Welcome to Day 1 of Azure Security! This blog series is here to help you explore Azure Security Fundamentals alongside the essential tools, concepts, and best practices needed to safeguard your Azure environment. Whether you’re an IT Engineer, Cloud Security Engineer, or Cybersecurity Engineer, this journey will deepen your understanding of Azure’s powerful security capabilities.
Did you know that over 90% of security breaches can be prevented with the right cloud security measures? As organizations increasingly migrate to the cloud, the need for robust security becomes critical. Azure provides a comprehensive security framework that acts as a vigilant guardian, defending against ever-evolving cyber threats. From identity management to threat detection, Azure combines intelligent, adaptive systems with automation to keep your digital assets safe while maintaining operational flexibility. However, leveraging these tools effectively requires a clear understanding of Azure’s shared responsibility model and how its services align with your organization’s security strategy.
Table of Contents
Identity and Access Management
Azure Active Directory
Azure AD delivers comprehensive identity management through SSO and RBAC capabilities. It seamlessly handles user authentication, enabling hybrid identity scenarios that bridge on-premises and cloud environments.
Multifactor Authentication
MFA adds critical protection beyond passwords by requiring multiple verification factors for access. It’s especially vital for privileged accounts with elevated permissions, forming a robust defense against unauthorized access attempts.
Conditional Access
Smart policies in Azure AD dynamically control resource access based on contextual factors like location and device health. These rules can trigger MFA prompts or block access when suspicious activity is detected.
Resource Access Management
Assigning permissions to AD groups instead of individual users streamlines access control and reduces security risks. This approach simplifies both granting and revoking access as roles change within the organization.
Zero Trust Architecture
Authentication and Authorization
Azure’s Zero Trust framework validates every access request by analyzing multiple data points including user identity, device status, and geolocation. This comprehensive verification approach treats all requests as potentially malicious, regardless of their origin.
Just in Time Access
JIT/JEA principles minimize security risks by granting temporary, limited scope permissions. Azure Privileged Identity Management implements these controls, ensuring users receive only necessary access for specific durations.
Network Protection
Implementing network segmentation through subnets and virtual networks reduces the potential attack surface. Combined with robust encryption for data both at rest and in transit, this creates multiple layers of defense against security breaches. Azure’s network security groups and private endpoints further strengthen this security model.
Network Security
Network Security Group Rules
NSG rules form the backbone of Azure traffic control, requiring regular review to maintain alignment with organizational security requirements. These configurable filters manage both inbound and outbound network traffic based on IP addresses, ports, and protocols.
Secure Virtual Networks
VNets provide isolated environments for Azure resources through robust subnet segmentation. Private endpoints enable secure resource communication without public internet exposure, while Azure Firewall integration adds advanced threat protection capabilities.
VPN and ExpressRoute Connectivity
Secure hybrid connectivity demands strong IPsec encryption and granular access controls for VPN and ExpressRoute connections. Regular monitoring ensures these pathways remain protected, while automated maintenance routines prevent security gaps from emerging.
Data Protection
Encryption
Azure offers comprehensive encryption solutions for safeguarding data both at rest and in transit. Through Azure Storage encryption and Azure Disk Encryption, organizations can protect sensitive information using industry standard protocols. Azure Key Vault securely manages encryption keys, ensuring controlled access to protected data.
Secure Backup Processes
Azure Backup and Azure Site Recovery enable robust data protection through automated backup procedures. Regular testing of backup and recovery processes ensures business continuity and data resilience in the face of potential incidents.
Data Access Audits
Azure Monitor and Azure Sentinel provide real time visibility into data access patterns through detailed logging and analytics. These powerful monitoring tools enable swift detection of unauthorized access attempts and ensure compliance with security protocols through comprehensive audit trails.
Application Security
Secure Coding Practices
Integrating security into Azure DevOps CI/CD pipelines ensures application safety from development through deployment. Automated code reviews, static analysis, and compliance checks safeguard against vulnerabilities before they reach production environments.
Web Application Firewall
Azure WAF delivers robust protection against common web exploits through intelligent HTTP traffic monitoring. When integrated with Azure Front Door and Application Gateway, it effectively blocks SQL injection, cross site scripting, and other sophisticated attacks targeting web applications.
Vulnerability Testing
Regular automated and manual penetration testing identifies potential security gaps in web applications and APIs. Azure DevOps scanning tools combined with third party security assessments provide comprehensive vulnerability detection, enabling rapid remediation of potential threats before exploitation.
Monitoring and Threat Detection
Continuous Monitoring Tools
Azure Security Center and Azure Sentinel work together to provide comprehensive security oversight. These platforms deliver unified security management through real time monitoring, automated threat detection, and advanced analytics capabilities that protect your cloud infrastructure.
Alerts and Notifications
Smart alert systems detect potential security threats through pattern analysis and behavioral monitoring. Customizable notification rules ensure security teams receive instant alerts about suspicious activities, enabling rapid response to emerging threats across the Azure environment.
Incident Response Planning
Effective incident management requires well documented response procedures and regular team training. Through systematic planning and routine security drills, organizations maintain readiness for security incidents while continuously refining their response strategies to address evolving threats in the cloud landscape.
