Table of Contents
Introduction
In today’s interconnected world, hybrid cloud environments are increasingly becoming the norm for enterprises. The challenge of securing a hybrid environment that spans on-premises infrastructure and the cloud requires a comprehensive, adaptive security posture. As organizations move their workloads to the cloud, they continue to rely on legacy on-premises infrastructure, and protecting these hybrid environments becomes a complex task. Microsoft Defender for Identity is a key player in this security ecosystem, helping enterprises protect both on-premises and cloud-based identity systems.
According to a recent study by Gartner, 75% of security breaches in 2024 will involve identities or compromised credentials. In a hybrid environment, securing identities becomes a top priority as attackers increasingly target user credentials and privileged accounts as entry points for lateral movement within the organization.
Understanding Microsoft Defender for Identity
Microsoft Defender for Identity is a cloud-based security solution that helps secure your identity monitoring across your organization.
Defender for Identity is fully integrated with Microsoft Defender XDR, and leverages signals from both on-premises Active Directory and cloud identities to help you better identify, detect, and investigate advanced threats directed at your organization.
Deploy Defender for Identity to help your SecOps teams deliver a modern identity threat detection (ITDR) solution across hybrid environments, including:
- Prevent breaches, using proactive identity security posture assessments
- Detect threats, using real-time analytics and data intelligence
- Investigate suspicious activities, using clear, actionable incident information
- Respond to attacks, using automatic response to compromised identities
Protect user identities and reduce the attack surface
Defender for Identity provides you with invaluable insights on identity configurations and suggested security best-practices. Through security reports and user profile analytics, Defender for Identity helps dramatically reduce your organizational attack surface, making it harder to compromise user credentials, and advance an attack.
Proactively assess your identity posture
Defender for Identity provides you with a clear view of your identity security posture, helping you to identify and resolve security issues before they can be exploited by attackers.
For example:
- Defender for Identity’s Lateral Movement Paths help you quickly understand exactly how an attacker can move laterally inside your organization. Lateral movement paths can compromise sensitive accounts, and Defender for Identity helps you prevent those risks in advance.
- Defender for Identity security assessments, available from Microsoft Secure Score, provide extra insights to improve your organizational security posture and policies.
Detect threats across modern identity environments
Modern identity environments often span both on-premises and in the cloud. Defender for Identity uses data from across your environment, including domain controllers, Active Directory Federation Services (AD FS), and Active Directory Certificate services (AD CS), to provide you with a complete view of your identity environment.
Defender for Identity sensors monitor domain controller traffic by default. For AD FS / AD CS servers, make sure to install the relevant sensor type for complete identity monitoring.
Identify suspicious activities across the cyber-attack kill-chain
Typically, attacks are launched against any accessible entity, such as a low-privileged user. Attackers then quickly move laterally until they gain access to valuable assets, such as sensitive accounts, domain administrators, and highly sensitive data.
Defender for Identity identifies these advanced threats at the source throughout the entire cyber-attack kill chain:
| Threat | In Defender for Identity |
| Reconnaissance | Identify rogue users and attackers’ attempts to gain information. Attackers search for information about user names, users’ group membership, IP addresses assigned to devices, resources, and more, using various methods. |
| Compromised credentials | Identify attempts to compromise user credentials using brute force attacks, failed authentications, user group membership changes, and other methods. |
| Lateral movements | Detect attempts to move laterally inside the network to gain further control of sensitive users, utilizing methods such as Pass the Ticket, Pass the Hash, Overpass the Hash and more. |
| Domain dominance | View highlighted attacker behavior if domain dominance is achieved. For example, attackers might run code remotely on the domain controller, or use methods like DC Shadow, malicious domain controller replication, Golden Ticket activities, and more. |
For more information, see Security alerts in Microsoft Defender for Identity.
