Welcome to Day 10 of our “30 Days of Azure Security” series! Today, we dive deep into Azure Network Security, a fundamental pillar of building robust and secure cloud environments. Networking in Azure is not just about connecting resources but also about ensuring that these connections are secure and resilient. In this post, we’ll explore critical aspects of Azure Network Security, providing insights for Cloud Security Engineers, Azure Security Engineers, and Cybersecurity professionals.
Table of Contents
The Growing Threat Landscape
Cloud-based attacks are on the rise. Data from cybersecurity firms shows that:
- Over 80% of organizations have experienced at least one cloud security breach.
- DDoS attacks increased by over 200% in recent years.
- Ransomware attacks targeting cloud environments have grown by 150%.
These statistics highlight the urgent need for effective cloud security strategies.
The Importance of Proactive Security
Reactive measures often lead to costly consequences. Organizations that wait until after an attack to act find themselves facing:
- Significant financial losses.
- Damage to reputation.
- Legal issues due to data breaches.
Investing in proactive strategies results in a safer environment at a lower cost.
What is an Azure Virtual Network (VNet)?
An Azure Virtual Network (VNet) is the backbone of networking in Azure. It enables organizations to create isolated networks in the cloud, ensuring secure communication between Azure resources and hybrid connectivity with on-premises environments.
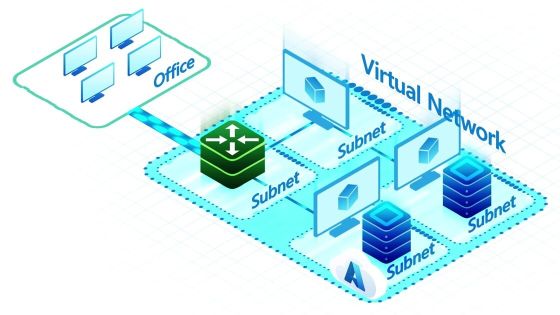
Key features of VNets include:
- Segmentation: Organize resources into subnets for better security and traffic management.
- Hybrid Connectivity: Connect VNets to on-premises networks using VPNs or Azure ExpressRoute.
- Custom Routing: Leverage system routes and User-Defined Routes (UDRs) to control traffic flow.
Think of VNets as secure containers that provide the foundation for your cloud networking infrastructure.
Plan and Implement Azure Network Security Groups (NSGs) and Application Security Groups (ASGs)
Network Security Groups (NSGs)
NSGs act as a virtual firewall, controlling inbound and outbound traffic to Azure resources. They operate at both the subnet and NIC levels and enforce security through rules defined by:
- Source and destination IP addresses.
- Port ranges.
- Protocols (e.g., TCP/UDP).
Best Practices for NSGs:
- Deny by Default: All traffic should be denied unless explicitly allowed.
- Layered Security: Apply NSGs at both subnet and NIC levels for defense-in-depth.
- Regular Audits: Periodically review rules to ensure they align with security policies.
Application Security Groups (ASGs)
ASGs simplify security management by allowing you to group resources with similar security needs. Instead of assigning rules to IP addresses, you can associate ASGs with NSG rules for dynamic and scalable configurations.
Example: Group VMs by application roles (e.g., web servers, database servers) and define rules based on ASGs rather than individual IPs.
Plan and Implement User-Defined Routes (UDRs)
By default, Azure provides system routes for traffic flow. However, User-Defined Routes (UDRs) give you the flexibility to override default routing behavior, allowing:
- Routing traffic through virtual appliances like firewalls or proxies.
- Implementing forced tunneling for internet-bound traffic.
Steps to Implement UDRs:
- Create a route table in Azure.
- Add custom routes with specified destinations and next-hop types (e.g., virtual appliances, internet, or on-premises).
- Associate the route table with a subnet.
Use Case: Direct all traffic from a specific subnet to a Network Virtual Appliance (NVA) for traffic inspection and logging.
Plan and Implement Virtual Network Peering or Gateway
VNet Peering
VNet Peering connects two VNets, enabling seamless communication. It’s useful for:
- Expanding networks across regions.
- Enabling resource sharing between VNets.
Benefits of VNet Peering:
- Low latency and high bandwidth.
- No need for a public IP address.
Gateway Connections
Gateways are essential for hybrid connectivity, providing secure connections between Azure and on-premises networks. Two common types are:
- VPN Gateway: Supports encrypted communication using IPsec/IKE protocols.
- ExpressRoute Gateway: Offers high-speed private connections via service providers.
Secure VPN Connectivity
Point-to-Site VPN
Point-to-Site (P2S) VPN enables individual devices to securely connect to an Azure VNet. This is ideal for remote workers or developers needing secure access.
Key Features:
- Easy setup and deployment.
- Support for multiple authentication methods (e.g., Azure AD, certificates).
Site-to-Site VPN
Site-to-Site (S2S) VPN provides secure, persistent connections between on-premises networks and Azure VNets.
