had some clear requirements:
- Support for data from multiple cloud environments
- Features and functionality required for a security operations center (SOC), without too much administrative overhead
You’ve found that Microsoft Sentinel could be a good fit. It offers data connectors for syslog, Amazon Web Services (AWS), and other sources, and the ability to scale effortlessly without provisioning servers. During your analysis, you also realized that your organization should make automation a key part of its SOC strategy. Automation wasn’t something the organization had considered before, but now you’ll look into using automation playbooks.
If you’re collecting infrastructure or application logs for performance monitoring, consider also using Azure Monitor and Log Analytics for that purpose.
And perhaps you want to understand the security posture of your environment, make sure that you’re compliant with policy, and check for security misconfigurations. If so, consider also using Microsoft Defender for Cloud. You can ingest Defender for Cloud alerts as a data connector for Microsoft Sentinel.
Benefits of Using Microsoft Sentinel
Microsoft Sentinel is a comprehensive, cloud-native solution for security operations that offers a range of benefits to organizations seeking to enhance their cybersecurity posture. Here are the key advantages of using Microsoft Sentinel:
1. Cloud-Native SIEM
Microsoft Sentinel is a scalable, cloud-native Security Information and Event Management (SIEM) solution. It eliminates the need to provision servers or maintain complex infrastructure, allowing organizations to scale effortlessly as their data volume grows.
2. Centralized Data Collection
Sentinel collects and analyzes data from various sources, including:
- On-premises systems.
- Cloud platforms like Azure, AWS, and Google Cloud.
- Third-party applications. This centralized approach ensures complete visibility into your environment.
3. Advanced Threat Detection
With built-in AI and machine learning, Sentinel detects anomalies and suspicious activities more effectively. It continuously learns from data patterns to identify potential threats faster than traditional SIEM solutions.
4. Integration with Microsoft Ecosystem
Sentinel integrates seamlessly with other Microsoft products like:
- Azure Active Directory for identity management.
- Microsoft Defender for Cloud for compliance and security posture management.
- Azure Logic Apps for automation playbooks.
5. Proactive Threat Hunting
Security analysts can use built-in queries or create custom ones to proactively search for threats. For advanced investigations, Sentinel supports Azure Notebooks, allowing users to analyze data with powerful programming tools.
6. Automation and Orchestration (SOAR)
Automated workflows, known as playbooks, enable quick responses to incidents. This capability streamlines processes such as:
- Incident management.
- Threat investigation.
- Data enrichment and remediation.
7. Cost-Efficiency
With pay-as-you-go pricing, Sentinel minimizes costs by charging only for the resources you use. Additionally, some key log sources, like Azure Security Center alerts, are provided for free.
8. Real-Time Insights
Interactive dashboards and workbooks provide real-time insights into your environment’s security posture. These visual tools help SOC teams prioritize and act on critical threats effectively.
9. Support for Hybrid Environments
Sentinel supports both cloud and on-premises environments, making it ideal for organizations operating in hybrid setups. It provides flexibility and adaptability across diverse infrastructures.
10. Enhanced Collaboration
With its incident management and investigation features, Microsoft Sentinel fosters better collaboration among SOC teams. Analysts can assign tasks, update statuses, and track incident resolution within the platform.
11. Quick Deployment
As a cloud-based solution, Microsoft Sentinel can be set up quickly without extensive hardware or software requirements. This rapid deployment allows organizations to start monitoring and securing their environments faster.
12. Compliance and Reporting
Sentinel helps ensure compliance with industry standards and regulatory requirements by providing detailed audit logs, reports, and alerts for policy violations or security misconfigurations.
13. Scalability and Performance
Built on Azure, Sentinel can handle massive volumes of data with high availability and performance, making it suitable for organizations of all sizes.
14. Flexibility with Data Connectors
Sentinel offers over 100 built-in data connectors for seamless integration with third-party applications, devices, and platforms. This flexibility simplifies data ingestion and analysis.
Integrations with Microsoft Sentinel
Microsoft Sentinel integrates with various Microsoft and third-party solutions to enhance security monitoring and incident response:
- Azure Services: Includes Azure AD, Azure Firewall, Security Center, and Key Vault to monitor identity, network, and security posture.
- Microsoft 365: Integrates with Defender for Identity, Endpoint, and Office 365 to track user activities, endpoint security, and email threats.
- Threat Intelligence: Utilizes Microsoft and third-party feeds (e.g., CrowdStrike, Anomali) to detect emerging threats.
- Third-Party Security Tools: Supports integrations with other SIEMs, firewalls, and network devices for better detection.
- Automation: Leverages Logic Apps and playbooks to automate workflows and incident responses.
- Custom Data Connectors: Allows integration with non-standard logs and data sources.
- Incident Management: Integrates with tools like ServiceNow for automated incident creation and response.
- Cloud Platforms: Supports integration with AWS and other cloud services for cross-cloud monitoring.
Challenges and Solutions of Microsoft Sentinel
Challenge: Data Overload
Solution: Implement data filtering and ingestion controls to focus on the most critical security logs. Use KQL (Kusto Query Language) to create customized queries for specific use cases and avoid unnecessary data noise.
Challenge: Complex Configuration
Solution: Utilize Microsoft Sentinel templates and data connectors to simplify configuration. Leverage built-in playbooks for incident response automation, reducing the need for complex manual setups.
Challenge: High Cost of Data Storage
Solution: Implement data retention policies to optimize storage costs, such as archiving older data to lower-cost storage tiers. Use Sentinel’s pricing calculator to monitor and manage costs effectively.
Challenge: Integration with Non-Microsoft Tools
Solution: Use custom connectors and REST API support to integrate with third-party security tools and other cloud environments like AWS. Leverage Microsoft Sentinel’s open-source integrations to connect with SIEM tools like Splunk.
Challenge: Alert Fatigue
Solution: Use machine learning and analytics to prioritize alerts based on severity. Implement automated incident response playbooks to handle low-priority alerts and reduce the workload for security teams.
Challenge: Lack of Skilled Personnel
Solution: Provide training and utilize Microsoft’s built-in resources, such as Sentinel’s Workbooks, dashboards, and tutorials. Adopt a collaborative approach with third-party managed services if necessary.
Challenge: Complex Incident Investigation
Solution: Use Sentinel’s built-in investigation tools, including case management, to streamline the process. Integrate with automation tools like Logic Apps to enhance efficiency in incident response.
Challenge: Scalability Issues
Solution: Take advantage of Sentinel’s cloud-native architecture, which allows for easy scalability. Use Azure Monitor and Azure Automation to scale resources based on demand.
Conclusion
Microsoft Sentinel is a robust, cloud-native solution that empowers businesses to protect their digital ecosystems effectively. Whether you’re a small business or a large enterprise, Sentinel offers the tools you need to monitor, detect, and respond to security threats efficiently.
FAQs
- What is Microsoft Sentinel best used for?
Microsoft Sentinel is ideal for centralized security monitoring, threat detection, and automated incident response. - Does Sentinel work with third-party tools?
Yes, Sentinel supports integration with numerous third-party solutions for extended functionality. - Can small businesses use Microsoft Sentinel?
Absolutely. Its scalability and flexible pricing make it accessible to small and medium-sized businesses. - How does Microsoft Sentinel ensure data security?
Sentinel encrypts data at rest and in transit, ensuring robust security for all ingested information. - What’s the difference between Sentinel and traditional SIEM tools?
Sentinel is cloud-native, offering enhanced scalability, real-time analytics, and AI-driven insights compared to traditional on-premises SIEM solutions.
Stay tuned for more insights in our 30 Days of Azure Security series!

