If you want to know why Splunk reigns supreme in cybersecurity, you have come to the right place. Here, we will try to give satisfactory answers to all your questions. Protecting data against increasing cyber threats is essential in today’s digital world, where it serves as the lifeblood of businesses and organizations. One name continually reigns supreme as the cybersecurity victor in this continuing conflict: Splunk.
Splunk’s dominance isn’t accidental; it’s the product of its extraordinary talents, adaptability, and unwavering dedication to digital security. This article will help you understand why Splunk is the industry leader in cybersecurity.
At its foundation, Splunk is a digital guardian rather than merely a tool. By utilizing the strength of data analysis and real-time monitoring to proactively detect and address threats, it goes beyond conventional cybersecurity tactics. By dissecting Splunk’s capabilities, we can see how strong it is at comprehensive data analysis, real-time insights, and threat detection. By the conclusion, you’ll have a deep understanding of why Splunk is the preferred option for protecting digital assets in today’s dynamic cyber scenario. Welcome to the Splunk universe, where the best in cybersecurity knows no borders.
Table of Contents
Why Splunk Reigns Supreme–The Unique Advantages in Cyber Security
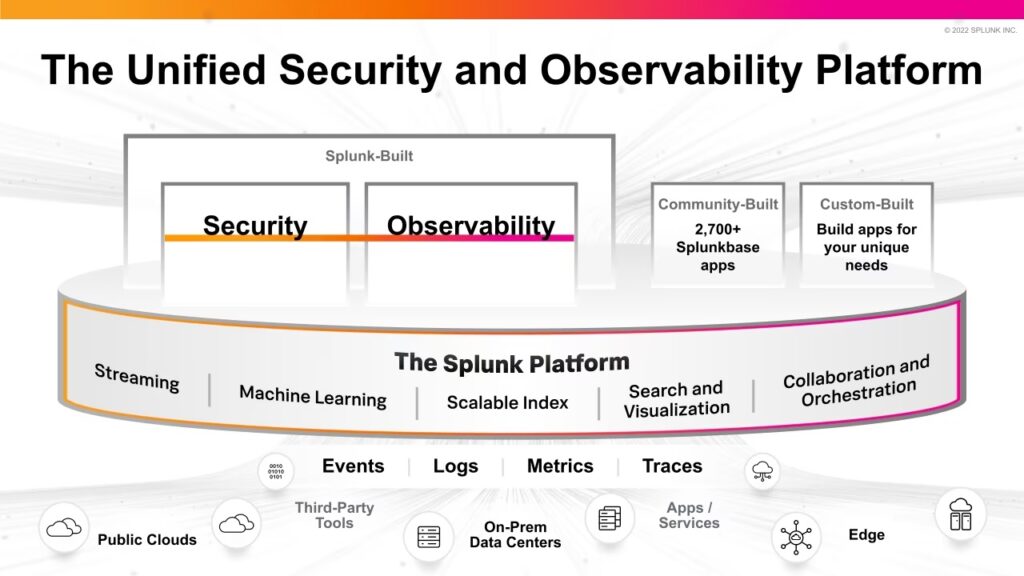
When it comes to defending against cyber threats, Splunk is the undisputed leader. What sets Splunk apart are its unique strengths. Unlike traditional cybersecurity tools, Splunk uses data analysis and real-time monitoring to stay one step ahead of threats.
Splunk stands out as a truly unique and indispensable tool in the field of cybersecurity for several key reasons:
Versatility: Splunk’s ability to ingest, index, and analyze data from virtually any source sets it apart. It thrives on data diversity, making it adaptable to the ever-changing digital landscape.
Real-Time Monitoring: Splunk’s real-time monitoring capabilities provide a proactive shield against threats. It detects anomalies and security incidents as they happen, enabling swift responses to mitigate potential damage.
Correlation Expertise: Splunk excels in connecting the dots. By correlating data from various sources, it uncovers hidden patterns and trends, even in the most complex threats, enhancing threat detection and incident response.
Digital Forensics Powerhouse: In the aftermath of a security incident, Splunk’s search and query capabilities transform it into a digital forensics powerhouse. It aids investigators in reconstructing events, deciphering attack vectors, and preventing future breaches.
Behavior Analytics: Splunk utilizes machine learning to monitor user and entity behavior, identifying abnormal activities indicative of insider threats or compromised accounts. This proactive stance is invaluable for early threat detection.
Seamless Integration: Splunk seamlessly integrates with a multitude of security tools, streamlining operations and automating responses to threats.
Scalability: Whether you’re a startup or a multinational corporation, Splunk scales effortlessly to accommodate your data needs, ensuring optimal performance.
