Table of Contents
Introduction: The Need for Security Automation in Azure
Security is no longer a static process—it requires continuous monitoring, adaptation, and automation. Organisations leveraging Microsoft Azure must proactively defend against evolving cyber threats, misconfigurations, and compliance risks. Manual security management is error-prone and inefficient, making automation an essential component of modern cybersecurity frameworks.
Azure provides a suite of automation tools, including PowerShell scripting and Azure Policy, which enable organisations to enforce security best practices, streamline compliance, and mitigate risks without constant human intervention. This blog post explores why automation is critical, how to implement it using PowerShell and Azure Policy, and best practices for securing cloud environments efficiently.
Why Automate Azure Security?
Security automation offers multiple benefits to cloud administrators and security teams:
- Consistency – Uniform security policies across all resources, reducing configuration drift.
- Efficiency – Automation eliminates tedious manual security tasks, freeing IT teams for strategic initiatives.
- Proactive Defense – Security automation detects misconfigurations, vulnerabilities, and threats before attackers exploit them.
- Continuous Compliance – Helps organisations adhere to security benchmarks like ISO 27001, NIST, CIS, and industry regulations.
Real-World Security Automation Use Cases
Imagine an Azure security administrator responsible for protecting a company’s cloud infrastructure. Without automation, this professional would need to:
- Manually audit Role-Based Access Control (RBAC) settings to prevent privilege escalation.
- Regularly verify that Multi-Factor Authentication (MFA) is enforced across users.
- Ensure that storage encryption is applied to all resources.
Instead of repetitive manual verification, automation via PowerShell & Azure Policy ensures these critical security configurations are enforced automatically, significantly reducing security gaps and administrative overhead.
Using PowerShell to Automate Azure Security
PowerShell is a powerful scripting language used by IT administrators to manage Azure resources programmatically. When used effectively, it automates security operations, ensuring that configurations remain consistent, scalable, and secure.
1️. Enforcing Multi-Factor Authentication (MFA) Across Users
MFA is a critical security control that prevents unauthorized account access. Using PowerShell, we can audit and enforce MFA policies.
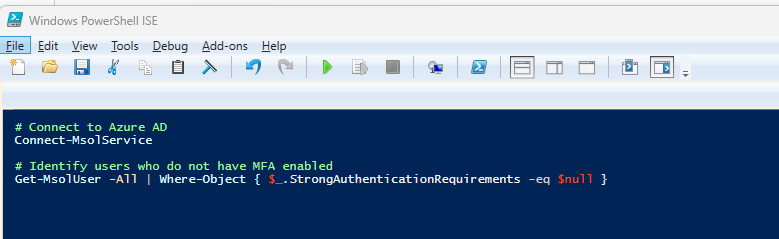
Automation Benefit: This script ensures MFA enforcement, preventing attackers from gaining access with compromised credentials.
2️. Automating RBAC Audits to Prevent Excessive Permissions
Role-Based Access Control (RBAC) defines who can perform actions on Azure resources. Misconfigurations in RBAC assignments can expose systems to privilege escalation risks.
Use PowerShell to audit RBAC assignments and identify unnecessary permissions:

Automation Benefit: Ensures that users, groups, and services only have the minimum required privileges, reducing attack surface.
3️. Deploying Security Baselines Automatically
Security baselines ensure that critical settings—such as encryption, network access rules, and log monitoring—are applied consistently.
Example: Force HTTPS on all Azure Storage Accounts
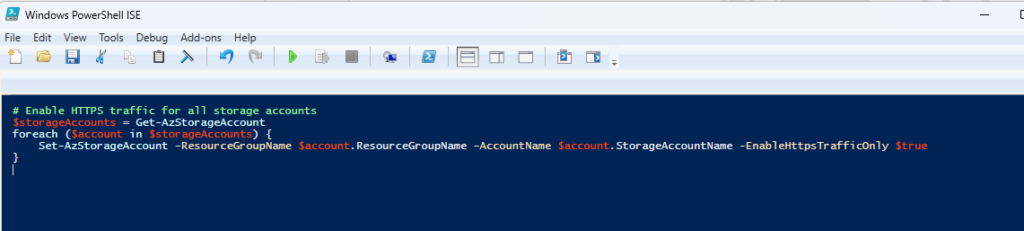
Automation Benefit: Strengthens data security by enforcing encrypted connections, protecting against man-in-the-middle attacks.
Using Azure Policy for Continuous Compliance Enforcement
Azure Policy allows administrators to define and enforce security rules automatically. Unlike PowerShell, which executes scripts on-demand, Azure Policy works continuously, evaluating resources to ensure compliance.
Key Benefits of Azure Policy
🔹 Prevents misconfigurations before they happen.
🔹 Provides centralized compliance reporting.
🔹 Automatically remediates policy violations.
Example: Enforcing Storage Account Encryption Using Azure Policy
Without automation, some users might forget to enable encryption when creating Azure Storage accounts, introducing vulnerabilities. Azure Policy ensures that only encrypted storage accounts are allowed.
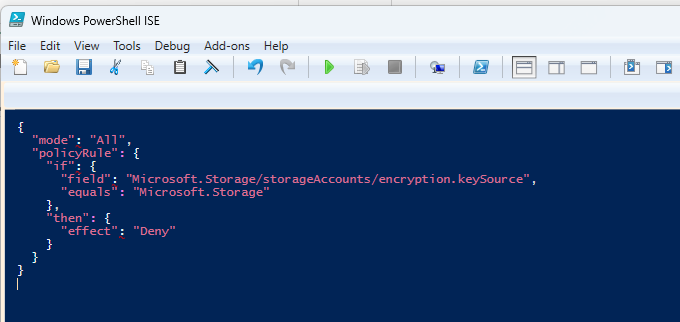
Automation Benefit: Prevents non-compliant storage accounts, ensuring data security is maintained across the organization.
Combining PowerShell & Azure Policy for Maximum Security Automation
How They Work Together:
✅ PowerShell automates security tasks proactively, such as monitoring MFA usage and enforcing RBAC policies.
✅ Azure Policy ensures continuous compliance, preventing misconfigurations from being introduced.
Security Automation Example Workflow:
- PowerShell scans RBAC permissions, highlighting high-risk roles.
- Azure Policy enforces privileged access restrictions automatically.
- PowerShell enables encryption on storage accounts, ensuring secure defaults.
- Azure Policy blocks storage accounts that fail encryption standards.
🚀 Result: A self-healing security framework that minimizes human error and protects Azure resources automatically.
Best Practices for Azure Security Automation
To maximize security automation benefits, organizations should:
- Implement Least Privilege Access – Avoid unnecessary permissions via PowerShell & RBAC audits.
- Define Custom Azure Policies – Tailor policies to your organizational security needs.
- Integrate Security Automation into CI/CD Pipelines – Scan infrastructure as code (IaC) before deployment.
- Monitor & Adapt Automation Policies Regularly – Security evolves, so automation should be continuously optimized.
Final Thoughts: The Future of Automated Azure Security
Security automation in Azure is not just an option—it’s a necessity. By combining PowerShell’s proactive automation capabilities with Azure Policy’s continuous compliance enforcement, organizations create a resilient security ecosystem that minimizes threats before they escalate.
🚀 The time for manual security management is over—embrace automation to safeguard your cloud workloads efficiently!
🔹 Are you using automation in your Azure security strategy? Share your insights in the comments!
Stay tuned for more insights in our 30 Days of Azure Security series!

