Today we are going to learn the top common questions about ADFS, along with detailed explanations. I hope this will help you get more clarity to understand ADFS.

Table of Contents
Common Questions about ADFS
What is the purpose of ADFS?
ADFS serves as a security token service (STS) in Microsoft’s identity and access management ecosystem. Its primary purpose is to enable Single Sign-On (SSO) and federated identity authentication across different systems, both within and outside an organization’s network. ADFS allows users to access various applications and services with a single set of credentials, enhancing the user experience and security.
What are the drawbacks of using ADFS?
Active Directory Federation Services (ADFS) offers single sign-on and identity federation but has drawbacks. It’s complex and costly to deploy and maintain, especially for high availability. ADFS is more suited to on-premises setups, making cloud migration complex. SSL certificate management and customization via claims rules can be cumbersome. Integration with some apps and services may be challenging. It requires skilled personnel for operations. Moreover, ADFS might introduce latency for external users and scalability limits for large organizations. It also ties organizations to Microsoft technology, posing vendor lock-in risks. Despite these limitations, ADFS can be valuable for specific on-premises infrastructure needs when managed diligently.
How does ADFS achieve Single Sign-On (SSO)?
ADFS achieves SSO by issuing security tokens containing user claims (attributes) when users authenticate. These tokens are presented to applications, allowing them to trust and authenticate users without requesting credentials again.
How does ADFS work at a technical level?
ADFS uses standards like Security Assertion Markup Language (SAML) and WS-Federation to facilitate identity federation. When a user attempts to access a federated application, ADFS acts as an identity provider (IdP). It issues security tokens containing user claims, which are then presented to the application’s relying party (RP) for authentication. The RP trusts ADFS and accepts the token, granting or denying access accordingly.
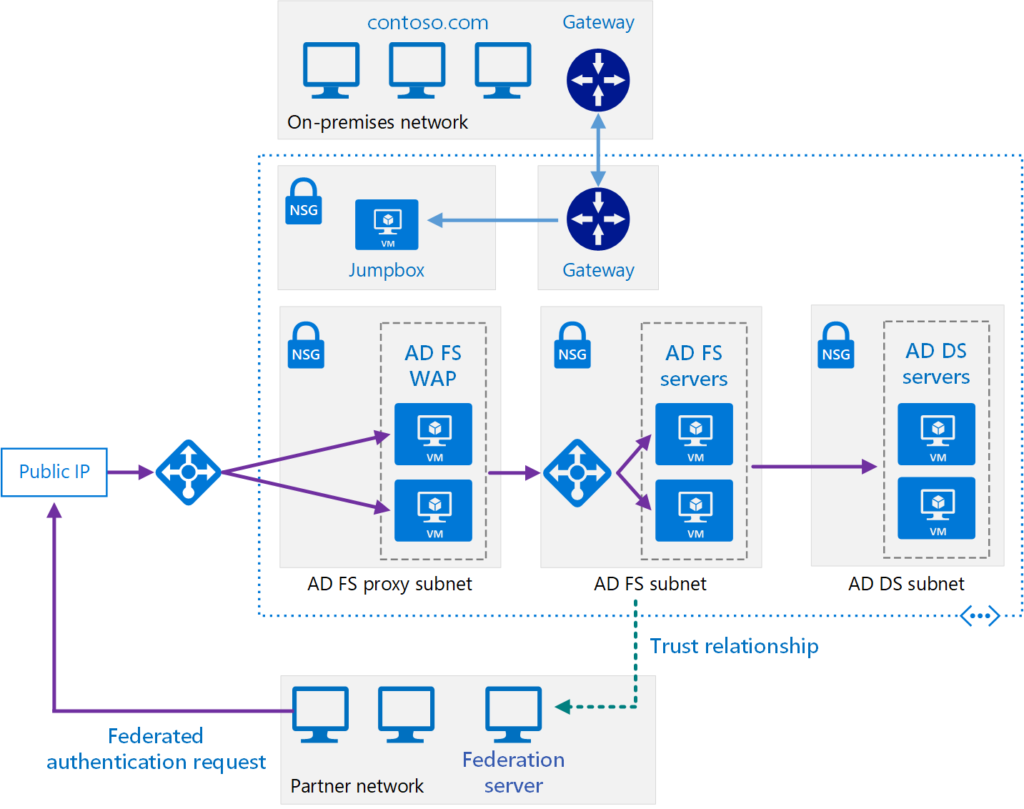
What are the key components of ADFS Architecture?
