Table of Contents
Introduction to Splunk

Hello, everyone! Today, we’re going to talk about a fascinating tool called Splunk. Imagine Splunk as a super smart detective that helps us solve mysteries hidden within data. Have you ever seen detectives in movies piecing together clues to solve a crime? Well, Splunk does something similar, but with data instead of crime scenes.
Understanding Data and Logs:
Okay, let’s start with some basics. Think of data as puzzle pieces, and logs as a special kind of puzzle that computers create when they do things. These logs are like a trail of breadcrumbs left behind whenever something happens on a computer, like when you log into your email or visit a website.

Key Concepts of Splunk:
Now, let’s talk about what makes Splunk so special. Imagine you have a giant pile of puzzle pieces (data), and you need to find the ones that fit together to create a picture (information). Splunk helps us find those puzzle pieces, put them together, and make sense of the bigger picture.
Components of Splunk:
Imagine Splunk as a team of detectives working together to solve a case. The Search Head is like the chief detective, who looks for clues and directs the investigation. The Indexer is like a filing system that organizes the clues neatly, so the detectives can find them quickly. The Forwarder is like a messenger that brings new clues to the team. To learn more about the components of Splunk, click here.
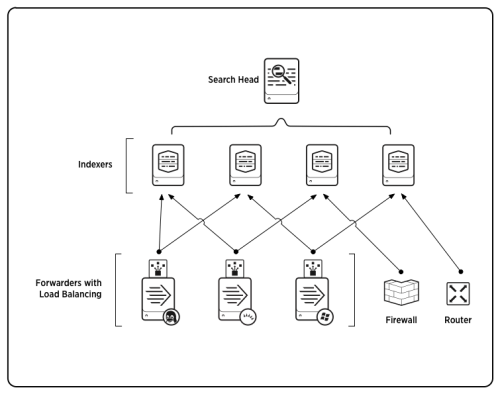
Data Collection and Indexing:
Let’s say you’re planning a party and want to keep track of who’s coming. Your friends send you messages with their names and their favorite party foods. The Forwarder collects these messages and brings them to you. Then, you use the Indexer to sort the messages based on names, making it easier to find who’s bringing what.
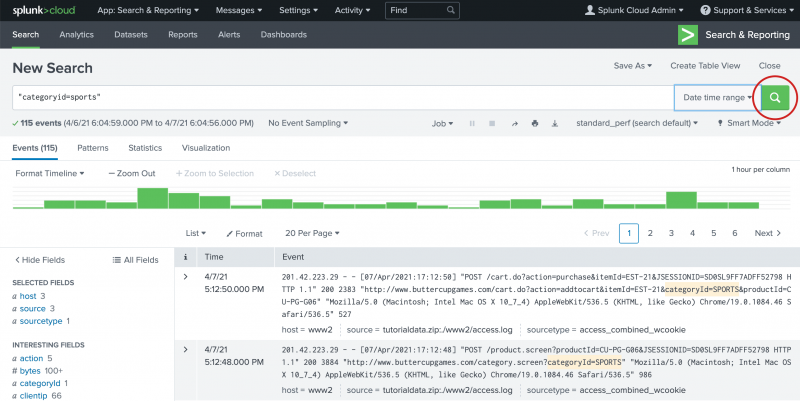
Searching Data in Splunk:
Now, imagine you’re trying to find out who ate all the cookies at your party. You use Splunk’s special language (SPL) to search through the messages and find out who mentioned cookies. In a real-world example, a company could use Splunk to search for patterns in computer logs to find out if someone is trying to break into their systems. To learn more about searching data in Splunk, click here
Creating Visualizations:
Let’s get creative! Imagine you want to show how many cupcakes each of your friends ate at the party. Splunk can take the information from the messages and create a colorful graph or chart that makes it easy to see who had the most cupcakes.
Use Cases in Cybersecurity:
Now, let’s talk about how Splunk helps in a more serious scenario – cybersecurity. Imagine you have a virtual castle that stores important information. Splunk acts like guards who watch the castle’s walls for any suspicious activity. If someone tries to sneak in or do something strange, Splunk alerts the guards so they can stop the intruder.
Real-world Scenario: Detecting Malicious Activity:
Imagine you’re playing an online game, and someone is cheating by using special tricks. Splunk is like a referee who watches all the players closely. If it sees someone doing something fishy, it can pause the game and investigate what’s going on.
Benefits and Challenges:
Think of Splunk as a super helpful tool that makes sense of data, even if you’re not a computer expert. However, setting up Splunk and understanding all its features might be a bit like learning a new game. Just like games, with practice, it gets easier!
Future of Splunk and Career Opportunities:
Splunk is always getting smarter and learning new tricks. If you enjoy solving puzzles and want to be a part of the digital detective team, there are exciting career opportunities using Splunk to keep information safe and catch bad guys.
So, there you have it – Splunk, the magical detective tool that turns data into stories, making it easy for anyone to understand and explore!
