As organizations increasingly migrate to the cloud, managing access to resources effectively becomes paramount. Microsoft Azure offers Role-Based Access Control (RBAC) as a powerful tool to manage who has access to what resources, ensuring security and operational efficiency. This guide provides a detailed overview of Azure RBAC, breaking down its components and functionality with practical examples.
Table of Contents
What is Azure Role-Based Access Control (Azure RBAC)?
Azure RBAC is a system that provides fine-grained access management for Azure resources. It allows organizations to define roles and assign them to users, groups, and applications to grant or restrict access to specific resources. By adhering to the principle of least privilege, Azure RBAC helps ensure that users only have the permissions they need to perform their tasks.
What Can I Do with Azure Role-Based Access Control (RBAC)?
Azure RBAC enables you to:
- Grant Least Privilege Access: Assign only the permissions users need to perform their jobs. This minimizes the risk of accidental or malicious changes.
- Control Access Scope: Assign permissions at the appropriate scope:
- Subscription: Access to all resources within the subscription.
- Resource Group: Access to resources within a specific resource group.
- Resource: Access to a specific resource.
- Support Separation of Duties: Assign roles to different individuals or groups based on their responsibilities (e.g., administrators, developers, and auditors).
- Audit and Monitor Access: Use Azure Activity Logs to track changes made by users with their assigned roles.
- Temporary Access with Privileged Identity Management (PIM): Grant time-bound and just-in-time (JIT) access to Azure resources
Example 1: Managing Access for Developers
Scenario:
A team of developers needs access to deploy and manage web applications in Azure App Service within a specific resource group but should not manage resources outside it.
Solution:
- Assign the Contributor role at the Resource Group level to the developer group.
- This allows them to create, update, and delete resources within the resource group but prevents access to other resources in the subscription.
Example 2: Limiting Access to Storage Accounts
Scenario:
An organization wants a finance team to read billing data stored in a storage account but does not want them to modify or delete it.
Solution:
- Assign the Storage Blob Data Reader role to the finance team at the Storage Account level.
- The team can view and download data but cannot delete or upload files.
Example 3: Managing Monitoring Access
Scenario:
An organization’s security team needs to monitor the logs and metrics of Azure resources but should not modify any configuration.
Solution:
- Assign the Reader role at the Subscription level to the security team.
- This provides read-only access to view resources and monitoring data but restricts changes.
Example 4: Temporary Elevated Access
Scenario:
A database administrator needs temporary access to perform maintenance on an Azure SQL Database.
Solution:
- Use Azure AD Privileged Identity Management (PIM) to assign the SQL DB Contributor role for a limited time.
- This ensures the administrator’s elevated access is revoked after the maintenance window.
How Azure Role-Based Access Control (RBAC) Works
Azure Role-Based Access Control (Azure RBAC) works by granting users, groups, or applications specific roles at a particular scope, allowing them to perform only the actions permitted by their assigned role. It uses a deny-by-default model, meaning users must explicitly be granted permissions to access Azure resources.
Key Components of Azure Role-Based Access Control
Roles:
A role is a collection of permissions.
Examples:
- Owner: Full access, including delegation.
- Contributor: Manage resources but cannot grant access.
- Reader: View resources but cannot make changes.
Scope:
Defines where access applies.
Examples:
- Management Group
- Subscription
- Resource Group
- Resource
Role Assignment:
Links a security principal (user, group, or service principal) to a role at a scope.
Example: Assign the Contributor role to a user at the resource group level.
Example 1: Assigning a Developer Role to a Resource Group
Scenario:
A developer named Alex needs to manage virtual machines (VMs) in a resource group called DevResources.
Steps:
- Assign the Contributor role to Alex for the
DevResourcesresource group. - Alex can:
- Create, update, and delete VMs in the
DevResourcesgroup.
- Create, update, and delete VMs in the
- Alex cannot:
- Access VMs in other resource groups or the subscription-level settings.
Example 2: Reader Role for Monitoring
Scenario:
The operations team needs to monitor logs and metrics for all resources in a subscription but should not modify them.
Steps:
- Assign the Reader role to the operations team at the subscription level.
- The team can:
- View resource configurations, logs, and metrics.
- The team cannot:
- Stop, delete, or modify resources.
Example 3: Using Custom Roles for Specific Permissions
Scenario:
A finance team needs to download invoices from a storage account but should not view other data.
Steps:
- Create a custom role with the following action:
Microsoft.Storage/storageAccounts/listKeys/actionMicrosoft.Storage/storageAccounts/read
- Assign this role to the finance team for the storage account.
- The team can:
- List and read storage account details to access invoices.
- The team cannot:
- Modify or delete any storage account data.
Real-World Mechanism of Azure Role-Based Access Control
Scope Inheritance: If a role is assigned at a higher level, it propagates downward.
Example: A role assigned at the subscription level applies to all resource groups and resources within it unless overridden.
Overriding Access: A more specific scope assignment overrides a broader scope.