What’s new in Microsoft Defender for Identity
New security posture assessment: Prevent Certificate Enrollment with arbitrary Application Policies (ESC15)
In December 2024, Microsoft Defender for Identity has added the new Prevent Certificate Enrollment with arbitrary Application Policies (ESC15) recommendation in Microsoft Secure Score.
This recommendation directly addresses the recently published CVE-2024-49019, which highlights security risks associated with vulnerable AD CS configurations. This security posture assessment lists all vulnerable certificate templates found in customer environments due to unpatched AD CS servers.
The new recommendation is added to other AD CS-related recommendations. Together, these assessments offer security posture reports that surface security issues and severe misconfigurations that post risks to the entire organization, together with related detections.
MDI is expanding coverage with new 10 Identity posture recommendations (preview)
In October 2024, the new Identity security posture assessments (ISPMs) can help customers monitor misconfiguration by watching for weak spots and reduce the risk of potential attack on on-premises infrastructure.
These new identity recommendations, as part of Microsoft Secure Score, are new security posture reports related to Active Directory infrastructure and Group policy Objects:
- Accounts with non-default Primary Group ID
- Change Domain Controller computer account old password
- GPO assigns unprivileged identities to local groups with elevated privileges
- GPO can be modified by unprivileged accounts
- Reversible passwords found in GPOs
- Built-in Active Directory Guest account is enabled
- Unsafe permissions on the DnsAdmins group
- Ensure that all privileged accounts have the configuration flag “this account is sensitive and cannot be delegated”
- Change password of krbtgt account
- Change password of built-in domain Administrator account
Additionally, we updated the existing recommendation of “Modify unsecure Kerberos delegations to prevent impersonation” to include indication of Kerberos Constrained Delegation with Protocol Transition to a privileged service.
New Microsoft Entra Connect sensor:
In August 2024, as part of ongoing effort to enhance Microsoft Defender for Identity coverage in hybrid identity environments, Microsoft have introduced a new sensor for Microsoft Entra Connect servers. Additionally, Microsoft have released new hybrid security detections and new identity posture recommendations specifically for Microsoft Entra Connect, helping customers stay protected and mitigate potential risks.
New Microsoft Entra Connect Identity posture recommendations:
- Rotate password for Microsoft Entra Connect connector account
- A compromised Microsoft Entra Connect connector account (AD DS connector account, commonly shown as MSOL_XXXXXXXX) can grant access to high-privilege functions like replication and password resets, allowing attackers to modify synchronization settings and compromise security in both cloud and on-premises environments as well as offering several paths for compromising the entire domain. In this assessment we recommend customers change the password of MSOL accounts with the password last set over 90 days ago. For more information click here.
- Remove unnecessary replication permissions for Microsoft Entra Connect Account
- By default, the Microsoft Entra Connect connector account has extensive permissions to ensure proper synchronization (even if they aren’t actually required). If Password Hash Sync isn’t configured, it’s important to remove unnecessary permissions to reduce the potential attack surface. For more information click here
- Change password for Microsoft Entra seamless SSO account configuration
- This report lists all Microsoft Entra seamless SSO computer accounts with password last set over 90 days ago. The password for the Azure SSO computer account isn’t automatically changed every 30 days. If an attacker compromises this account, they can generate service tickets for the AZUREADSSOACC account on behalf of any user and impersonate any user in the Microsoft Entra tenant that is synchronized from Active Directory. An attacker can use this to move laterally from Active Directory into Microsoft Entra ID. For more information click here.
New Microsoft Entra Connect detections:
- Suspicious Interactive Logon to the Microsoft Entra Connect Server
- Direct logins to Microsoft Entra Connect servers are highly unusual and potentially malicious. Attackers often target these servers to steal credentials for broader network access. Microsoft Defender for Identity can now detect abnormal logins to Microsoft Entra Connect servers, helping you identify and respond to these potential threats faster. It’s specifically applicable when the Microsoft Entra Connect server is a standalone server and not operating as a Domain Controller.
