If you want to learn about FSMO roles in Active Directory, then you are on right place. Active Directory, the central nervous system of many Windows-based networks, depends on a set of unique roles known as FSMO (Flexible Single Master Operations) roles. In this comprehensive article, we will delve into the intricate world of FSMO roles in Active Directory, understanding what they are, unraveling their importance in Active Directory management, and exploring their significance in maintaining the integrity of network directories.
Table of Contents
What Are FSMO Roles in Active Directory?
Understanding FSMO Roles: FSMO roles, short for Flexible Single Master Operations roles, are specialized positions within Microsoft’s Active Directory that wield significant control over essential functions. These roles serve as the guardians of data integrity, governing operations ranging from schema management to password changes, and play a fundamental role in ensuring the consistency and reliability of Active Directory.
Significance in Active Directory: FSMO roles are the unsung heroes of Active Directory management, ensuring the smooth and secure operation of network directories. By actively managing data consistency, preventing conflicts, controlling directory structure, resolving conflicts, and supporting disaster recovery, they stand as the backbone of a well-functioning Active Directory system.
Types of FSMO Roles in Active Directory
Exploring the Five FSMO Roles in Active Directory:
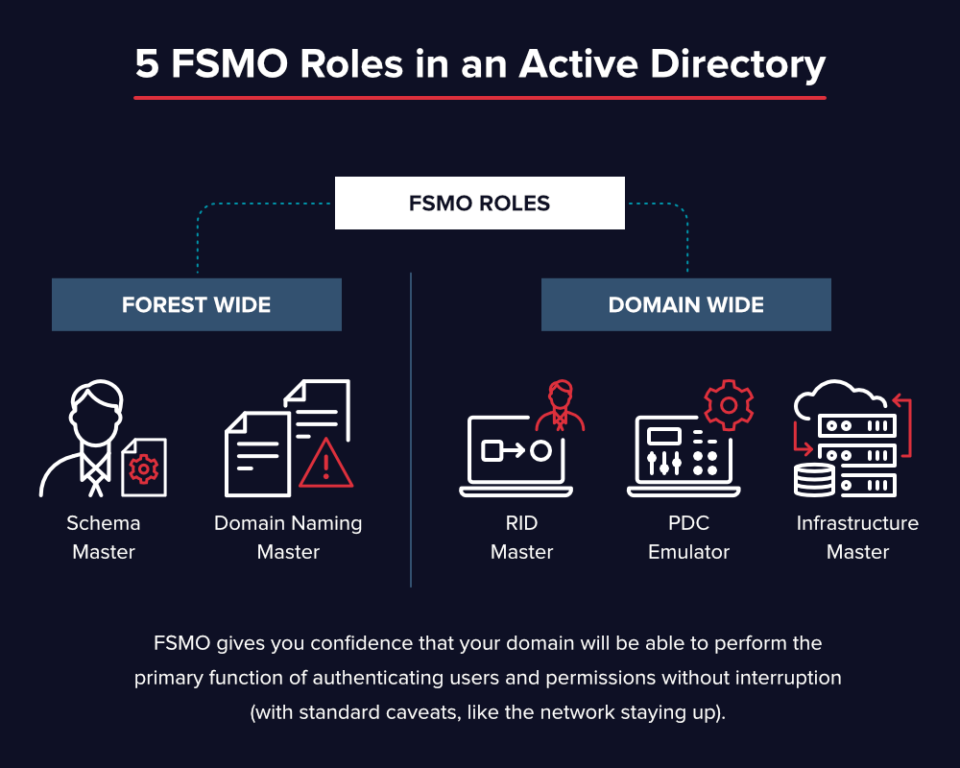
1. Schema Master:
Function: The Schema Master is responsible for managing the Active Directory schema, which defines the structure and attributes of directory objects. It controls changes to the schema, ensuring modifications are controlled and consistent.
Importance: Maintaining the integrity of the schema is crucial as it affects the directory’s overall structure. Unauthorized or inconsistent schema changes can lead to compatibility issues and data corruption.
Issues If Not Working: If the Schema Master is unavailable or not functioning correctly, unauthorized schema changes may occur. For example, an admin might accidentally or intentionally make unauthorized schema modifications, which can disrupt the directory’s structure and consistency.
Troubleshooting: Troubleshooting Schema Master issues involves verifying schema modification permissions, monitoring schema changes, and regularly backing up the schema to facilitate recovery in case of issues.
2. Domain Naming Master:
Function: The Domain Naming Master manages the addition and removal of domains within an Active Directory forest. It ensures that domain names are unique and free from conflicts.
Importance: This role is crucial for maintaining naming consistency across the forest. It prevents naming conflicts and ensures that domains are added or removed with precision.