Example: Assigning a Reader role at the subscription level and a Contributor role at the resource group level grants contributor access to that resource group only.
Explicit Denials: If there is a deny assignment (available in Azure Blueprints), it takes precedence over allow assignments.
Real-World Benefits
- Simplified Management: Assign roles once and let Azure handle scope inheritance.
- Least Privilege Principle: Reduce risk by limiting permissions to exactly what’s required.
- Auditability: Easily track who has access to what through Azure logs.
Groups and Multiple Role Assignments
Role assignments are transitive for groups, which means that if a user is a member of a group and that group is a member of another group that has a role assignment, the user has the permissions in the role assignment.

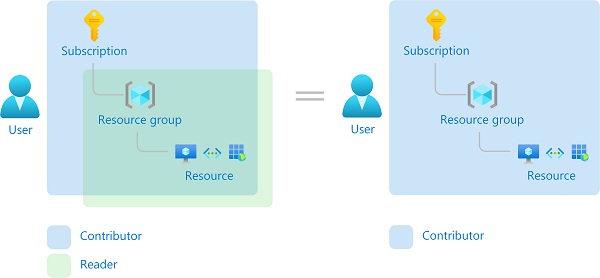
So what happens if you have multiple overlapping role assignments? Azure RBAC is an additive model, so your effective permissions are the sum of your role assignments. Consider the following example where a user is granted the Contributor role at the subscription scope and the Reader role on a resource group. The sum of the Contributor permissions and the Reader permissions is effectively the Contributor role for the subscription. Therefore, in this case, the Reader role assignment has no impact.
How Azure Role-Based Access Control Determines Access
When a user attempts to access a resource, Azure RBAC checks:
- Role Assignments: Does the user have a role assignment for the resource?
- Role Permissions: Does the role include the necessary permissions for the action?
- Scope: Does the scope of the role assignment cover the resource?
Example:
- User: Alice
- Role: Contributor
- Scope: Resource group “RG1”
- Action: Delete a virtual machine in “RG1”
- Result: Access granted because Alice’s role and scope include the required permission.
Where is Azure Role-Based Access Control Data Stored?
Role definitions, role assignments, and deny assignments are stored globally to ensure that you have access to your resources regardless of the region you created the resource.
When a role assignment or any other Azure RBAC data is deleted, the data is globally deleted. Principals that had access to a resource via Azure RBAC data will lose their access.
Why is Azure RBAC Data Global?
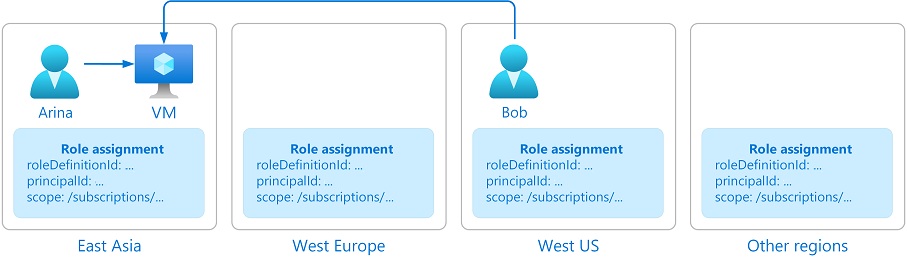
Azure RBAC data is global to ensure that customers can timely access resources regardless from where they’re accessing. Azure RBAC is enforced by Azure Resource Manager, which has a global endpoint and requests are routed to the nearest region for speed and resilience. Therefore, Azure RBAC must be enforced in all regions and the data is replicated to all regions. For more information, see Resiliency of Azure Resource Manager.
Consider the following example. Arina creates a virtual machine in East Asia. Bob, who is a member of Arina’s team, works in the United States. Bob needs to access the virtual machine that was created in East Asia. To grant Bob timely access to the virtual machine, Azure needs to globally replicate the role assignment that grants Bob access to the virtual machine from anywhere Bob is.
License Requirements
Azure RBAC functionality is included in all Azure subscriptions. However, certain features, like advanced management of Azure AD groups or Privileged Identity Management (PIM), may require premium Azure AD licenses (P1 or P2).
Practical Implementation Example
Let’s walk through a real-world scenario:
- Requirement: A project manager needs to view billing information but not make any changes.
- Solution:
- Security Principal: User (Project Manager)
- Role Definition: “Reader”
- Scope: Subscription
- Implementation Steps:
- Assign the “Reader” role to the Project Manager at the subscription level.
- Validate the access by ensuring the user can view billing information but cannot modify resources.
Conclusion
Azure Role-Based Access Control is a critical tool for managing access in a secure and scalable way. By understanding its components and functionality, organizations can enforce the principle of least privilege and ensure compliance. With proper implementation, Azure RBAC not only strengthens security but also simplifies management for Azure environments.
For more information, explore the official Azure documentation.
Stay tuned for more insights in our 30 Days of Azure Security series!

