If you are an IT student or fresher and want to know how to configure MFA in Azure, this is the right place. Multi-factor authentication (MFA) is an additional security measure that requires users to enter two or more factors of authentication when logging in to their accounts. This helps to protect accounts from unauthorized access, even if the attacker has the user’s password.
Azure Active Directory (Azure AD) provides a number of different MFA methods, including:
- Authenticator apps: Authenticator apps generate a one-time code that the user must enter when logging in.
- Phone calls: The user receives a phone call with a one-time code that they must enter when logging in.
- SMS: The user receives an SMS message with a one-time code that they must enter when logging in.
- Security keys: Security keys are physical devices that generate a one-time code when pressed.
Table of Contents
Why should you use MFA?
MFA is an important security measure that can help protect your accounts from unauthorized access. Even if an attacker has your password, they will not be able to log in without your second factor of authentication.
MFA is especially important for businesses and organizations, as it can help protect sensitive data from being compromised.
Benefits of using MFA in Azure
There are a number of benefits to using MFA in Azure, including:
- Improved security: MFA helps to protect your accounts from unauthorized access, even if the attacker has your password.
- Reduced risk of data breaches: MFA can help reduce the risk of data breaches by making it more difficult for attackers to gain access to your systems and data.
- Compliance with regulations: Many regulations require businesses and organizations to implement MFA to protect their data
How to configure MFA in Azure
To configure MFA in Azure AD, follow these steps:
Step 1: Access Azure Portal
- Log in to the Azure portal using your administrative credentials.

Step 2: Navigate to Azure Active Directory
- In the Dashboard, go to search and type “Azure Active Directory”.
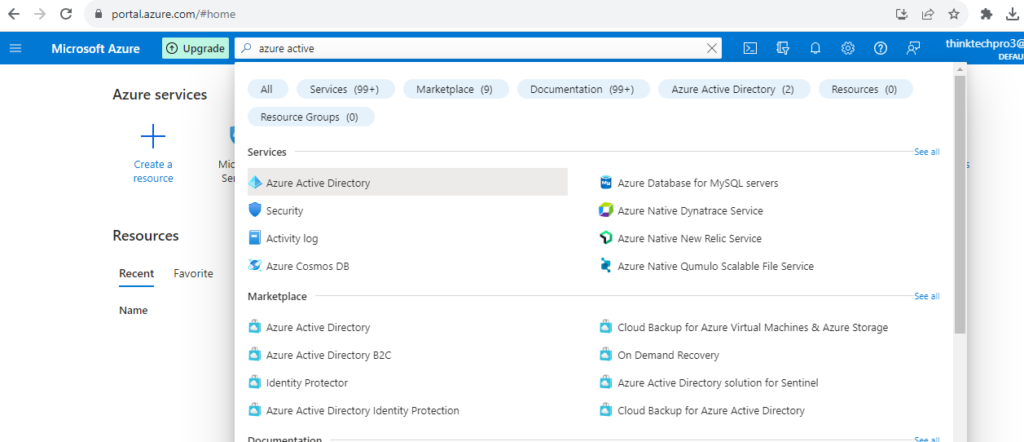
Step 3: Configure MFA
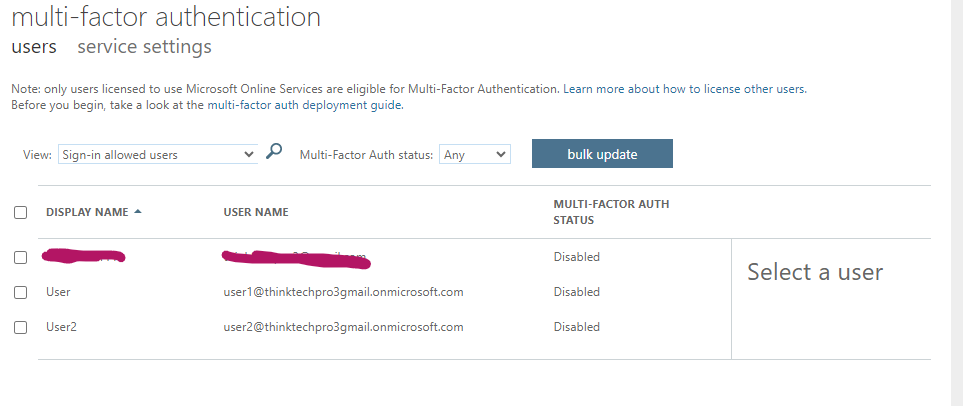
- In the Azure AD menu, click on “Users” and then “Per user MFA.”