- User Password Reset by Microsoft Entra Connect Account
- The Microsoft Entra Connect connector account often holds high privileges, including the ability to reset user’s passwords. Microsoft Defender for Identity now has visibility into those actions and will detect any usage of those permissions that were identified as malicious and non-legitimate. This alert will be triggered only if the password writeback feature is disabled.
- Suspicious writeback by Microsoft Entra Connect on a sensitive user
- While Microsoft Entra Connect already prevents writeback for users in privileged groups, Microsoft Defender for Identity expands this protection by identifying additional types of sensitive accounts. This enhanced detection helps prevent unauthorized password resets on critical accounts, which can be a crucial step in advanced attacks targeting both cloud and on-premises environments.
Additional improvements and capabilities:
- New activity of any failed password reset on a sensitive account available in the ‘IdentityDirectoryEvents’ table in Advanced Hunting. This can help customers track failed password reset events and create custom detection based on this data.
- Enhanced accuracy for the DC sync attack detection.
- New health issue for cases where the sensor is unable to retrieve the configuration from the Microsoft Entra Connect service.
- Extended monitoring for security alerts, such as PowerShell Remote Execution Detector, by enabling the new sensor on Microsoft Entra Connect servers.
In July, 6 New detections are new in public preview:
- Possible NetSync attack
- NetSync is a module in Mimikatz, a post-exploitation tool, that requests the password hash of a target device’s password by pretending to be a domain controller. An attacker might be performing malicious activities inside the network using this feature to gain access to the organization’s resources.
- Possible takeover of a Microsoft Entra seamless SSO account
- A Microsoft Entra seamless SSO (single sign-on) account object, AZUREADSSOACC, was modified suspiciously. An attacker might be moving laterally from the on-premises environment to the cloud.
- Suspicious LDAP query
- A suspicious Lightweight Directory Access Protocol (LDAP) query associated with a known attack tool was detected. An attacker might be performing reconnaissance for later steps.
- Suspicious SPN was added to a user
- A suspicious service principal name (SPN) was added to a sensitive user. An attacker might be attempting to gain elevated access for lateral movement within the organization
- Suspicious creation of ESXi group
- A suspicious VMWare ESXi group was created in the domain. This might indicate that an attacker is trying to get more permissions for later steps in an attack.
- Suspicious ADFS authentication
- A domain-joined account signed in using Active Directory Federation Services (ADFS) from a suspicious IP address. An attacker might have stolen a user’s credentials and is using it to move laterally in the organization.
Defender for Identity release 2.238
This version includes improvements and bug fixes for cloud services and the Defender for Identity sensor.
Easily Go Hunt For user Information From the ITDR Dashboard
In June 2024, the Shield Widget provides a quick overview of the number of users in hybrid, cloud, and on-premises environments. This feature now includes direct links to the Advanced Hunting platform, offering detailed user information at your fingertips.
ITDR Deployment Health Widget Now Include Microsoft Entra Conditional Access and Microsoft Entra Private Access
Now you can view the license availability for Microsoft Entra Workload Conditional Access, Microsoft Entra User Conditional Access, and Microsoft Entra Private Access.
Defender for Identity release 2.237
This version includes improvements and bug fixes for cloud services and the Defender for Identity sensor.
Microsoft Defender for Identity architecture
Microsoft Defender for Identity monitors your domain controllers by capturing and parsing network traffic, leveraging Windows events directly from your domain controllers, and then analyzes the data for attacks and threats.
The following image shows how Defender for Identity is layered over Microsoft Defender XDR, and works together with other Microsoft services and third-party identity providers to monitor traffic coming in from domain controllers and Active Directory servers.
