Table of Contents
Overview of Microsoft Entra ID Governance
In today’s digital-first world, managing identities effectively has become a critical pillar of IT governance. Microsoft Entra ID Governance (formerly Azure AD Governance) empowers organizations to maintain control over identities and access while meeting compliance requirements.
Microsoft Entra ID Governance is an identity governance solution that enables organizations to improve productivity, strengthen security and more easily meet compliance and regulatory requirements. You can use Microsoft Entra ID Governance to automatically ensure that the right people have the right access to the right resources. This is achieved through identity and access process automation, delegation to business groups, and increased visibility. With features in Microsoft Entra ID Governance and related Microsoft products, you can mitigate identity and access risks by protecting, monitoring, and auditing access to critical assets.
Specifically, Microsoft Entra ID Governance helps organizations address these four key questions, for access across services and applications both on-premises and in clouds:
- Which users should have access to which resources?
- What are those users doing with that access?
- Are there organizational controls in place for managing access?
- Can auditors verify that the controls are working effectively?
Identity Lifecycle Management
Identity Governance assists organizations in striking a balance between productivity—such as determining how swiftly a person can access necessary resources upon joining the organization—and security, which considers how access should evolve over time due to changes in employment status. The backbone of Identity Governance is identity lifecycle management. Achieving effective governance at scale necessitates the modernization of identity lifecycle management infrastructure for applications.

Why It Matters:
An improperly managed identity can become a security risk, leading to unauthorized access or lingering permissions after an employee leaves. For instance, when a new sales manager joins, their digital identity is created, and access to Salesforce, the CRM platform, is provisioned automatically based on their role. This ensures they can hit the ground running without delays while maintaining security boundaries.
Key Steps:
- Onboarding: Automatically provision accounts and assign roles based on department or job function.
- Role Changes: Adjust permissions dynamically during promotions, departmental transfers, or role changes.
- Offboarding: Ensure accounts are disabled and access revoked promptly after separation to minimize risks.
Access Lifecycle Management
Organizations need a process to manage access beyond what was initially provisioned for a user when that user’s identity was created. Furthermore, enterprise organizations need to be able to scale efficiently to be able to develop and enforce access policy and controls on an ongoing basis.
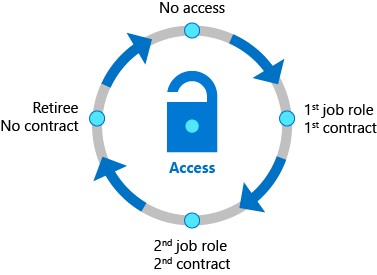
With Microsoft Entra ID Governance, IT departments can establish which access rights users should have across various resources. They can also determine necessary enforcement checks, such as separation of duties or access removal on job change are necessary.
Microsoft Entra ID is equipped with connectors for a vast array of cloud and on-premises applications. It enables you to integrate your organization’s other applications, whether they rely on AD groups, other on-premises directories, or databases, and whether they use a SOAP or REST API, including SAP. It also supports standards like SCIM, SAML, and OpenID Connect. When a user tries to sign in to one of these applications, Microsoft Entra ID enforces Conditional Access policies, ensuring a secure and seamless access experience.
Access changes across apps and groups can be automated based on attribute changes. Microsoft Entra lifecycle workflows and Microsoft Entra entitlement management automatically add and remove users from groups or access packages, ensuring that access to applications and resources is always up-to-date. Users can be moved to different groups when their condition within the organization changes, and they can be completely removed from all groups or access packages if necessary.
Best Practices:
- Access Provisioning: Align permissions with role-based access control (RBAC) policies.
- Periodic Reviews: Implement access reviews to ensure permissions remain appropriate. For example, a quarterly review of finance team access to sensitive budget reports can help identify and revoke outdated permissions.
- Revocation: Revoke access immediately when roles change or employees exit.
By adopting these practices, organizations can mitigate risks such as privilege creep, where users accumulate excessive permissions over time.
Privileged Access Lifecycle
Governing privileged access is a key part of modern Identity Governance especially given the potential for misuse associated with administrator rights can cause to an organization. The employees, vendors, and contractors that take on administrative rights need to have their accounts and privileged access rights governed.