2. A new window will open with options to enable MFA.
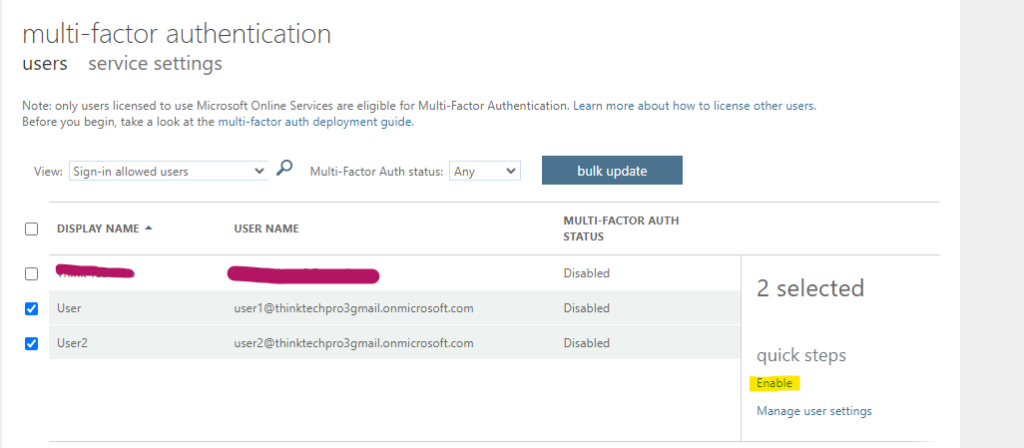
3. In the “Multi-Factor Authentication” page, select the users you want to enable MFA for (e.g., all users, or selected users) and click “enable multi-factor auth”.
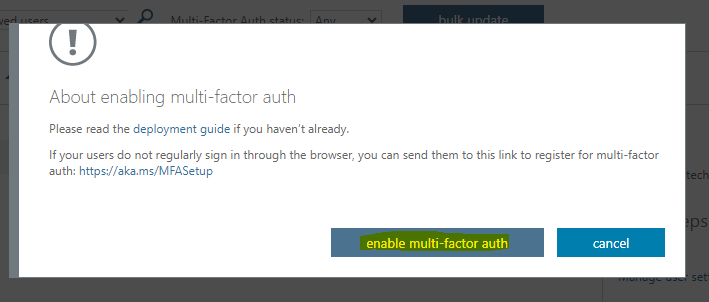

5. MFA is now enabled to user, now we need to configure MFA. Go to “Azure AD”, click on “Users” and select and click on user name, here we select “user1”
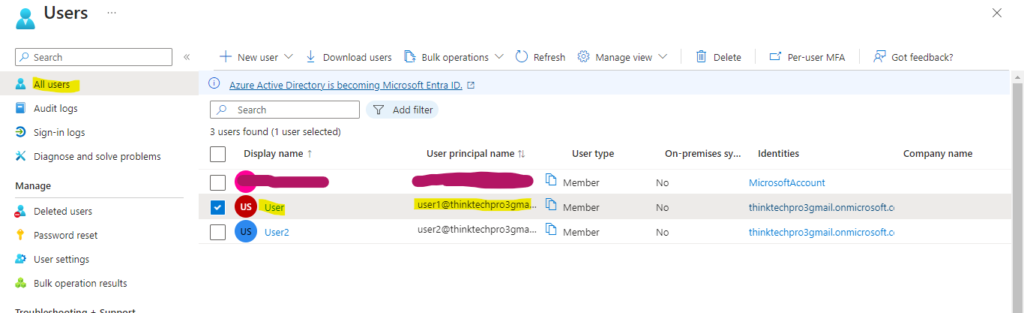
6. A new window will open. Click “Authentication Methods,” then provide your phone no or email address and click on “required re-register multifactor authentication”

7. Click “Save” to apply the changes.
Step 4: Notify Users
1. Inform the affected users about the upcoming MFA implementation and provide them with instructions on setting up MFA on their accounts.
