If you are search different types of common attacks in the digital world, your search end here. The internet, which provides convenience, connectivity, and endless options, has become a crucial component of our everyday lives in the rapidly expanding digital landscape. However, these benefits come with a number of online dangers and harmful actions that might endanger your safety and online visibility. This review will examine some of the most prevalent cyberattacks, illuminate the meths that cybercriminals employ to take advantage of weaknesses, and provide advice on how you may safeguard yourself.
Table of Contents
Common Attacks in The Digital World:

Phishing Attacks
Phishing is a type of cyberattack in which bad actors imitate genuine entities in order to fool people into disclosing sensitive information such as login passwords, personal data, or financial information.

Example of a Phishing Attack
Imagine receiving an email that appears to be from your bank, warning you of suspicious activity on your account. The email includes a link urging you to “verify your account” by clicking on it. However, upon clicking, you are redirected to a fraudulent website that mimics your bank’s login page, and any information you enter is captured by the attacker
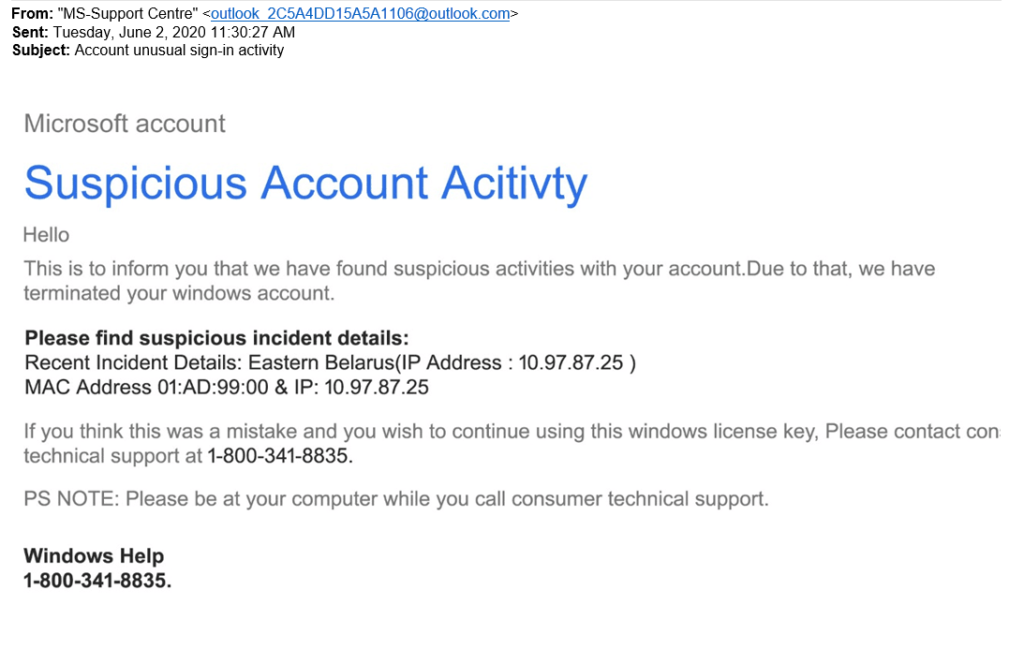
Source: Stanford University
Types of Phishing Attacks:
Spear Phishing: Targeted attacks on specific individuals or organizations, where attackers gather information to craft convincing and personalized phishing messages.
Whaling: A specialized form of spear phishing aimed at high-profile targets, such as CEOs or senior executives.
Vishing: Phishing via phone calls, where attackers impersonate legitimate organizations and attempt to extract sensitive information over the phone.
Smishing: Phishing through SMS or text messages, often containing malicious links or requests for personal information.
Clone Phishing: Attackers duplicate legitimate emails or messages, making minor modifications to deceive recipients into thinking they’re dealing with a trusted source.
Identifying Phishing Attacks
Check the sender’s email: Carefully inspect the sender’s email address for any inconsistencies or unusual domain names.
Look for generic greetings: Phishing emails often use generic salutations like “Dear Customer” instead of your name.
Inspect the URL: Hover over links in emails to view the actual URL; make sure it matches the legitimate website.
Beware of urgency: Phishing emails often create a sense of urgency, pressuring you to take immediate action.
Watch for spelling and grammar mistakes: Poorly written emails are often indicative of phishing attempts.
How to Stay Safe from Phishing Attacks
Verify the sender: Contact the organization directly using official contact information to confirm the authenticity of any suspicious messages.
Never click on suspicious links: Avoid clicking on links in emails or messages unless you are certain of their legitimacy.
Use security software: Keep your antivirus and anti-malware software up-to-date to help identify and block phishing attempts.
Enable Multi-factor authentication (MFA): Implement MFA on your accounts whenever possible to add an extra layer of security.
Report phishing attempts: If you receive a phishing email, report it to your email provider, organization, or relevant authorities.
Use a password manager: Password managers can help generate and store complex, unique passwords for different accounts, reducing the risk of password-related attacks.
Social Engineering Attacks
Cybercriminals employ social engineering attacks to target human psychology rather than technical flaws. These assaults are designed to trick people into disclosing private information, granting illegal access, or taking actions that harm security. To achieve their goals, social engineers frequently play on trust, fear, or curiosity.
Types of Social Engineering
Phishing: Attackers use deceptive emails, messages, or websites that impersonate trusted entities to trick victims into disclosing sensitive information.
Baiting: Cybercriminals offer something enticing, like free software or downloads, to lure victims into downloading malicious software or sharing personal data.
Pretexting: Attackers fabricate a scenario or pretext to extract information or gain trust. They might pose as co-workers or authorities seeking sensitive data.
Tailgating: This physical form of social engineering involves gaining unauthorized access to a secured location by following someone with legitimate access.
Quid Pro Quo: Attackers promise something in return for information or actions, such as offering IT support in exchange for login credentials.
Impersonation: Criminals impersonate trusted individuals or organizations through phone calls, emails, or in-person encounters to manipulate victims into divulging information.
How to Protect ourself from Social Engineering Attacks
Question and Verify: Always question requests for sensitive information or actions, especially if they seem unusual or unexpected. Verify the identity and legitimacy of the requester.
Educate Yourself:Discover the typical tactics employed in social engineering and the warning signs to watch for. Developing awareness serves as your primary means of protection against these manipulative techniques.
Use Strong Authentication: Implement multi-factor authentication (MFA) wherever possible to add an extra layer of security to your accounts.
Protect Personal Information: Avoid oversharing personal details on social media, as attackers can use this information to craft convincing social engineering attacks.
Exercise caution when dealing with links and attachments: Avoid clicking on links or downloading attachments from sources that are unfamiliar or raise suspicion. Take a moment to hover over links to verify the authenticity of the URL.
Verify Requests: If someone asks for sensitive information, such as passwords or financial details, independently verify their identity through official channels.
Don’t Succumb to Pressure: Social engineers often create urgency or fear. Take your time to assess the situation, and don’t make rushed decisions.
Report Suspicious Activity: If you encounter a potential social engineering attempt, report it to your organization’s IT or security team and inform relevant authorities. Stay Informed: Keep up with the latest social engineering trends and share this knowledge with friends and family to protect the wider community.
What is a Virus Attack?
A virus attack, in the context of computers and technology, refers to the infiltration of malicious software known as “viruses” into a computer system. These viruses are designed to replicate themselves and often cause harm by corrupting or destroying data, slowing down the system, or even compromising security.