Issues If Not Working: Without an operational Domain Naming Master, domain naming conflicts may arise. For example, if two administrators independently attempt to create a domain with the same name, it can lead to naming disputes.
Troubleshooting: Troubleshooting Domain Naming Master issues includes ensuring connectivity to the role holder, verifying that it is online, and confirming that domain naming changes are made by authorized administrators.
3. Relative Identifier (RID) Master:
Function: The RID Master allocates unique pools of Relative Identifiers (RIDs) to each domain controller. These RIDs are crucial for generating Security Identifiers (SIDs) for objects.
Importance: The RID Master’s function is essential for preventing SID conflicts. It ensures that each object in Active Directory has a unique SID, maintaining security and data integrity.
Issues If Not Working: If the RID Master becomes inaccessible or fails, SID conflicts can occur. For instance, two objects might end up with the same SID, leading to access issues and security vulnerabilities.
Troubleshooting: Troubleshooting the RID Master involves checking connectivity, verifying the role holder’s functionality, and monitoring the availability of RID pools. Adjusting the pool size may be necessary to prevent pool exhaustion.
4. Primary Domain Controller (PDC) Emulator:
Function: The PDC Emulator role serves a crucial role, particularly in multidomain environments. It emulates the behavior of older Windows NT PDCs. It manages password changes, time synchronization, and specific authentication requests.
Importance: Ensures password changes are processed correctly and maintains accurate time synchronization across the network. These are pivotal for security and authentication.
Issues If Not Working: Without an operational PDC Emulator, password changes may not be correctly processed. Time discrepancies can lead to authentication problems.
Troubleshooting: In case of PDC Emulator issues, verifying time synchronization and the role holder’s operational status is paramount. Investigate replication issues within the domain to resolve authentication problems.
5. Infrastructure Master:
Function: The Infrastructure Master maintains object references between domains, ensuring they are accurate and uptodate.
Importance: Vital for data consistency, particularly in multidomain environments. It prevents data inconsistencies, conflicts, and ensures proper replication.
Issues If Not Working: If the Infrastructure Master encounters issues, it can lead to outdated object references, causing data inconsistencies, conflicts, and issues with replication.
Troubleshooting: Troubleshooting Infrastructure Master problems includes verifying connectivity, ensuring the role holder is operational, and confirming correct configuration of global catalog servers.
Why are FSMO Roles Important?
Impact on Active Directory Operations: FSMO roles play an indispensable role in maintaining data consistency, forestalling conflicts, and controlling crucial network operations. They are the unseen guardians that ensure Active Directory functions seamlessly.
The Consequences of Mismanagement: Mishandling FSMO roles can lead to naming conflicts, data inconsistencies, authentication bottlenecks, and security vulnerabilities. Real-world examples further illustrate the gravity of mismanaging these pivotal roles.
Best Practices for Managing FSMO Roles in Active Directory
1. Role Placement:
Plan Carefully: When initially deploying Active Directory, plan the placement of FSMO roles strategically. Ensure they are distributed across different domain controllers to prevent a single point of failure.
Use Separate Hardware: Whenever possible, consider placing FSMO roles on domain controllers with dedicated hardware resources to optimize their performance.
2. Role Ownership:
Document Ownership: Keep a clear record of which domain controller holds each FSMO role. This documentation is invaluable for troubleshooting and disaster recovery.
3. Role Transfers and Seizures:
Understand Transfer vs. Seizure: Understand the distinction between transferring and seizing FSMO roles. Transferring is the preferred method, as it allows for graceful role migration. Seizing should only be used in disaster recovery scenarios.
Minimize Seizures: Minimize the use of role seizures, as they can lead to data inconsistencies and operational issues if not performed carefully.
4. Monitoring and Alerts:
Implement Monitoring: Use network monitoring tools to keep an eye on the health and status of domain controllers, particularly those holding FSMO roles.
Set Up Alerts: Configure alerts and notifications for FSMO role changes, role holder failures, and other critical events. This ensures timely responses to issues.
5. Regular Backups:
Back Up Roles: Regularly back up the Active Directory database, including the system state. This includes the FSMO roles’ data, allowing for restoration in case of role corruption or data loss.
Test Restores: Periodically perform test restores of the Active Directory to ensure that FSMO role backups are functional and can be used in case of emergencies.
6. Role Transfers:
Plan Role Transfers: When needing to change the role holder, perform role transfers during planned maintenance windows to minimize disruption.
Verify Successful Transfers: After transferring roles, verify that the new role holder is functioning correctly and has replicated the role data.
7. Documentation:
Maintain Documentation: Keep comprehensive documentation of your Active Directory environment, including FSMO role assignments, role holder details, and any related procedures.