2. Consider providing training materials or guidance to help users understand the MFA setup process.
Additional tips for configuring MFA in Azure
Here are some additional tips for configuring MFA in Azure:
- Roll out MFA gradually. Don’t try to enable MFA for all of your users at once. Start by enabling MFA for a small group of users, such as administrators and other high-value targets. Once you have verified that MFA is working properly, you can roll it out to the rest of your users.
- Communicate with your users. Let your users know that MFA is being enabled and explain why it’s important. Also, provide them with instructions on how to set up and use MFA.
- Use a variety of MFA methods. Not all MFA methods are created equal. Some methods, such as SMS, are less secure than others. Consider using a variety of MFA methods to give your users more flexibility and to improve security.
- Monitor your MFA usage. Azure AD provides reports that can help you to monitor your MFA usage. This information can be used to identify users who are not using MFA and to troubleshoot any problems that may occur.
Best practices for using MFA in Azure
Here are some best practices for using MFA in Azure:
- Require MFA for all users. All users, including administrators and privileged users, should be required to use MFA.
- Use strong MFA methods. Recommend that users use strong MFA methods, such as authenticator apps or security keys.
- Enforce MFA for all applications. Require MFA for all applications, including cloud-based applications and on-premises applications.
- Monitor MFA usage. Regularly review MFA usage reports to identify users who are not using MFA and to troubleshoot any problems that may occur.
By following these best practices, you can help to ensure that your users are using MFA correctly and that your organization is protected from unauthorized access.
FAQs for how to configure MFA in Azure
Q: What is MFA?
A: MFA is an additional security measure that requires users to enter two or more factors of authentication when logging in to their accounts. This helps to protect accounts from unauthorized access, even if the attacker has the user’s password.
Q: Why should I use MFA?
A: MFA is an important security measure that can help to protect your accounts from unauthorized access, even if the attacker has your password. MFA is especially important for businesses and organizations, as it can help to protect sensitive data from being compromised.
Q: What are the different types of MFA methods?
A: Azure AD provides a number of different MFA methods, including:
- Authenticator apps: Authenticator apps generate a one-time code that the user must enter when logging in.
- Phone calls: The user receives a phone call with a one-time code that they must enter when logging in.
- SMS: The user receives an SMS message with a one-time code that they must enter when logging in.
- Security keys: Security keys are physical devices that generate a one-time code when pressed.
Q: How do I choose the right MFA method for me
A: When choosing an MFA method, you should consider the following factors:
- Enhanced Security: When it comes to MFA methods, the level of security can vary significantly. For instance, security keys offer a higher level of security compared to SMS authentication.
- Convenience: Some MFA methods are more convenient to use than others. For example, authenticator apps are more convenient to use than phone calls.
- Cost: Some MFA methods are more expensive than others. For example, security keys are more expensive than SMS.
Q: How to configure MFA in Azure?
A: To configure MFA in Azure AD, follow these steps:
- Sign in to the Azure portal.
- Click Azure Active Directory.
- Click Security.
- Click Multi-factor authentication.
- Click Enabled.
- Select the MFA methods that you want to use.
- Click Save.
Once you have enabled MFA, users will be required to enter a one-time code from their chosen MFA method when logging in to their Azure AD accounts.
Q: How do I roll out MFA to my users?
A: You can roll out MFA to your users in a number of ways. One way is to enable MFA for a small group of users, such as administrators and other high-value targets. Once you have verified that MFA is working properly, you can roll it out to the rest of your users.
Another way to roll out MFA is to use a staged rollout approach. In this approach, you would enable MFA for a subset of your users each week or month. This approach can help to minimize disruption to your users.
Q: How do I communicate with my users about MFA?
A: It is important to communicate with your users about MFA before you enable it. You should explain why MFA is important and how it will benefit them. You should also provide them with instructions on how to set up and use MFA.
Q: How do I monitor MFA usage?
A: Azure AD provides reports that can help you to monitor your MFA usage. This information can be used to identify users who are not using MFA and to troubleshoot any problems that may occur.
Q: What are the best practices for using MFA?
- Require MFA for all users, including administrators and privileged users.
- Use strong MFA methods, such as authenticator apps or security keys.
- Enforce MFA for all applications, including cloud-based applications and on-premises applications.
- Monitor MFA usage regularly.