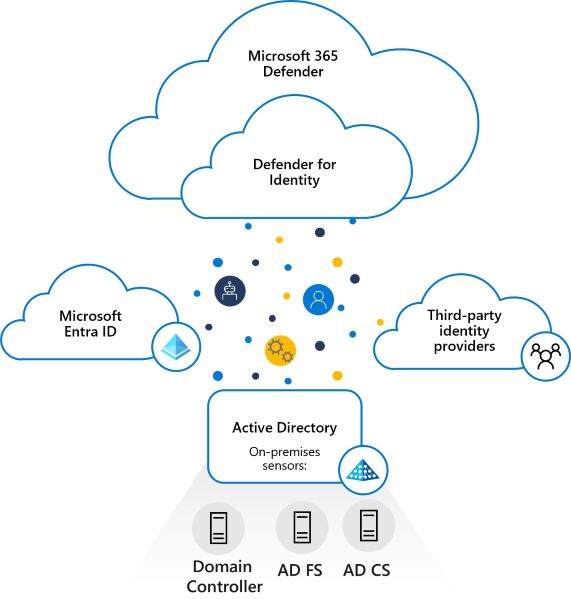
Installed directly on your domain controller, Active Directory Federation Services (AD FS), or Active Directory Certificate Services (AD CS) servers, the Defender for Identity sensor accesses the event logs it requires directly from the servers. After the logs and network traffic are parsed by the sensor, Defender for Identity sends only the parsed information to the Defender for Identity cloud service.
Defender for Identity components
Defender for Identity consists of the following components:
- Microsoft Defender portal
The Microsoft Defender portal creates your Defender for Identity workspace, displays the data received from Defender for Identity sensors, and enables you to monitor, manage, and investigate threats in your network environment. - Defender for Identity sensor Defender for Identity sensors can be directly installed on the following servers:
- Domain controllers: The sensor directly monitors domain controller traffic, without the need for a dedicated server, or configuration of port mirroring.
- AD FS / AD CS: The sensor directly monitors network traffic and authentication events.
- Defender for Identity cloud service
Defender for Identity cloud service runs on Azure infrastructure and is currently deployed in Europe, UK, Switzerland, North America/Central America/Caribbean, Australia East, Asia, and India. Defender for Identity cloud service is connected to Microsoft’s intelligent security graph.
Microsoft Defender portal
Use the Microsoft Defender portal to:
- Create your Defender for Identity workspace.
- Integrate with other Microsoft security services.
- Manage Defender for Identity sensor configuration settings.
- View data received from Defender for Identity sensors.
- Monitor detected suspicious activities and suspected attacks based on the attack kill chain model.
- Optional: The portal can also be configured to send emails and events when security alerts or health issues are detected.
Note
If no sensor is installed on your Defender for Identity workspace within 60 days, the workspace may be deleted and you’ll need to recreate it.
Defender for Identity sensor
The Defender for Identity sensor has the following core functionality:
- Capture and inspect domain controller network traffic (local traffic of the domain controller)
- Receive Windows Events directly from the domain controllers
- Receive RADIUS accounting information from your VPN provider
- Retrieve data about users and computers from the Active Directory domain
- Perform resolution of network entities (users, groups, and computers)
- Transfer relevant data to the Defender for Identity cloud service
Defender for Identity sensor reads events locally, without the need to purchase and maintain additional hardware or configurations. The Defender for Identity sensor also supports Event Tracing for Windows (ETW) which provides the log information for multiple detections. ETW-based detections include Suspected DCShadow attacks attempted using domain controller replication requests and domain controller promotion.
Domain synchronizer process
The domain synchronizer process is responsible for synchronizing all entities from a specific Active Directory domain proactively (similar to the mechanism used by the domain controllers themselves for replication). One sensor is automatically chosen at random from all of your eligible sensors to serve as the domain synchronizer.
If the domain synchronizer is offline for more than 30 minutes, another sensor is automatically chosen instead.
Resource limitations
The Defender for Identity sensor includes a monitoring component that evaluates the available compute and memory capacity on the server on which it’s running. The monitoring process runs every 10 seconds and dynamically updates the CPU and memory utilization quota on the Defender for Identity sensor process. The monitoring process makes sure the server always has at least 15% of free compute and memory resources available.
No matter what occurs on the server, the monitoring process continually frees up resources to make sure the server’s core functionality is never affected.