Compliance Simplification: For regulated industries, Splunk simplifies compliance reporting by consolidating and analyzing security-related data, facilitating audits and regulatory adherence. Customization and Community: Splunk’s adaptability allows organizations to tailor it to their unique requirements. Its active user community ensures ongoing support and enhancement. To learn more, click here
How is Splunk better than other tools?
Splunk outshines other tools in cybersecurity and data analysis due to its unmatched versatility, real-time monitoring, and correlation capabilities. Its flexibility allows it to collect and analyze data from diverse sources, offering a comprehensive view of an organization’s environment.
Splunk’s real-time monitoring is a proactive shield against security incidents and anomalies, ensuring swift responses to threats as they emerge. It stands out in threat detection, correlating data to uncover complex and evolving risks, going beyond basic analysis. To learn more about log analysis and monitoring, click here.
In the aftermath of security incidents, Splunk excels as a digital forensics tool, enabling investigators to reconstruct events and understand attack vectors. Leveraging machine learning, it monitors user and entity behavior, aiding in early threat detection.
Splunk’s seamless integration with various security tools streamlines operations and enhances threat response. Its scalability accommodates organizations of all sizes, and compliance reporting is simplified, crucial for regulated industries.
Customization, a vibrant community, and a rich ecosystem further bolster Splunk’s effectiveness. However, achieving its full potential requires proper implementation and ongoing monitoring. Splunk’s comprehensive capabilities make it the top choice for organizations seeking enhanced security and data insights, setting it apart from other tools in the field
Advantages and Disadvantages of Splunk
Advantages of Splunk:
Comprehensive Data Analysis: Splunk can collect and analyze data from a wide range of sources, providing organizations with a holistic view of their IT environment.
Real-Time Monitoring: Splunk offers real-time monitoring, allowing organizations to detect and respond to security incidents and anomalies as they happen.
Correlation and Threat Detection: Splunk’s ability to correlate data from various sources helps in identifying complex and evolving threats.
Digital Forensics: Splunk’s search and query capabilities are invaluable for digital forensics, aiding in incident reconstruction and understanding attack vectors.
User Behavior Analytics: Leveraging machine learning, Splunk can monitor user and entity behavior, identifying abnormal activities that may indicate insider threats.
Integration: Splunk seamlessly integrates with various security tools, streamlining security operations and enabling automated responses to threats.
Scalability: Splunk is scalable, catering to organizations of all sizes and efficiently managing large volumes of data.
Compliance Reporting: For regulated industries, Splunk simplifies compliance reporting, making it easier to demonstrate adherence to regulatory standards.
Disadvantages of Splunk:
Cost: Splunk’s licensing costs can be substantial, particularly for larger organizations or those with extensive data volumes.
Complexity: Implementing and configuring Splunk can be complex, requiring skilled personnel and expertise.
Resource Intensive: Splunk can be resource-intensive, particularly when dealing with large data volumes, which may necessitate substantial hardware resources.
Learning Curve: Splunk has a learning curve, and training may be required for staff to use it effectively.
Overwhelming Data: With vast data sources, Splunk may generate an overwhelming amount of data, leading to information overload if not managed effectively.
Maintenance: Regular maintenance and monitoring are essential to keep Splunk running efficiently and effectively.
Customization: While its flexibility is an advantage, it can also be a disadvantage if not customized correctly, potentially leading to suboptimal performance.
FAQs:

Question: What are the key use cases for implementing Splunk in our organization?
Answer: Splunk is versatile and can be used for various purposes, including cybersecurity, IT operations, application monitoring, and business analytics. Identifying specific use cases helps determine how Splunk aligns with your organization’s goals.
Question: What is the total cost of ownership (TCO) for implementing Splunk, including licensing, hardware, and ongoing maintenance?
Answer: Understanding the TCO is crucial. It involves licensing fees, hardware costs, and ongoing expenses. Budget considerations are essential to ensuring sustainability.
Question: What level of expertise and resources will we need to effectively implement and manage Splunk?
Answer: Splunk can be complex to set up and maintain. Assessing the required skill sets and resources helps in planning and ensuring successful implementation.
Question: How does Splunk integrate with our existing IT infrastructure and security tools?
Answer: Compatibility and integration are vital. Knowing how Splunk fits into your existing technology stack and its ability to work with other tools streamlines operations and enhances effectiveness.
Question: What are the scalability options with Splunk, and how well does it accommodate our organization’s growth?
Answer: Scalability is key. Ensure Splunk can handle your current data volumes and growth projections without compromising performance or incurring substantial additional costs.