ADFS consists of several key components:
ADFS Server: The core ADFS service running on Windows Server
ADFS Proxy (Web Application Proxy, WAP): Used for external access and publishing ADFS services securely.
Federation Service: Manages authentication requests and token issuance.
Relying on Party Trusts: Define trust relationships with external applications.
Claims Rules: Determine what claims (user attributes) are included in issued tokens.
Token Signing and Encryption: Protects token integrity and confidentiality.
What authentication protocols does ADFS support?
ADFS supports authentication using standards like Security Assertion Markup Language (SAML), WS-Federation, and OpenID Connect. These protocols enable ADFS to federate identities with different systems and platforms.
What is the role of claims in ADFS?
Claims are user attributes (e.g., username, email, role) that ADFS includes in security tokens. They provide information about the user, which applications can use for authorization and personalization. Claims are managed through claims rules.
What are common troubleshooting challenges with ADFS?
Common issues include certificate problems (expiry, mismatch), misconfigured trust relationships, network connectivity issues, firewall problems, and incorrect claims rules. In-depth troubleshooting involves reviewing logs, analyzing token issuance, and verifying configurations.
How can I secure ADFS communication with external partners?
You can secure ADFS communication by implementing HTTPS (port 443) and ensuring that SSL certificates are valid and properly configured. You can also use ADFS Proxy (WAP) servers in a DMZ to publish ADFS services externally while protecting your internal network.
Can ADFS be used with multi-factor authentication (MFA)?
Yes, ADFS can integrate with MFA solutions to enhance security. It supports MFA through mechanisms like Azure Multi-Factor Authentication (MFA) or third-party MFA providers. MFA strengthens the authentication process by requiring multiple forms of verification.
How does ADFS handle user attributes and claims?
ADFS uses claims-based authentication, where it issues security tokens containing claims (user attributes) that applications can use for authorization. Claims rules are configured to transform and pass specific attributes to the relying party. Claims can include user roles, email addresses, or custom attributes.
How can ADFS be used with Azure and Office 365?
ADFS can be used to enable SSO for Microsoft Azure and Office 365. By federating with Azure AD, users can use their on-premises credentials to access cloud services, enhancing user convenience and security.
Is ADFS expensive?
ADFS requires a Windows Server license to deploy. However, the cost of ADFS can be offset by the benefits it offers, such as improved security and reduced user support costs.
Is ADFS compatible with other identity providers?
ADFS can be used with a variety of identity providers, including Microsoft Azure Active Directory, Google, and Okta. This makes it easy to federate your organization’s Active Directory domain with other identity providers.
How can I troubleshoot common ADFS issues?
Troubleshooting ADFS issues may involve diagnosing certificate problems, trust relationship misconfigurations, network connectivity issues, firewall settings, and examining ADFS logs. A systematic approach is essential to identifying and resolving issues.
What are the alternatives to ADFS for federated authentication?
Alternatives include Azure Active Directory (Azure AD) for cloud-centric federated authentication, OpenID Connect for web-based SSO, and third-party identity providers like Okta or Ping Identity. The choice depends on your organization’s needs and infrastructure.
What are the security best practices for ADFS?
Security practices include using trusted SSL certificates, regular certificate renewal, proper firewall configurations, monitoring ADFS logs for security events, implementing strong password policies, and conducting periodic security audits and penetration tests.
How do I set up high availability for ADFS?
Achieving high availability involves deploying multiple ADFS servers on a farm behind a load balancer. Configure database replication, use network load balancing, and ensure that service accounts and certificates are synchronized across ADFS servers. Regularly test failover scenarios to validate the setup.
Have more burning questions about ADFS that you’d like us to answer? Feel free to leave your comments below, and we’ll provide you with even more insights and solutions!