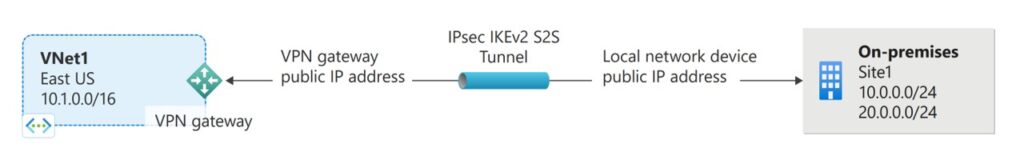
Best Practices:
- Use strong encryption protocols such as AES-256.
- Configure multiple tunnels for redundancy.
- Monitor VPN gateways for performance and security metrics.
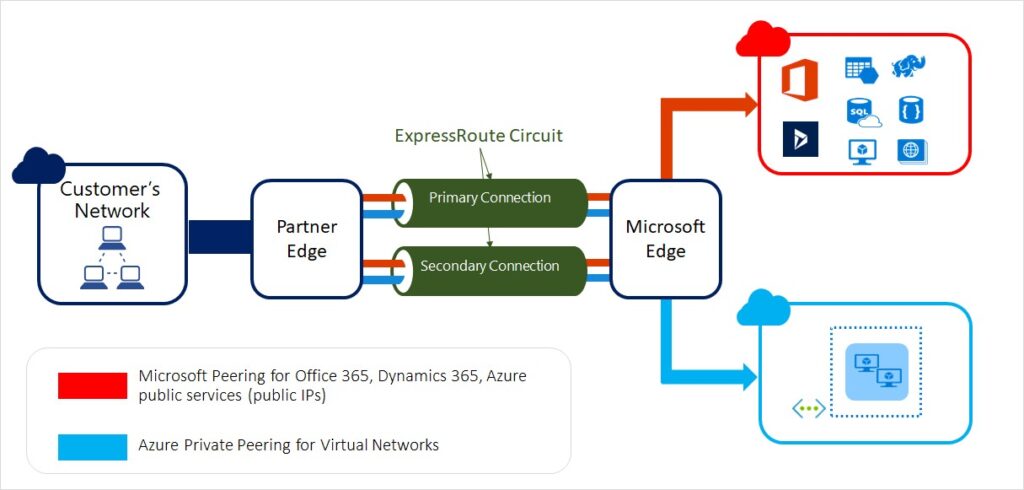
Azure ExpressRoute
Azure ExpressRoute offers private, dedicated connections between Azure data centers and on-premises environments. Unlike VPNs, ExpressRoute doesn’t traverse the public internet, providing greater reliability and security.

Key Advantages:
- Lower latency and higher throughput for mission-critical workloads.
- Secure and consistent connectivity.
- Support for hybrid environments.
Implement Encryption over ExpressRoute
While ExpressRoute connections are inherently private, they are not encrypted by default. For sensitive data, you can implement encryption as an additional security measure:
- IPsec Tunnels: Use IPsec over ExpressRoute for encrypted traffic.
- Application-Level Encryption: Encrypt data before transmission for end-to-end protection.
Tip: Always encrypt sensitive data, even when using private connections.
Monitor Network Security Using Network Watcher
Azure Network Watcher provides tools to monitor, diagnose, and visualize network security.
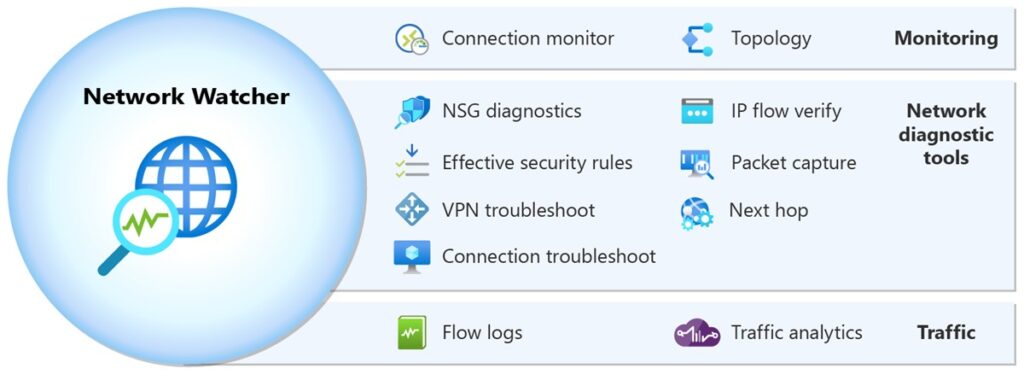
Key Features:
- NSG Flow Logs: Capture and analyze traffic data for NSGs.
- Connection Troubleshoot: Diagnose connectivity issues between resources.
- Topology Viewer: Visualize the structure and dependencies of network resources.
Best Practices:
- Integrate Network Watcher with Log Analytics for centralized monitoring.
- Set up alerts for unusual traffic patterns or unauthorized access attempts.
- Use diagnostic logs to maintain compliance with security policies.
Conclusion
Azure Network Security is essential for protecting your cloud resources from evolving cyber threats. By leveraging tools like VNets, NSGs, ASGs, and ExpressRoute, and by following best practices, you can build a secure, resilient network infrastructure.
Stay tuned for more insights in our 30 Days of Azure Security series!