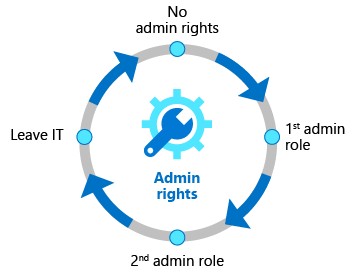
Key Considerations:
- Just-in-Time Access: Enable privileged access only when needed, reducing the window of vulnerability. For example, a system administrator can request elevated access to troubleshoot a server issue for a limited time.
- Role-Based Access Control: Assign permissions based on the principle of least privilege to minimize potential abuse.
- Audit and Monitoring: Use tools like Microsoft Entra Privileged Identity Management (PIM) to monitor privileged account activity.
License Requirements
Microsoft Entra ID Governance features are available across various licensing tiers, each catering to different organizational needs:
- Microsoft Entra ID P1: Covers basic identity governance, including self-service password resets and application management.
- Microsoft Entra ID P2: Includes advanced features like PIM, risk-based conditional access, and identity protection.
- Microsoft 365 E5: Provides the most comprehensive coverage, ideal for organizations with complex security needs.
Choosing the right tier depends on your organization’s size, compliance needs, and security requirements.
Getting Started with Microsoft Entra ID Governance
Implementing Entra ID Governance requires a clear roadmap:
- Understand Your Needs:
- Assess your organization’s requirements for identity and access management.
- Identify key applications and resources that need to be governed.
- Set Up Microsoft Entra ID:
- Make sure you have Microsoft Entra ID set up and configured for your organization.
- Familiarize yourself with its features and capabilities.
- Integrate Applications:
- Connect your cloud and on-premises applications using the available connectors.
- Utilize standards such as SCIM, SAML, and OpenID Connect for seamless integration.
- Configure Conditional Access:
- Define and enforce Conditional Access policies to ensure secure sign-in experiences.
- Set policies based on user, location, device, and risk factors.
- Automate Access Changes:
- Use Microsoft Entra lifecycle workflows to automate user access changes based on attribute modifications.
- Implement entitlement management to manage group memberships and access packages.
- Monitor and Audit:
- Regularly monitor access activities and audit compliance with governance policies.
- Use Microsoft Entra ID’s reporting tools to gain insights into access patterns and potential risks.
- Continuous Improvement:
- Continuously assess and refine your governance strategies.
- Stay updated with the latest features and best practices for identity governance.
Simplifying Identity Governance Tasks with Automation
Automating identity governance tasks can significantly enhance efficiency and security in your organization. Here’s how you can simplify these tasks with automation:
- Automated User Provisioning:
- Streamline the process of adding new users by automating user account creation, role assignment, and access provisioning.
- Utilize lifecycle workflows to handle changes in user status automatically.
- Dynamic Group Management:
- Use dynamic groups to automatically adjust group memberships based on user attributes such as department, location, or role.
- Ensure that users always have the right access without manual intervention.
- Entitlement Management:
- Implement entitlement management to automate the assignment and removal of access packages.
- Define policies that automatically grant and revoke access based on predefined conditions.
- Access Reviews and Certification:
- Schedule regular automated access reviews to ensure that users only have access to resources they need.
- Use automation to remind reviewers and collect feedback, streamlining the review process.
- Compliance and Reporting:
- Leverage automated reporting tools to generate compliance reports and audit trails.
- Automate the monitoring of policy violations and take corrective actions promptly.
- Conditional Access Policies:
- Configure Conditional Access policies to enforce security requirements dynamically based on user, location, device, and risk factors.
- Automate responses to detected risks, such as requiring multi-factor authentication or blocking access.
Conclusion
Microsoft Entra ID Governance offers a robust framework to manage identities and access efficiently. By focusing on lifecycle management, privileged access, licensing, and automation, organizations can bolster their security posture and streamline operations.
Whether you’re just starting or refining your governance strategy, Entra ID Governance provides the tools and features needed to succeed. Take the first step today—evaluate your current setup, identify gaps, and embrace the future of identity governance.
Stay tuned for more insights in our 30 Days of Azure Security series!