Types of Viruses:
File Infector Viruses: These attach themselves to executable files and spread when the infected file is executed.
Macro Viruses: These infect documents or files that contain macros, often in office applications like Word or Excel.
Boot Sector Viruses: These target the boot sector of a computer’s hard drive or removable storage, making them active when the system is booted.
Resident Viruses: These embed themselves in a computer’s memory, allowing them to operate even when the infected program isn’t running.
Non-Resident Viruses: These viruses rely on the infected program to be active for them to execute.
Top 10 Most Dangerous Viruses (historical):
ILOVEYOU: Spread through email, it caused extensive damage in 2000.
Conficker: Infected millions of computers worldwide and was particularly challenging to remove.
Mydoom: One of the fastest-spreading email worms, it launched DDoS attacks and affected email servers.
Blaster (MSBlast): Exploited a vulnerability in Microsoft Windows and caused widespread infections.
Sasser: Spread rapidly, targeting Windows XP and 2000 systems.
Slammer (SQL Slammer): Infected thousands of computers within minutes by exploiting a SQL Server vulnerability.
Nimda: Affected web servers and email systems, spreading through multiple methods.
Code Red: Targeted Microsoft IIS web servers and attempted to deface websites.
Storm Worm: Spread through malicious emails and created a large botnet for cybercriminal activities.
Melissa: One of the first major macro viruses, it caused widespread email disruptions in 1999.
How to Stay Safe from Virus Attacks?
Utilize Antivirus Protection: Ensure the installation of reliable antivirus software and maintain regular updates for enhanced security.
Keep Operating Systems and Software Updated: Regularly update your operating system and all software, as updates often contain security patches.
Download from Trusted Sources: Only download software and files from trusted, official sources, and avoid pirated or cracked software.
Be Cautious with Email: Don’t open email attachments or click on links in emails from unknown or suspicious sources.
Activate a Firewall: Enhance your computer’s security by enabling a firewall, which filters both incoming and outgoing network traffic.
Backup Your Data: Regularly back up your important data to an external source to mitigate data loss in the event of an attack.
Avoid Piracy: Do not use pirated or cracked software, as it often comes bundled with malware.
Educate Yourself: Stay informed about common tactics used in virus attacks and be cautious when browsing the internet or downloading files.
Enable User Account Control (UAC): On Windows systems, use UAC to control which changes can be made to your computer by unauthorized software.
Use Strong Passwords: Create strong, unique passwords for your accounts and enable multi-factor authentication (MFA) when possible.
What is a Malware Attack?
A malware attack is a malicious attempt to infiltrate a computer, device, or network with the intent to disrupt, damage, or gain unauthorized access. “Malware” is short for “malicious software,” and it encompasses a wide range of harmful programs that can include viruses, worms, Trojans, ransomware, and more.