If the monitoring process causes the Defender for Identity sensor to run out of resources, only partial traffic is monitored and the health alert “Dropped port mirrored network traffic” appears in the Defender for Identity sensor page.
Windows Events
To enhance Defender for Identity detection coverage related to NTLM authentications, modifications to sensitive groups and creation of suspicious services, Defender for Identity analyzes the logs of specific Windows events.
To ensure that the logs are read, make sure that your Defender for Identity sensor has advanced audit policy settings configured correctly. To make sure that Windows Event 8004 is audited as needed by the service, review your NTLM audit settings
Real-World Best Practices in Protecting Hybrid Environments
1. Extend Protection to Hybrid Identity with Entra ID Connect
When securing a hybrid environment, the integration of on-premises Active Directory with Entra ID via Entra ID Connect is the foundational element. Entra ID Connect synchronizes user identities, groups, and other directory objects between on-premises AD and Entra ID, enabling single sign-on (SSO) and seamless identity management across both environments.
Best Practice: Always ensure that Entra ID Connect Health is actively monitoring synchronization and sign-in activities. In addition, enable Microsoft Defender for Identity to monitor events on both your on-premises AD and Entra ID. This provides a unified threat detection mechanism across both environments.
Example: Suppose an attacker gains access to your Entra ID tenant using a stolen credential. If Microsoft Defender for Identity is integrated with Entra ID Connect, it will monitor signs of malicious activity such as unusual logins or lateral movement, regardless of whether the action originates from the cloud or on-premises.
2. Leverage Risk-Based Conditional Access Policies
Conditional Access is a powerful tool that controls access to your resources based on specific conditions, such as user risk, location, device health, and more. Leveraging Microsoft Defender for Identity in tandem with Conditional Access enables dynamic risk-based decision-making. When Microsoft Defender for Identity detects suspicious activities like unusual logins or impossible travel events, it can trigger policies that block access or require additional authentication factors.
Best Practice: Implement a Zero Trust security model where access is never assumed, and access rights are continuously validated using real-time risk signals from Microsoft Defender for Identity. Conditional Access policies should be fine-tuned to enforce multi-factor authentication (MFA) or enforce access restrictions based on the security risk profile of users.
Scenario: Consider a scenario where a user logs in from an unusual geographic location that contradicts their typical login patterns. Microsoft Defender for Identity detects this anomaly and automatically triggers a Conditional Access policy requiring MFA before granting access to sensitive data.
3. Monitor Lateral Movement and Privilege Escalation
Lateral movement and privilege escalation are critical indicators of advanced persistent threats (APTs). Attackers often move across systems within the network once they compromise a low-level account, seeking higher-privilege accounts. Microsoft Defender for Identity is adept at detecting these types of activities in hybrid environments by analyzing user behavior and network traffic.
Best Practice: Regularly monitor for lateral movement and privilege escalation patterns by analyzing alerts generated by Microsoft Defender for Identity. Use Azure Sentinel to aggregate these alerts and correlate them with other security data for a more comprehensive threat detection strategy.
Example: An attacker may initially compromise a standard user account but then attempt to move laterally by exploiting a vulnerability or weak password in the on-premises domain. Microsoft Defender for Identity can flag abnormal privilege escalation attempts, providing early detection before the attacker gains domain administrator rights.
4. Utilize Built-In Threat Intelligence and Integrate with Azure Sentinel
Microsoft Defender for Identity uses built-in threat intelligence to help security teams detect emerging threats. It combines internal telemetry with Microsoft’s vast global data sources to identify attack patterns such as credential stuffing, pass-the-ticket, and Golden Ticket attacks. Integrating Microsoft Defender for Identity with Azure Sentinel allows security teams to automate incident response and threat hunting processes.
Best Practice: Build automated response playbooks in Azure Sentinel using the alerts and detections from Microsoft Defender for Identity. This integration can help accelerate threat containment by automatically isolating compromised accounts or triggering alerts to security operations teams.