Compliance and Governance
Azure Policy Management
Azure policies enable robust security governance through automated enforcement of organizational standards. Regular policy reviews ensure alignment with evolving compliance requirements while maintaining strict security controls across cloud resources.
Azure Compliance Manager
The centralized compliance dashboard streamlines regulatory adherence through comprehensive monitoring capabilities. It integrates seamlessly with Azure Policy to provide real time visibility into compliance status, helping identify and remediate potential gaps in security posture.
Audit Trail Maintenance
Leveraging Azure Monitor’s advanced logging capabilities ensures comprehensive tracking of all system changes and access attempts. These detailed audit trails support compliance requirements while providing critical insights for security investigations and regulatory reporting.
Security Controls and Tools
Azure Security Center
Azure Security Center delivers unified security management across your cloud infrastructure. Its advanced threat detection capabilities and vulnerability assessment tools provide comprehensive protection while offering actionable security recommendations to strengthen your environment.
Azure Sentinel

As a cloud native SIEM and SOAR solution, Azure Sentinel aggregates security data from multiple sources. It leverages AI powered analytics to detect threats and automates incident response workflows, enabling security teams to focus on critical investigations rather than routine tasks.
Azure Defender
Azure Defender provides advanced threat protection against sophisticated cyberattacks and malicious insider activities. Its integrated security controls safeguard virtual machines, databases, and storage accounts through continuous monitoring and adaptive protection mechanisms that evolve with emerging threats.
Continuous Monitoring and Maintenance
Microsoft Defender for Cloud
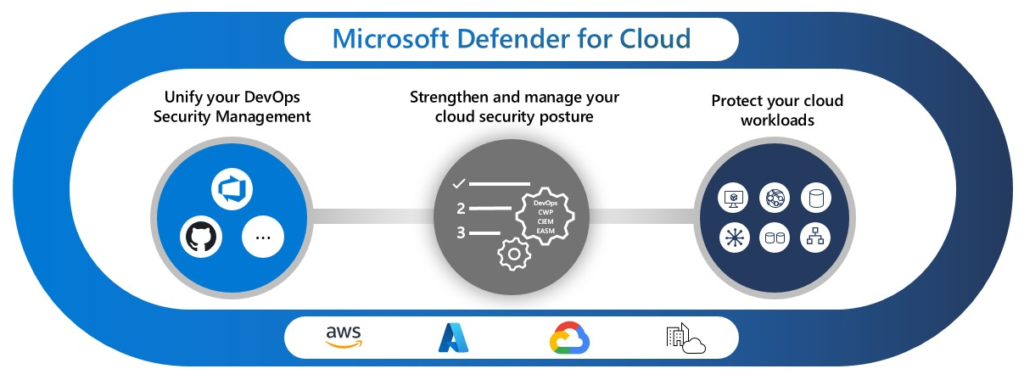
Microsoft Defender for Cloud delivers comprehensive security monitoring across Azure environments. Through automated security assessments, it generates a secure score that reflects your current protection level and highlights areas needing improvement. This dynamic scoring system helps prioritize security enhancements while tracking progress over time.
Threat Detection Exercises
Regular penetration testing and red team activities strengthen Azure infrastructure resilience. These simulated attacks uncover potential vulnerabilities and validate existing security controls. By conducting routine security drills, organizations can test their defense mechanisms, improve response procedures, and ensure their cloud environment remains protected against evolving cyber threats.
Training and Awareness
Cloud Security Education
Effective security starts with comprehensive training on Azure cloud environments. Team members’ need thorough understanding of context based security principles, access controls, and threat detection. Regular workshops and hand son sessions help reinforce best practices while keeping staff updated on emerging security challenges.
Security Posture Management
Maintaining strong security oversight requires continuous assessment and improvement. Organizations must establish clear security metrics, conduct regular audits, and implement robust monitoring protocols. This proactive approach ensures Azure environments remain protected through systematic evaluation of security controls, vulnerability management, and compliance verification. Regular security assessments help identify potential weaknesses before they can be exploited.
Resource Management
Resource Utilization
Optimizing Azure service usage plays a crucial role in maintaining robust security. Shutting down unused services not only reduces costs but significantly minimizes the potential attack surface. Regular resource audits help identify and deactivate idle services, ensuring a lean and secure cloud environment.
Resource Group Security
Implementing resource locks provides essential protection against accidental or unauthorized deletions. Azure offers multiple lock levels, including read only and delete locks, to safeguard critical resources. These protection mechanisms ensure business continuity by preventing unintended changes to vital cloud infrastructure. Regular review of lock configurations maintains the integrity of resource groups while supporting operational flexibility.
Securing Your Azure Future
Building a robust Azure security infrastructure requires a holistic approach that combines technical controls with human expertise. By implementing the comprehensive security measures outlined above, organizations can create a resilient defense system that adapts to emerging threats while maintaining operational efficiency.
What’s Next?
Today, we laid the foundation for understanding Azure security. In Day 2, we’ll delve into Azure Identity and Access Management (IAM), exploring how to manage users, roles, and policies effectively.
Engage With Us
If you have questions or want to share your thoughts, drop them in the comments below. Let’s make Azure a safer cloud together!
Stay tuned, and see you tomorrow for Day 2 of Azure Security! 🌟