Types of Malware:

Viruses: Malicious code that attaches to legitimate files and spreads when those files are executed.
Worms: Self-replicating malware that spreads independently through networks and devices.
Trojans: Deceptive programs that appear legitimate but hide malicious functions.
Ransomware: Encrypts files or locks a user out of their device, demanding a ransom for access or decryption.
Spyware: Secretly collects user data, including keystrokes and browsing habits, often for cybercriminal purposes.
Adware: Displays unwanted advertisements, often as pop-ups, and can lead to compromised privacy.
Rootkits: Stealthy malware that hides in a device’s operating system, making it challenging to detect and remove.
Keyloggers: Records keystrokes to steal sensitive information like passwords.
Botnets: A network of infected devices controlled by a remote attacker for various malicious purposes. Fileless Malware: Malicious code that operates in memory, leaving little to no traces on the hard drive
How to Stay Safe from Malware Attacks?
Utilize Antivirus Protection: Ensure the installation of reliable antivirus software and maintain regular updates for enhanced security.
Regular Updates: Keep your operating system, software, and apps updated to patch security vulnerabilities.
Download from Trusted Sources: Only download software and files from official, reputable websites.
Email Caution: Be wary of email attachments and links, especially from unknown or suspicious sources.
Use a Firewall: Enable a firewall to filter incoming and outgoing network traffic.
Backup Data: Regularly back up important data to an external source to mitigate data loss.
User Awareness: Educate yourself and your family about common malware tactics and threats.
Strong Passwords: Use strong, unique passwords for your accounts, and enable multi-factor authentication (MFA) when available.
Avoid Pirated Software: Steer clear of pirated or cracked software, as it often contains malware.
Exercise Caution: Be cautious while browsing the internet, and don’t click on suspicious pop-ups or links.
What is a Password Attack?

A password attack is a malicious attempt to gain unauthorized access to an individual’s or organization’s accounts, systems, or devices by exploiting weaknesses in password security. Attackers use various techniques to guess, steal, or crack passwords to compromise digital assets.
Types of Password Attacks
Brute Force Attack: Attackers systematically try every possible combination of characters until they find the correct password.
Dictionary Attack: Attackers use a list of common words, phrases, or known passwords to guess the target’s password.
Phishing: Attackers trick users into revealing their passwords through fake login pages or deceptive emails.
Credential Stuffing: Attackers use username-password pairs obtained from previous data breaches to gain unauthorized access to other accounts, assuming users reuse passwords.
Keylogger Attack: Malicious software records keystrokes to capture passwords as users type them.
Rainbow Table Attack: Attackers use precomputed tables of password hashes to quickly crack passwords.
How to Stay Safe from Password Attacks?
Use Strong, Unique Passwords: Create complex, lengthy passwords that combine letters, numbers, and special characters. Avoid using things like your birthday or everyday words that others could easily figure out.
Enable Multi-Factor Authentication (MFA): Whenever possible, enable MFA to add an extra layer of security by requiring a second authentication step, such as a one-time code sent to your phone.
Password Manager: Use a reputable password manager to generate, store, and auto-fill strong, unique passwords for each of your accounts.
Regularly Change Passwords: Change your passwords periodically, especially for critical accounts, like email and banking.
Stay Alert to Phishing: Exercise caution when encountering emails, messages, or websites that request your login information. Confirm the sender’s authenticity and refrain from clicking on any links that seem suspicious.
Check for HTTPS: Ensure websites use HTTPS, which encrypts data transmitted between your browser and the website, protecting your login information.
Monitor Account Activity: Regularly review your account activity for any unauthorized access or suspicious activity.
Stay Informed: Keep up with security news and best practices to stay aware of emerging threats and how to defend against them.
Secure Your Devices: Keep your devices free from malware, as compromised devices can lead to password theft. Use antivirus software and keep your devices updated.
Educate Yourself: Learn about common password attack techniques and share this knowledge with friends and family to protect them as well.