Scenario: During a routine security assessment, Microsoft Defender for Identity flags an attempt to create a Golden Ticket, a classic sign of an advanced attack. By integrating with Azure Sentinel, the response playbook automatically disables the compromised accounts and triggers a detailed forensic investigation, reducing the time to containment.
5. Protect Critical Assets with Microsoft Defender for Identity Insights
Microsoft Defender for Identity also allows you to protect your most sensitive assets by providing deeper insights into how users and devices are interacting with these resources. By enabling monitoring for high-value targets like privileged accounts, you can detect if they are being targeted by attackers.
Best Practice: Enable Identity Protection to monitor risk levels for privileged accounts such as administrators, service accounts, and highly sensitive resources. Use Microsoft Defender for Identity’s threat detection capabilities to understand the patterns and activities that pose the greatest risk to critical assets.
Example: If an attacker compromises a privileged account and starts accessing high-value resources, Microsoft Defender for Identity will flag this behavior and prompt you to take immediate action, such as locking the account or requiring a password reset.
6. Establish Clear Governance and Incident Response Procedures
While Microsoft Defender for Identity can detect threats, it is equally important to establish governance policies for how incidents are handled. Your incident response plan should include guidelines on who will respond to Microsoft Defender for Identity alerts, how to escalate high-priority threats, and the communication procedures with other security teams.
Best Practice: Create a detailed incident response workflow that involves Microsoft Defender for Identity, Azure Security Center, and Microsoft Sentinel. Ensure all security teams understand their roles in responding to different types of alerts and incidents.
Scenario: An administrator receives an alert from Microsoft Defender for Identity about suspicious login attempts from an internal user account. The incident response plan should define the steps to validate the alert, whether to block the account immediately, and how to notify the security operations team for further investigation.
Conclusion
Microsoft Defender for Identity is a critical tool for securing hybrid environments by offering comprehensive protection against a wide range of identity-based threats. By leveraging its advanced threat detection capabilities, integrating with other Azure security services, and following best practices in monitoring, risk-based access control, and automated response, enterprises can significantly improve their security posture and reduce the risk of identity-related attacks.
Security professionals should continuously evolve their identity protection strategies, taking advantage of the insights and alerts from Microsoft Defender for Identity to identify vulnerabilities, mitigate risks, and safeguard their hybrid environments effectively.
FAQs
Q1: How does Microsoft Defender for Identity work with cloud-only environments?
Microsoft Defender for Identity is designed to protect both on-premises and cloud-based identities. While it primarily focuses on on-premises Active Directory, it also integrates with Entra ID to detect suspicious activity, providing holistic protection across hybrid environments.
Q2: Can Microsoft Defender for Identity help prevent insider threats?
Yes, Microsoft Defender for Identity is particularly useful for detecting insider threats. By monitoring user behavior, it can identify abnormal patterns, privilege escalation attempts, or lateral movement that could signal malicious activities from internal users.
Q3: How does Microsoft Defender for Identity integrate with third-party solutions?
Microsoft Defender for Identity integrates with other Azure services like Azure Sentinel, Microsoft Defender for Endpoint, and Azure Security Center. You can also extend its functionality by using APIs or leveraging third-party SIEM systems for further analysis.
Q4: What is the impact of deploying Microsoft Defender for Identity on my infrastructure?
Microsoft Defender for Identity operates with minimal overhead, as it analyzes existing logs and network traffic without the need for additional agents or hardware. It can scale easily to protect environments of varying sizes, from small businesses to large enterprises.
Q5: How often should Microsoft Defender for Identity alerts be reviewed?
Alerts generated by Microsoft Defender for Identity should be reviewed regularly, especially for high-severity incidents. Ideally, they should be integrated with a SIEM solution like Azure Sentinel to ensure automated tracking and response, enabling security teams to act swiftly on high-priority threats.
Stay tuned for more insights in our 30 Days of Azure Security series!