8. Disaster Recovery:
Create Disaster Recovery Plans: Develop and regularly test disaster recovery plans for FSMO roles. These plans should cover scenarios such as role-holder failures, data corruption, and role seizure recovery.
9. Security Considerations:
Secure Role Holders: Ensure that FSMO role holders are well secured, with proper access controls and permissions. Unauthorized access to these domain controllers can compromise your network’s security.
10. Regular Auditing:
Audit Changes: Regularly audit and review changes to FSMO roles, especially during personnel transitions or organizational changes.
11. Training and Knowledge Sharing:
Provide Training: Ensure that IT staff responsible for Active Directory management have the necessary training and expertise in FSMO role management.
12. Maintenance Scheduling:
Scheduled Maintenance: Schedule routine maintenance tasks, such as FSMO role checks, backups, and audits, to keep your Active Directory environment in optimal condition.
Tools and Resources
Managing FSMO (Flexible Single Master Operations) roles in Active Directory can be made more efficient with the use of various tools and resources. Here are some essential tools and resources for FSMO role management:
1. Active Directory Users and Computers (ADUC):
Role Management: ADUC is a built in Windows tool for managing Active Directory. It allows you to view and transfer some of the FSMO roles, such as the RID Master, PDC Emulator, and Infrastructure Master.
2. Active Directory Sites and Services:
Transfer Roles: This builtin tool enables you to transfer the Schema Master and Domain Naming Master roles. It’s particularly useful for managing these roles in multidomain environments.
3. PowerShell:
PowerShell Cmdlets: Windows PowerShell provides a set of cmdlets for FSMO role management. You can use commands like “Move ADDirectoryServerOperationMasterRole” to transfer roles.
4. NTDSUTIL:
Command Line Tool: NTDSUTIL is a command line utility for managing Active Directory. It allows for seizing FSMO roles in disaster recovery scenarios. Be cautious when using it, as seizing roles should be a last resort.
5. Active Directory Replication Status Tool:
Replication Monitoring: This tool, provided by Microsoft, helps monitor the replication status of Active Directory, including FSMO role data. It’s useful for ensuring the proper functioning of role replication.
6. AD DS Best Practices Analyzer:
Health Checks: This tool examines the state of your Active Directory environment, including FSMO role management. It provides recommendations for improving the health and performance of your directory.
7. Monitoring and Alerting Solutions:
Network Monitoring Tools: Third party network monitoring solutions can help keep an eye on the health and status of domain controllers and send alerts for critical events, including FSMO role changes and failures.
8. Microsoft Documentation:
Official Resources: Microsoft offers comprehensive documentation on Active Directory and FSMO role management. The official documentation provides guidance on understanding, configuring, and troubleshooting FSMO roles.
9. Online Communities and Forums:
Knowledge Sharing: Online communities and forums, such as Microsoft TechNet and Reddit’s /r/sysadmin, are valuable resources for getting advice, sharing experiences, and finding solutions to FSMO role-related issues.
10. Professional Training and Courses:
Certification Programs: Consider professional training programs and certification courses, such as those offered by Microsoft (e.g., MCSE(Microsoft Certified Solutions Expert)). These programs provide in-depth knowledge of Active Directory and FSMO roles.
11. FSMO Role in Active Directory Management Scripts:
Custom Scripts: Many IT professionals and organizations have developed custom scripts for automating FSMO role management tasks. These scripts can be valuable for simplifying routine role checks and transfers.
12. Disaster Recovery Guides:
Documentation and Guides: FEMA (Federal Emergency Management Agency) and other organizations provide disaster recovery guides and best practices. These can be adapted to create a disaster recovery plan specifically for FSMO roles.
13. Vendor Specific Tools:
Third Party Tools: Some vendors offer tools for Active Directory management and monitoring that include features for FSMO role management. These tools can provide a user-friendly interface and additional functionality.
Utilizing these tools and resources will help you effectively manage FSMO roles in Active Directory, ensure the health and stability of your Active Directory environment, and be prepared for any role related issues or contingencies.
Conclusion
In summary, FSMO roles in Active Directory are the unsung heroes of Active Directory management, ensuring the reliability, security, and continuity of network directories. By understanding and effectively managing these roles, network administrators can safeguard their systems from potential conflicts, data inconsistencies, and security vulnerabilities.
Call to Action
We urge all network administrators and IT professionals to implement best practices in FSMO role management within their Active Directory systems. The proper administration of these roles is not only a best practice but a necessity for maintaining the security and reliability of network directories. For further inquiries, consultations, or assistance, please don’t hesitate to contact us at [contact information]. Your network’s security and integrity are our primary concerns.
You can follow us on LinkedIn and Twitter for Cloud & Cybersecurity updates.
Also read..

