In the intricate realm of cybersecurity, where threats lurk and data flows incessantly, a formidable ally emerges in the form of the Kusto Query Language (KQL). Donning the hat of a cyber security instructor, I’m here to guide you through the nuances of this enigmatic language in a manner that’s accessible and comprehensible to all, regardless of your technical background.
Table of Contents
Introduction to Kusto Query Language (KQL) for Cyber Security
Hello everyone! Today, we’re going to dive into the world of cyber security and explore a powerful tool called the Kusto Query Language, or KQL for short. Don’t worry if you’re not a tech expert; I’ll explain everything in simple terms so you can grasp the concept easily. To learn more about KQL click here.
What is Kusto Query Language (KQL)?
Kusto Query Language (KQL) is a special language designed to help you analyze large sets of data quickly and efficiently. It’s like a detective tool for cyber security professionals, helping them find clues and insights hidden in mountains of data. Think of it as a way to ask questions about your data and get meaningful answers.
Picture this: you’re a guardian of digital fortresses, tasked with safeguarding an organization’s digital realm from the relentless onslaught of cyber adversaries. In your arsenal of tools, Kusto Query Language stands as a beacon of insight, enabling you to navigate and analyze vast troves of data with finesse. KQL, often referred to as the “Kusto” language, bears the name of the data platform that birthed it – Azure Data Explorer, previously known as “Project Kusto.” At its core, KQL is a query language tailor-made for querying massive datasets swiftly and intelligently. It’s akin to a digital detective’s magnifying glass, aiding cybersecurity professionals in unearthing hidden clues and extracting meaningful insights from oceans of data.
The Role of KQL in Cyber Security
In the world of cybersecurity, data is king. We have information flowing from various sources, like computer systems, networks, and software applications. This data tells us about user activities, potential attacks, and system behavior. But here’s the challenge: how do we make sense of this massive amount of data? This is where KQL steps in. It’s like a superpower that allows us to search, filter, and analyze this data so we can find patterns, anomalies, and signs of trouble.
Getting Acquainted with KQL: A Step-by-Step Guide
Imagine you’re a cybersecurity analyst on a mission to find any signs of unauthorized access on your company’s network. Let’s embark on a journey through the steps of using KQL to accomplish this task.
Step 1: Understanding Your Data Source
Before we dive into KQL, we need to know where our data comes from. In the cybersecurity world, we have tools and systems that collect data from different sources, like firewalls, servers, and user devices. This data is stored in a special place for analysis. Think of it as your detective’s evidence locker.
Step 2: Formulating Your First Query
Now, let’s write our first KQL query. Imagine you want to check if there have been any failed attempts to log into your organization’s systems. Here’s how you would write the query:
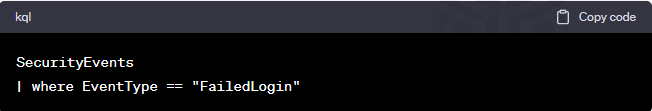
Let’s break it down:
SecurityEvents is like the table in your evidence locker where all security-related events are stored.
| is a pipeline that connects different parts of the query.
where EventType == “FailedLogin” is like a filter that tells the system to only show events where someone tried and failed to log in.
Step 3: Executing Your Query
With your query written, it’s time to put it into action. You send your query to the system, and it starts looking through the data for events that match your criteria. In this case, the system finds events where login attempts failed.
Step 4: Analyzing the Results
As the results come in, you’re presented with a list of events where login attempts failed. Now, this is where your detective skills come into play. You might notice patterns, like the same username trying to log in from different locations. Or you might spot an unusual IP address that’s attempting multiple failed logins. These could be signs of a hacker trying to break in.
Real-Life Scenario: The Intrusion Attempt
Imagine you run your query, and it shows a series of failed login attempts from an unfamiliar IP address. These attempts occurred in the middle of the night and targeted multiple user accounts. This raises a red flag – it seems like an intrusion attempt, where someone is trying to gain unauthorized access to your systems.
The Power of KQL: Beyond the Basics
Now that you’ve glimpsed the basics of KQL, know that it can do much more than just find failed logins. It’s like having a cyber Swiss Army knife at your disposal. You can use KQL to track user behavior over time, identify trends in attacks, and even predict potential threats. It’s a tool that empowers you to understand the digital landscape and take proactive steps to defend against cyber risks.
Conclusion: The Journey of Cyber Sleuths
As we conclude our exploration of the Kusto Query Language (KQL) in the realm of cybersecurity, remember that you’ve embarked on a journey of cyber sleuthing. KQL is your key to deciphering the intricate code of data and extracting insights that can make all the difference in safeguarding digital landscapes. So whether you’re a curious beginner or an aspiring cyber warrior, KQL is your partner in unraveling the mysteries of the digital world. Armed with KQL, you’re equipped to become a defender of the digital realm, unearthing threats and fortifying your organization against the ever-evolving landscape of cyber challenges.
if you are interested to learn fundamental of Splunk please click here.
